Asymmetric vs. Symmetric Encryption: What are Differences?
Hackers and other cybercriminals are more prevalent than ever today, affecting millions of customers. We must encrypt everything to prevent these criminals from taking our info. Fortunately, you can use two alternative encryption techniques: symmetric and asymmetric.
Look at the overview of encryption before focusing on symmetric and asymmetric encryption.
What is Encryption?
When a communication is sent across a network using encryption, the sender converts the original data into a different format. We may send, receive, and store data more securely with its assistance. It helps secure the data we send, receive, and maintain. Data includes text messages saved to our cell phones, activity logs saved to our fitness trackers, and financial information transmitted by your online account.
It involves taking regular text, like that in a text message or email, and converting it into “cipher text,” an unreadable format. When the recipient accesses the message, a process known as decryption converts the ciphertext back into its initial form. It assists in securing digital data stored on or spread through a network, such as the internet, on computer systems.
Let’s understand the main differences between symmetric and asymmetric encryption.
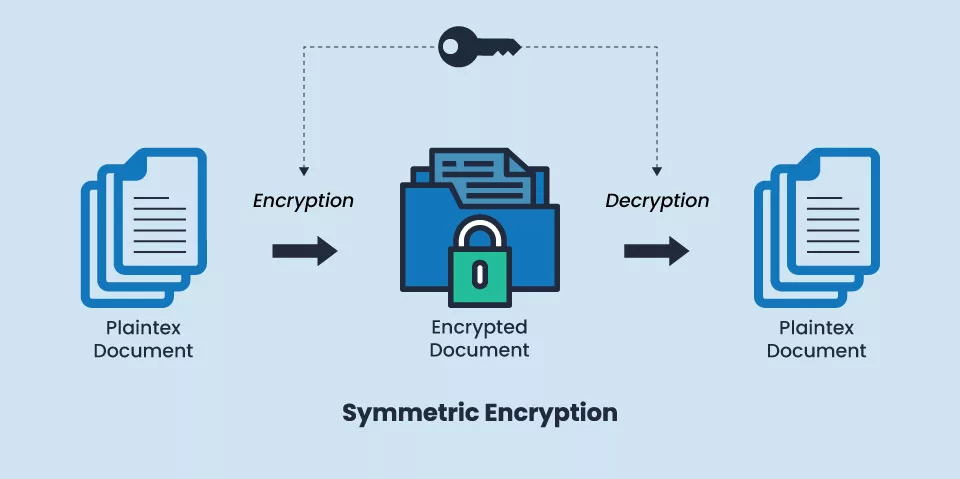
What is Symmetric Encryption?
A popular data encryption method known as symmetric encryption encrypts and decrypts data using a single, secret cryptographic key. The key is specifically used to encrypt plaintext, the data’s pre-encryption or post-decryption state, and decrypt ciphertext – the data’s post-encryption or pre-decryption state.
One of the oldest and most used encryption methods, symmetric encryption has roots in the Roman Empire. Caesar’s cipher, so named because none other than Julius Caesar used it to encrypt his military correspondence, is a renowned historical instance of symmetric encryption in action.
Securing sensitive data is the primary objective of symmetric encryption. It is regularly used in many vital areas, including defense, aerospace, finance, health care, and others, where protecting an individual’s or organization’s sensitive data is most important.
How does Symmetric Encryption Work?
Data is encrypted and decrypted using a block or stream cipher in symmetric encryption. A block cipher uses a fixed key length, such as 128, 192, or 256 bits, to convert whole units or blocks of plaintext, whereas a stream cipher turns plaintext into ciphertext one byte at a time.
Both senders and recipients using symmetric encryption to transfer data to one another must know the secret key to allow senders to encrypt the data they want to share with recipients and for the recipients to decrypt and read the encrypted data the senders share with them, as well as to encrypt all required responses.
However, symmetric encryption is not restricted to data transmission between a single sender and recipient. Anyone can access information that is symmetrically encrypted.
Symmetric Encryption Examples
The following are famous examples of symmetric encryption:
- Data Encryption Standard (DES)
- Triple Data Encryption Standard (Triple DES)
- International Data Encryption Algorithm (IDEA)
- Advanced Encryption Standard (AES)
- TLS/SSL Protocol
Advantages of Symmetric Encryption
Rapid:
It takes less time to run since it only needs one key for encryption and decryption.
Identity Verification:
As a security measure, it uses password authentication to verify the receiver’s identity.
Simple to Manage:
It is effortless since users only need one key for encryption and decryption.
Security:
It would take billions of years for brute-force attempts to penetrate symmetric encryption algorithms like AES.
Industry Use and Acceptance:
Due to the security and speed benefits offered by symmetric encryption algorithms like AES, they have long been accepted in the industry and have become the pinnacle of data encryption.
Disadvantages of Symmetric Encryption
- Transferring keys with symmetric encryption is challenging and complicated, which reduces the probability of secure key sharing.
- Data that is encrypted with a key is compromised if it is lost.
- Since it is unsuitable for different users, symmetric could be more scalable.
Recommended: Hashing VS Encryption
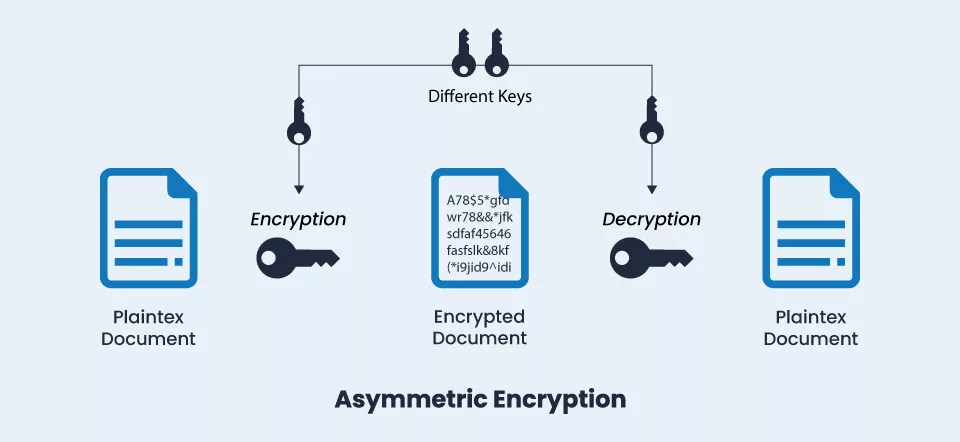
What is Asymmetric Encryption?
In an encrypted communication, two parties are involved: the sender and the recipient. Asymmetric encryption, as the name suggests, uses two separate keys for the sender and the recipient. Only the private key can be used to decode data encrypted with the public key, which is used in asymmetric encryption, also called public key encryption.
In simple terms, asymmetric encryption, also referred to as public-key encryption or public-key cryptography uses effective mathematically linked public as well as private-key pairs to encrypt and decrypt sensitive data for senders and recipients as compared to symmetric encryption, which uses the same secret key for both operations.
Plaintext is still changed into ciphertext during encryption and decryption, just like with symmetric encryption. The primary difference is that data is encrypted asymmetrically using two key pairs.
How does Asymmetric Encryption Work?
Let’s use a hypothetical scenario to make explicit asymmetric encryption.
Imagine that you are mailing your significant other a box of priceless jewellery and want to secure it. Use a unique lock that requires two number combinations to keep it secure while in transit. You have a number that can lock the box, and the receiver has a combination of numbers to unlock it.
You start by placing the things within the box you want to protect. After that, you lock the box using a specific combination of numbers before mailing it. Once it’s there, your partner uses her combination of numbers to open the box and get to the items within. She never gives the number to anyone and keeps it to herself, so nobody else can use it.
Let’s use this concept to comprehend asymmetric encryption concerning public critical infrastructure.
Every bit of information you transfer over the internet is in plaintext. It can therefore be read and understood by anybody with access to it. Of course, you can now encrypt the data with a private key.
You cannot use the same key to decode data once it has been converted into ciphertext. Only the appropriate private key could decipher the ciphertext. Generally, both the sender and the receiver need to have the appropriate private key, and both must have access to the public key.
Asymmetric Encryption Examples
The following are famous examples of asymmetric encryption:
- Rivest Shamir Adleman (RSA)
- Elliptical Curve Cryptography (ECC)
- the Digital Signature Standard (DSS), which incorporates the Digital Signature Algorithm (DSA)
- The Diffie-Hellman Exchange Method
- TLS/SSL Protocol
Advantages of Asymmetric Encryption
- Key distribution is not an issue since asymmetric encryption uses two keys, one public and one private.
- Again, communication with several parties is simple with a pair of keys, making it more scalable in large networks.
- Only the owner’s private key could be used to decrypt the data.
- Data won’t be compromised if the public key is lost or stolen.
- Authentication, non-repudiation, and confidential data are provided.
Disadvantages of Asymmetric Encryption
- Compared to symmetric encryption, it is slower
- More resources are used.
- It is only possible to recover the private key if it is recovered.
Symmetric Encryption v/s Asymmetric Encryption
| According to | Symmetric Encryption | Asymmetric Encryption |
| Keys used | The communication is encrypted and decrypted using just one shared key (secret key). | It encrypts data using one key, then decrypts it using a different key. |
| Cipher text size | Compared to the original plain text file, the cipher text is smaller. | The cipher text is more significant than the original plain text file. |
| The amount of data | used to send large amounts of data. | used to send small amounts of data. |
| Utilisation of Resources | Symmetric key encryption uses only a few resources to function. | High resource usage is necessary for asymmetric encryption. |
| Key Lengths | Key sizes are 128 or 256 bits. | RSA key size of 2048 bits or more. |
| Efficiency | Given that this method should be used for texts with extensive data, it is effective. | Since only brief messages are utilized with this approach, it is ineffective. |
| Approaches | It is an old approach. | It is a novel encryption method. |
| Security | There is a risk that a single key used for encryption and decoding can be compromised. | Separately created keys for encryption and decryption |
| Rapidity | Symmetric encryption is a quick method. | The speed of asymmetric encryption is slower. |
| Algorithms | RC4, AES, DES, 3DES, and QUAD. | RSA, Diffie-Hellman, ECC algorithms. |
Applications of Symmetric and Asymmetric Encryption
Symmetric and asymmetric encryption are each better suited to specific scenarios. Since it only requires one key, symmetric encryption is better suited for data that is not in use.
Data must be encrypted before being stored in databases to prevent compromise or theft. This data must be secure until it needs to be retrieved in the future. Therefore, only the one key offered by symmetric encryption is needed.
On the other hand, data transmitted to other individuals through email should be encrypted using asymmetric methods. Email data would not be secure if we utilized symmetric encryption; an attacker could subsequently compromise or steal the data by obtaining the encryption and decryption keys.
Asymmetric encryption uses the sender and receiver’s public keys to encrypt the data, ensuring that only the recipient can decrypt the data. To further enhance the data’s security, these encryption methods are combined with other procedures like digital signature or compression.
Wrap up!
In terms of encryption, the most recent techniques might sometimes be better. The appropriate encryption algorithm for the job at hand should always be used. As cryptography evolves, new algorithms are being developed to prevent keeping up with hackers and protect data to improve confidentiality.
Expect more from the cryptography community in the coming years, as hackers will inevitably make things difficult for professionals!
Recommended: ECC, RSA & DSA Encryption Algorithm: Difference to Know
