Difference between Symmetric and Asymmetric Key Encryption
Overview
To prevent unauthorized access, data that is in plaintext is encrypted into ciphertext, a format that has been scrambled. Symmetric and asymmetric cryptography are both methods for doing this, although they handle encryption keys differently.
Symmetric Key Encryption
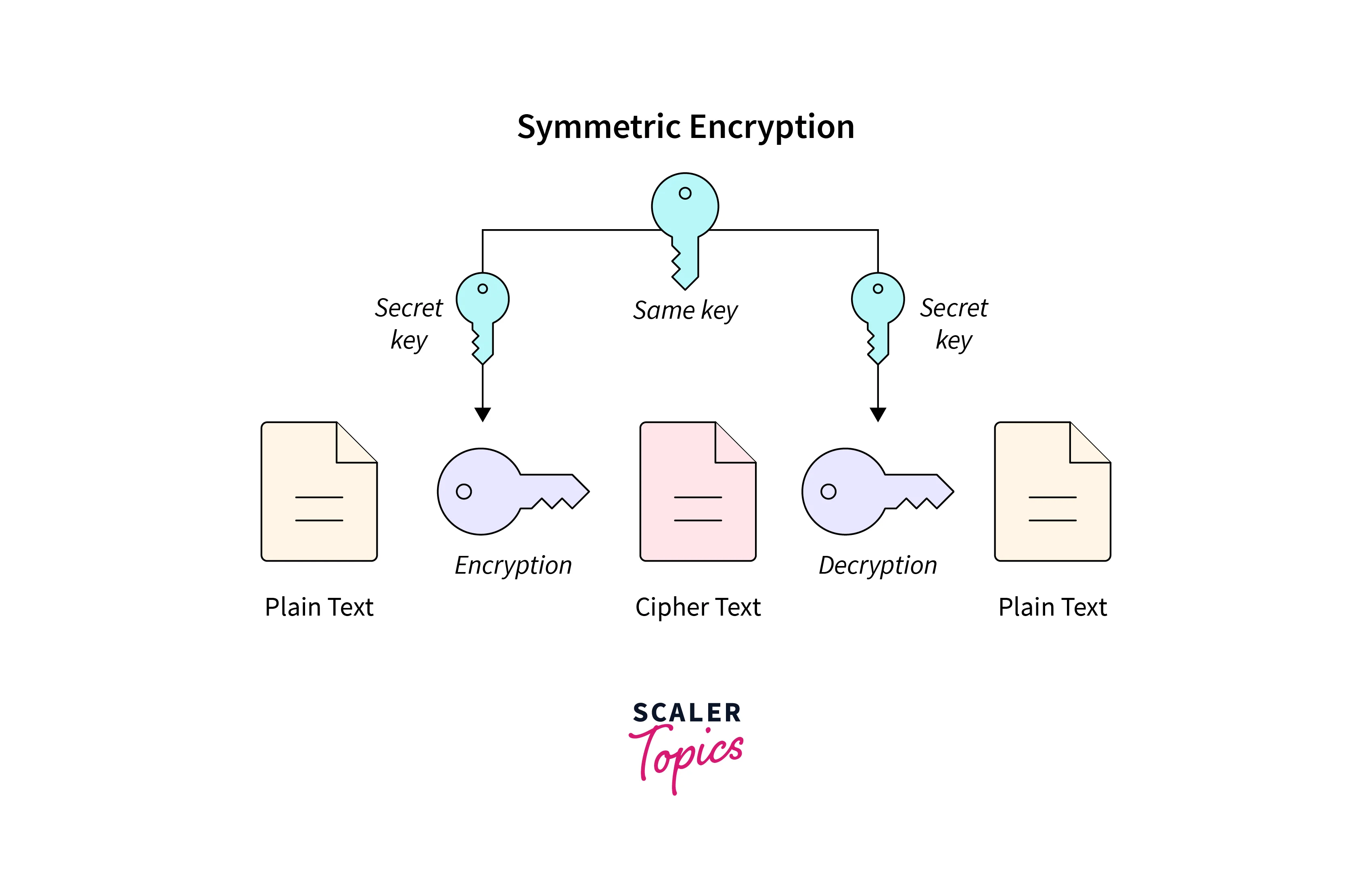
A cryptographic method known as symmetric key encryption uses the same secret key to encrypt and decode data. To convert plaintext data into ciphertext (encryption) and subsequently back into plaintext (decryption), the sender and the receiver must have the same key. Since the same key is utilized for both procedures, it is crucial to keep the key secure to protect the data's secrecy.
A brief explanation of how symmetric key encryption functions in symmetric and asymmetric cryptography is given below:
Key Generation:
An encryption algorithm creates a safe key. The sender and recipient then communicate with one another through a secure channel to exchange this key.
Encryption:
The sender encrypts the plaintext message using the secret key. The plaintext and the key are inputs into the encryption algorithm, which outputs ciphertext.
Transmission:
A weak channel is used to send the encrypted ciphertext. Without the key, it is challenging to decipher the original communication because the ciphertext seems random and impossible to understand, even if it is intercepted.
Decryption:
Using the same secret key, the recipient can unlock the ciphertext and get access to the original plaintext message. The key is used by the decryption algorithm to reverse the encryption process and restore the original form of the ciphertext.
Asymmetric Key Encryption
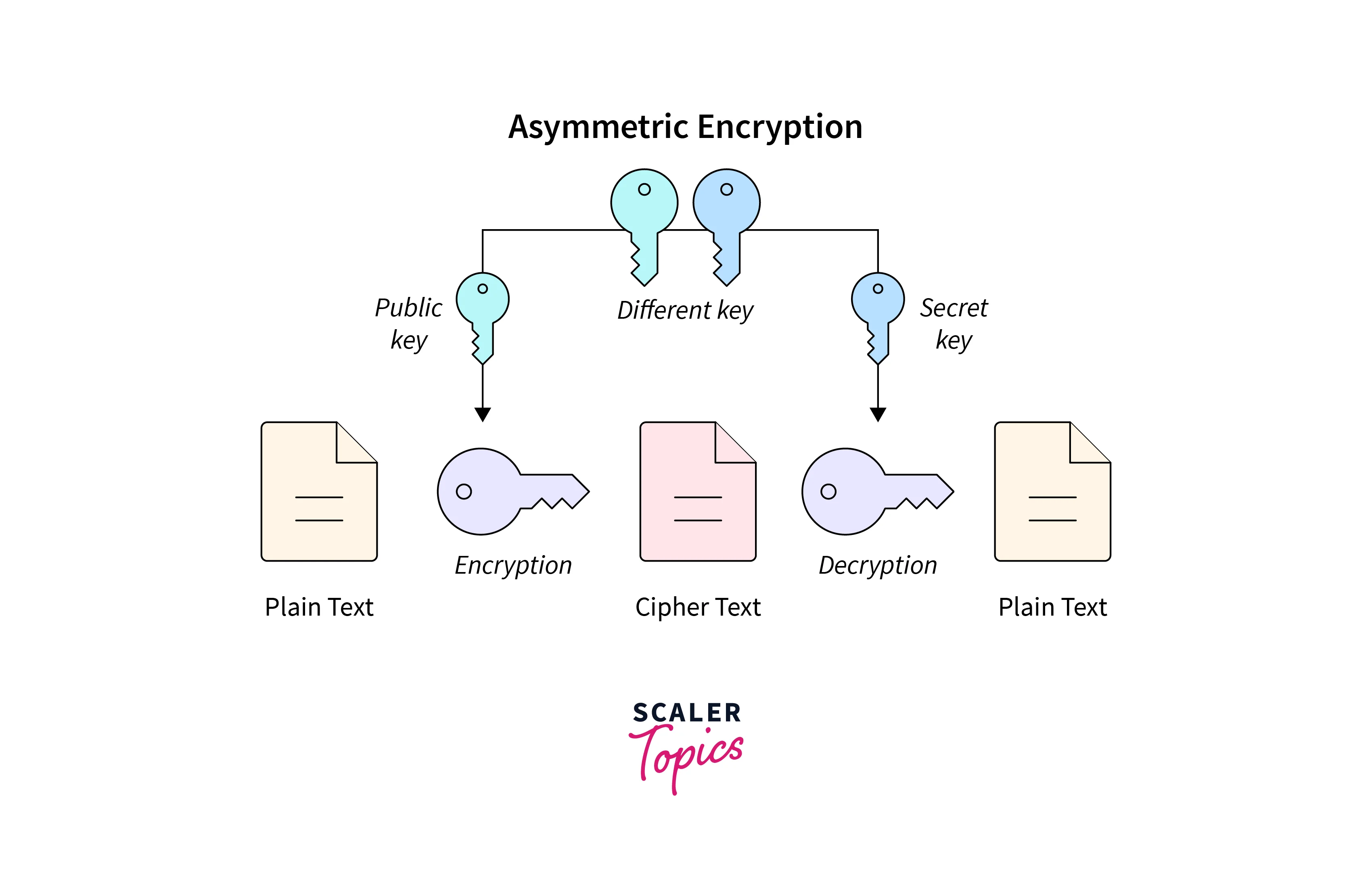
Cryptographic method employs two keys: a public key and a private key that are mathematically connected to do the process of symmetric and asymmetric cryptography. Asymmetric encryption uses distinct keys for encryption and decryption as opposed to symmetric encryption, which uses the same key for both operations.
Here is a detailed description of how asymmetric key encryption functions:
Generation of Key Pairs:
Public Key:
Anyone who wishes to send an encrypted message to the key owner must use the public key, which is meant to be widely distributed.
Private Key:
The owner must keep this private key a secret as it is used to decipher messages that have been encrypted using the associated public key.
Encryption:
Party A encrypts the message using Party B's publicly accessible public key if Party A wants to send Party B a private communication.
Transmission:
Party B receives the encrypted ciphertext over an insecure channel.
Decryption:
The ciphertext can only be decrypted by Party B, which has the associated private key. This makes use of the private key.
Digital Signatures:
Using their private key, a sender can sign a message, and the recipient can then use the sender's public key to confirm the signature.
Comparison Table
Here's a comparison of the two encryption methods:
| Aspect | Symmetric Key Encryption | Asymmetric Key Encryption |
|---|---|---|
| Keys Used | Single secret key shared between parties. | Key pair: public key and private key. |
| Key Distribution | Challenging to securely distribute the key. | Public keys can be freely distributed. |
| Security | Key exposure risks decryption of all data. | Private keys must remain confidential. |
| Use Cases | Bulk data encryption within closed systems. | Secure communication, digital signatures. |
| Key Management | Requires secure key management practices. | Private key must be well-protected. |
| Examples | AES (Advanced Encryption Standard). | RSA, ECC (Elliptic Curve Cryptography). |
| Key Generation | Typically requires key exchange methods. | Involves key pair generation. |
Conclusion
Some key points about symmetric and asymmetric cryptography:
Synchronous Key Encryption:
- Utilises a secret key that is the same for encryption and decryption.
- Faster and more effective for handling massive data volumes.
- Key distribution is difficult, and safe key sharing is essential.
- Key disclosure puts all data in danger of being decrypted.
Encryption with asymmetric keys:
- Use a set of public and private keys that are connected mathematically.
- Slower and requiring more computing because of intricate computations.
- Public keys can be freely shared, whereas private keys are kept secret.
- Private keys must be kept private; otherwise, security will be compromised.
