Asymmetric vs Symmetric Encryption: Definitions & Differences
Encryption is what makes secure data exchanges possible on the internet — let’s explore the differences between symmetric vs asymmetric encryption
Asymmetric vs symmetric encryption. Not sure what these terms are or what they mean in relation to your life? Let’s put this into terms that’ll help you understand their importance immediately.
Encryption is everywhere. From sending emails and making online purchases to securing sensitive government or healthcare-related information, symmetric and asymmetric encryption play critical roles in making secure data possible in our digital world. They’re what keep your communications secure and your sensitive data out of the hands of criminals (and the hands of anyone else who shouldn’t have it).
But what are symmetric and asymmetric encryption? When comparing asymmetric vs symmetric encryption, in what ways are they alike, and how are they different? Lastly, which is more secure in different applications?
Let’s hash it out.
Editor’s Note: This article is the first in a series of articles on symmetric encryption. Be sure to check out the related articles below:
- Symmetric Encryption 101: Definition, How It Works & When It’s Used
- Symmetric Encryption Algorithms: Live Long & Encrypt
- Block Cipher vs Stream Cipher: What They Are & How They Work
What Is Encryption and How Does It Work? A Quick Refresher
Okay, this is going to be a bit of a heavy topic, but we’re going to simplify this as much as possible to appeal to all of our readers, regardless of your level of tech-savviness. So, before we can jump right into talking about asymmetric vs symmetric encryption, I think it would be important to quickly review what encryption is in general and how encryption works in general.
You can define encryption as a means by which to convert readable content (plaintext) into unreadable gibberish (ciphertext). Encryption is a mathematical operation that exists within the realm of cryptography. This is why you’ll often hear people talking about encryption and cryptography within the same discussion or sometimes use the terms interchangeably. However, there’s an important difference:
- Cryptography is the overarching term for the field of cryptographic communications.
- Encryption, on the other hand, refers to the actual process of encrypting plaintext data into unreadable ciphertext.
Basically, encryption is the process of transforming plaintext into ciphertext through the use of two important elements:
- Algorithms — An encryption algorithm is a set of directions to help you solve a problem. More specifically, it’s a set of mathematical instructions and processes that serve a specific purpose. Some algorithms are designed to work in either private or public channels. So, you can have asymmetric or symmetric encryption algorithms. In general, encryption algorithms are useful for encrypting data. When coupled with authentication measures, they also protect data integrity.
- Keys — A cryptographic key is a long, random and unpredictable string of letters and numbers that you use to encrypt or decrypt data. No matter whether you’re talking about asymmetric vs symmetric encryption, the keys are important to protect. We’ll talk more about those later.
Let’s take a look at a simplified illustration of the process to better understand how encryption works in general:
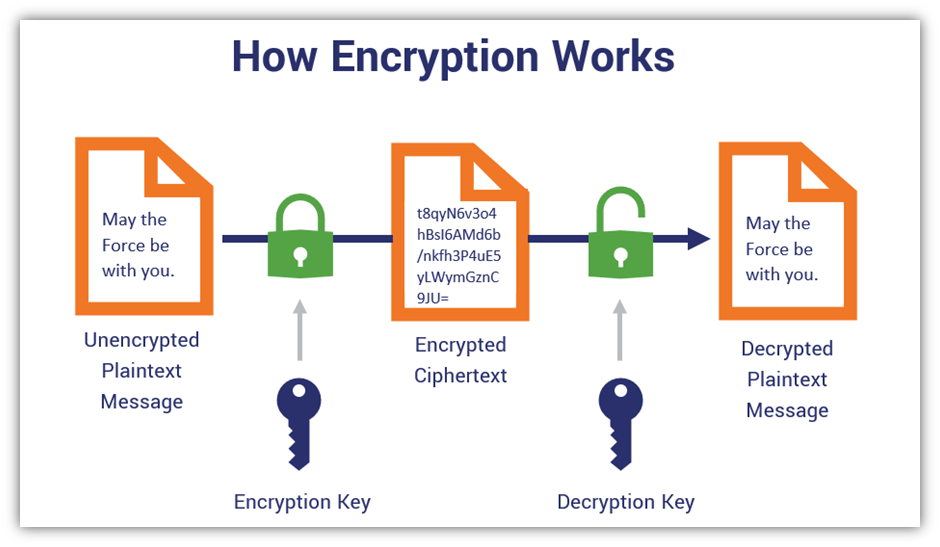
- You take a plaintext, unencrypted message (such as “May the Force be with you.”) and apply an encryption key to it.
- This process converts your message into nonsensical ciphertext (like “t8qyN6v3o4hBsI6AMd6b/nkfh3P4uE5yLWymGznC9JU=” in the example above). Without the decryption key, no one can decipher the meaning of the message.
- You use a decryption key to descramble the message. This reverts the unreadable ciphertext into words that make sense.
That’s encryption in a nutshell. In the example graphic above, you may have noticed that the encryption and decryption keys are the same. No, this isn’t a mistake — it’s an example of symmetric encryption (which we’ll talk more about shortly). That’s because in symmetric encryption, one key encrypts and decrypts data. Asymmetric encryption looks similar, but it will involve using two separate keys that are related yet still unique.
We’ve talked about different types of encryption before in some of our blog posts. But when it comes to a topic like asymmetric encryption vs symmetric encryption, there’s a lot to unpack. So, let’s explore each of these types of encryption individually to ensure a full understanding.
Asymmetric vs Symmetric Encryption: What They Are & How They Work
What Is Asymmetric Encryption? Public Key Encryption Defined & Explained

Asymmetric encryption is also a process of encrypting data between two parties — but instead of using a single key (as with conventional cryptographic systems), it uses two unique yet mathematically related keys to do so. The first key, known as the public key, encrypts your data before sending it over the internet; the other (aka the private key) decrypts the data on the recipient’s end of the exchange. This is why asymmetric encryption is also known as public key encryption and public encryption.
The public and private keys are mathematically related yet uniquely paired so that they match only one another. However, one key is publicly available while the other remains hidden and is never shared.
However, encrypting data isn’t all that asymmetric encryption does. As TV infomercials love to say — but, wait, there’s more! Asymmetric encryption also offers:
- Authentication —Asymmetric encryption helps you to verify identities in a way that no one can fake or contest (this is known as non-repudiation), which makes this process is ideal for encrypting data between third parties who don’t know each other.
- Secure Key Exchanges — Asymmetric key exchange protocols facilitate symmetric key exchange (more on that a little later) via public channels that are otherwise susceptible to man-in-the-middle (MitM) attacks.
- Data Integrity — Offers assurances that your data hasn’t been altered or modified through the use of digital signatures.
Asymmetric encryption plays a crucial role in public key infrastructure (PKI), which we’ll talk more about shortly. But first, let’s hash out what symmetric encryption is and why it’s also so important.
What Is Symmetric Encryption? Secret Key Encryption Defined & Explained

Symmetric encryption is another way to encrypt and decrypt data, but it uses one secret key instead of two to do so. Basically, the sender and the recipient have identical copies of the key, which they keep to themselves. This is why symmetric encryption is also known as private key encryption, private key cryptography, secret key encryption, secret key encryption, secret key cryptography, and symmetric cryptography.
Symmetric encryption is the workhorse of cryptography. It’s what enables you to encrypt massive quantities of data without bogging down processors, internet speed, and other IT resources. It’s significantly more efficient than asymmetric encryption at scale and is an invaluable tool for large organizations and businesses in particular that value data security, privacy, and confidentiality.
You’ll find symmetric encryption in use for everything from banking and financial transactions to protecting data at rest. We recently wrote an article that offers a deep dive into the topic of symmetric encryption. Be sure to check that out for a more in-depth look at what symmetric encryption is and how it works.
What Is the Difference? Symmetric vs Asymmetric Encryption
Okay, so now that we know what asymmetric and symmetric encryption are overall, let’s compare and contrast them. There are several key traits that make symmetric and asymmetric encryption different in terms of how they work and where they’re most valuable:
1. The Number, Nature, and Size of the Cryptographic Keys
Symmetric keys are identical, whereas asymmetric public and private keys are mathematically related yet still unique. Symmetric keys are also typically shorter in length than their asymmetric counterparts. Symmetric keys are frequently 128 bits, 192 bits, and 256 bits, whereas asymmetric keys are recommended to be 2048 bits or greater.
For example, here’s an example of what a base64-encoded AES-256 symmetric encryption key looks like:
QnqAb/Q+TosXWD8OxIiaBjriAJNqYs4VNtvGc87kmsY=Now, let’s take a quick peek at what RSA 2048-bit asymmetric encryption keys look like.
Public key:
-----BEGIN PUBLIC KEY-----
MIIBITANBgkqhkiG9w0BAQEFAAOCAQ4AMIIBCQKCAQBwviVpz7WKp2jXTpRZB0QO
yDwa7KTVBT/2XLRLHDaLL+lO/DrJRN1IY8EaoaSO8LDp/Kxoe/U4HI/98Lzmabm/
9o/sGN6LH2rqNQET+c1WsMPTAz6+WFpnbbMataoAH6vzDfVFRy6GnF/AsnnpgF15
wqmwLq7T5s+Vq8qo+nT/MOYUyR81CY0FQurfc58aPwSg6yC5OLOGdz7eiAvOMysC
zOJZy0n8BIRXn7Yrh7wo9HdSAGEb1rzFxLAyoEthN+GFvH7uN1P76l5g8E3k6Z5M
4FXsk7uqIO8gdD8nuM1jH0YK1OxWl8UdQpVMx306pNM5npHhI0pbXn5D9XThAKgt
AgMBAAE=
-----END PUBLIC KEY-----
Private key:
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQBwviVpz7WKp2jXTpRZB0QOyDwa7KTVBT/2XLRLHDaLL+lO/DrJ
RN1IY8EaoaSO8LDp/Kxoe/U4HI/98Lzmabm/9o/sGN6LH2rqNQET+c1WsMPTAz6+
WFpnbbMataoAH6vzDfVFRy6GnF/AsnnpgF15wqmwLq7T5s+Vq8qo+nT/MOYUyR81
CY0FQurfc58aPwSg6yC5OLOGdz7eiAvOMysCzOJZy0n8BIRXn7Yrh7wo9HdSAGEb
1rzFxLAyoEthN+GFvH7uN1P76l5g8E3k6Z5M4FXsk7uqIO8gdD8nuM1jH0YK1OxW
l8UdQpVMx306pNM5npHhI0pbXn5D9XThAKgtAgMBAAECggEAcGp4nbf5eaaRmFYG
/3qKNv8bR3F8rddNPtaTA22/SSvdw98msreSuXKWAnr4vXprvPQv6QLosSlxvjCD
+m+jQjCUs0Lc6/XIwn1VdNiZEX6x076hmmQ4yHaOpuxK9VKfPnxFeu2OC7TymQ6d
FuHi0tzyG/WAZ1P22nNwYOtTK3v2+56QcWpshNWgtPRHC4Y7Cbqn3dEnrQAVhqiY
Xd/wzizzcXbn/49JCTypxgQ8Ru5a7/PvRtKiRAUd1Y7nGX5wKAgkVz9RqSe8y/lD
PLea1jQT+1oCIGS2CnTL4pBfrJCfmfW2n7WkHTvd+RUkScC9RtJBwYYaNBjhPd0D
XnABFQKBgQDXvLn3CXrTjxlEpNeXLkiVmQxMjYlZ+gvrGkHNW8eeUfJHptTAh+0Y
oZTI/IOyxArbn3r0VmrpDOlOlt3atiRAPqNFcsp53TgDviNyrGlRMZlXvNrHKVS6
fe0FcXVlxnMIRQU3dbSoe9aO03aszbm/F5aDfaob7jdrjhSz5TOPkwKBgQCFyKe8
wUZkH+bRWNxhbj5XjpSWw+Cwe3IJMXm+cXKGKOp8znqAavRkQQPT7rGKMdZEjN/C
O8JIdmPtkGlTN/AWYxaXKjM5qsNdPgNjRPao70OVe/5GM7Z1JPy0GkL5DhyxoMMJ
8UPwStAaJuTZWJwOw4G8pVf0KvEbh6Vd6DRBPwKBgQCycoAcT/ISBl6vQe62NWmC
nGro83X2P/cVy808ETunwD64d82pR4WdhyHrsbs55iDZEyx/6O9bv/tHr1DpNRn9
LhKdQlsqvAo2RlNJ6kTfDTi6sxMABDb6X2jrxLKHscO6xmSPQERjzLNnxpB2VWDc
KKWuNAa+PagHxilnuCGTEwKBgDTinERGlv/viHwLR5sQTH6qM1zh88lwEyVFNJ4v
FJmqRP+vU8e9//w9ozi9K9u4Vb5lffK3Utb4TgpUQv6Np1ACPaTmHrfWJEKQyCAO
2/7uDmZiTKMNwDvQskCz/POdO4SQS2l7wWKVAGzGIUM1/wLrEDc1mW5BJ2y9k4Zq
y3VbAoGAVKUM5mIE4rzMEEtU7xBRSat1xwIFNOsY77+nHBG4pU5AKPgfPzHpFACj
yskOW0OG5io0/bmydqpElMSLLxkekPXXDQD3lSPZei9ZOuyWALWb9kXb/U/cxaMh
H2bnVTgEcBNGdFCYXy4u1AAkVICajJ7Vkd4jGPReuYuF452w+34=
-----END RSA PRIVATE KEY-----
See the difference? But that’s not the only thing that differs when comparing asymmetric vs symmetric encryption.
2. How the Keys Are Distributed
With asymmetric encryption, exchanging keys via digital public channels isn’t an issue. That’s because asymmetric key exchange protocols were literally designed with that very purpose in mind. To securely exchange symmetric keys, on the other hand, you’d need to meet up in person (offline). Not only is this inconvenient, but it also defeats the purpose of communicating digitally in the first place!
Exchanging symmetric keys in public channels (like on the internet) otherwise is an issue because the key is vulnerable. Using asymmetric techniques in the key exchange process is more secure. This is why PKI incorporates the use of asymmetric key exchange protocols for the symmetric key exchange process as part of the TLS handshake.
According to the original X.509 standards that were published by the CCIT (now ITU-T) and ISO in 1988:
“The necessary key exchange for either case is performed either within a preceding authentication exchange or off-line any time before the intended communication. The latter case is outside the scope of the authentication framework.”
3. The Types and Complexities of the Encryption Algorithms
One of the big differences between symmetric vs asymmetric encryption is the types of encryption algorithms used in each process. Symmetric encryption algorithms are either block ciphers or stream ciphers, and include algorithms like DES, TDEA/3DES, AES, etc. Asymmetric encryption algorithms, on the other hand, include algorithms like RSA, DSA, ECC, etc.
4. How Time-Consuming and Resource-Intensive Each Process Is at Scale
Symmetric encryption, because it’s faster and only uses one key, is great for large organizations and businesses that need to encrypt vast quantities of data. Asymmetric encryption uses two separate keys and more complex algorithms in the encryption and decryption process, which makes it slower for encrypting and decrypting large amounts of data.
However, when comparing asymmetric vs symmetric encryption, you also must keep in mind the channels that you’re using it in. Is it a public-facing channel or something private?
5. One’s Better Suited Than the Other For Use in Public/Private Channels
We’ve already talked about this, but to quickly summarize — symmetric encryption on its own is best suited for non-public channels and asymmetric encryption is best for public channels. That’s a quick way to think of the differences with asymmetric vs symmetric encryption.
But why does it have to be either/or? Why can’t we use both together in a way that’s complementary? Well, we do — and this concept is at the very heart of public key infrastructure.
The Roles of Asymmetric and Symmetric Encryption in Public Key Infrastructure
Asymmetric encryption and symmetric encryption both play crucial roles in public key infrastructure, or PKI for short. PKI is a framework of technologies, processes, and policies that serves as the foundation of internet security. Basically, it’s what makes secure data exchanges possible over the internet. You see, the internet itself is insecure. So, PKI outlines everything that makes it possible to:
- Authenticate you and a third party that you’re connecting to (for example, connecting your browser to the server of a website).
- Securely exchange keys via insecure public channels.
- Securely encrypt data that exchanges between two parties (such as when sending emails, shopping on your favorite website, etc.).
Public key encryption, key exchanges, and digital signatures all play pivotal roles in securing digital communications. Once parties are authenticated and keys are securely exchanged to create a secure connection, then symmetric encryption can often take over to speed up the data encryption process.
Encryption Is What Makes Your Online Shopping, Banking & Other Data Exchanges Secure
Without encryption, the data you transmit across the internet travels in plaintext format. This means that anyone who can intercept it can read it. So, whenever you buy something from amazon.com, for example, your credit card and other personal information travel through multiple touchpoints — networks, routers, servers, etc. — located throughout the world. This means that when you transmit data through those channels, someone could intercept that data and read it.
Of course, this is why we constantly preach about using websites that are secured by SSL/TLS certificates here at Hashed Out. Why? Because it means that your data is secure while traveling through all of those different channels to get from point A to point B.
So, if you like being able to buy ‘snazzy’ custom socks that have your dog’s face printed on them in private, without someone intercepting your order and stealing your credit card information, then you’re a fan of PKI.
Symmetric vs Asymmetric Encryption: Which Is Better?
Forgive me for a moment as I channel my inner Peter Griffin, but “you know what really grinds my gears?” When I ask a question and I get the wishy-washy answer “it depends.” But, in the case of determining which is “better” — asymmetric or symmetric encryption — that same loathed answer really rings true. That’s because “better” can be defined in different ways depending on the specific circumstances at hand.
For example, in non-public facing environments, symmetric encryption is great because it’s a less complex process that allows for faster, more efficient data encryption. This means that you can encrypt large quantities of data without bogging down your IT resources. But when you use that same speedy encryption process in public channels on its own, without an asymmetric key exchange first, then it’s not so great. In fact, it can be downright dangerous. This is why asymmetric encryption is so important in public channels (such as on the internet).
Asymmetric encryption, although slower, is better for those circumstances where your data is at risk of being intercepted by unintended third parties. It offers you greater security in terms of authentication and non-repudiation — so you know you’re talking to the right person — as well as data integrity.
Symmetric vs Asymmetric Encryption: Which Is More Secure?
So, to answer the question about whether symmetric or asymmetric encryption is more secure, I’d again have to give the dreaded answer, “it depends.” And it really does — the answer depends on how you define “more secure” and in what context the encryption takes place. For example:
- Symmetric encryption is more secure than asymmetric encryption when you use smaller key sizes (such as a 256-bit key). That’s because in asymmetric encryption that uses smaller keys, having the public key actually makes the private key easier to calculate. (This is why we use larger keys in asymmetric encryption.)
- Asymmetric encryption is more secure when you use larger key sizes (such as a 2048-bit key). This is because it involves the use of more complex encryption processes and two separate keys rather than two identical copies of a single key.
So, if you’re comparing an asymmetric key pair and a symmetric key of equal size (in terms of bits) side by side, you’d be able to calculate the asymmetric pair’s private key more easily. This explains why we use asymmetric key sizes (2048 bits or higher) that are significantly larger than symmetric key sizes (typically just 256 bits) in asymmetric encryption.
However, the larger the asymmetric keys are, the more processing power they require. This is why, when establishing an encrypted website connection, we start out using an asymmetric key exchange before switching to symmetric encryption to secure the session. So, in that way, asymmetric encryption helps to make symmetric encryption more secure.
Of course, this answer is also dependent on the technologies that are in use at the time. For example, asymmetric encryption methods like RSA are incredibly secure (but are also resource draining). It would take thousands of lifetimes to break this algorithm using modern computers. But what happens when computers get smarter, faster, and more capable?
The Rise of Quantum Computing and Its Future Impact on Encryption
Of course, when it comes to encryption, concerns relating to quantum computing are always lurking. Quantum computers, unlike classical computers, operate using different directions that’s based on quantum physics. As such, they can run advanced algorithms (quantum algorithms) and achieve things that traditional computers simply can’t.
As such, the overarching concern is that these computers, which are capable of completing steps and processing calculations at exponentially faster rates than our modern supercomputers, will break modern asymmetric cryptography as we know it. So, you’ll often hear people calling out warnings about the dangers of quantum computing with regard to quantum cryptography.
Shor’s Algorithm
This is what people are typically referring to when they talk about the threat of quantum computing to encryption. Mathematician Peter Shor came up with this algorithm, which provides exponential speedup, in 1994. (He later revised and expanded upon the paper a couple of years later.) The concern surrounding his algorithm is that it would make the factoring of larger numbers and calculation of discrete logarithms that asymmetric cryptography is based on vulnerable.
Here’s a quick video from Shor himself on the factoring algorithm:
If that explanation was clear as mud, let’s try a different approach. Essentially, it nullifies modern public key encryption schemes (like RSA). So, what this means is that quantum computers will break our modern asymmetric cryptosystems — leaving them useless against cybercriminals and other schmucks who wish to do bad things.
However, Shor’s algorithm applies to asymmetric cryptographic systems, not symmetric ones. You need the public key to be able to calculate the private key using Shor’s Algorithm — and remember, symmetric encryption doesn’t use public keys. But is there a type of algorithm that poses a threat to symmetric encryption? Yes and no.
Grover’s Algorithm
If your first thought is of a blue Muppet when you read that header, then I’d suggest you grab another cup of coffee before reading this part. This algorithm, which was developed by Lov Grover in 1996, is one that applies to symmetric cryptographic systems. It’s an algorithm that provides a quadratic speedup to address unordered search (whereas Shor’s offers exponential speedup), which means that it can make brute-force searches substantially faster for encryption schemes that use smaller key sizes.
The idea behind Grover’s algorithm is that it essentially cuts symmetric key lengths in half, making them faster to compute. However, it’s a concern is something that many experts believe can be addressed by increasing key spaces to double key lengths.
Researchers in the Department of Informatics at the University of Oslo in Norway shared the following in an article in the International Journal of Advanced Computer Science and Applications (IJACSA):
“For symmetric cryptography quantum computing is considered a minor threat. The only known threat is Grover’s algorithm that offers a square root speed-up over classical brute force algorithms.”
The researchers go on to state some good news as far as symmetric encryption is concerned:
“The Advanced Encryption Standard (AES) is considered to be one of the cryptographic primitives that is resilient in quantum computations, but only when [it’s] used with key sizes of 192 or 256 bits.”
Researchers at Princeton University’s Center for Information Technology Policy created a paper for Carnegie’s Encryption Working Group that shares the following about the implications of quantum computing on encryption:
“[…] it is possible to compensate for the effect of quantum computing by increasing the key size, expanding the space that must be searched by brute force, so as to counteract the effect of Grover’s Algorithm. For many encryption algorithms, doubling the key size, say from 128 bits to 256 bits, has the effect of squaring the size of the key space that someone without the key would have to search. This countermeasure exactly offsets the square-root effect of Grover’s Algorithm, restoring the security level of the pre-quantum algorithm.
One consequence is that data that was encrypted before the emergence of viable quantum computing—with the original smaller key size—will become susceptible to decryption when quantum computing does become available, but data encrypted with the larger quantum-safe key size will continue to be secure.”
Preparing for the Future With Post-Quantum Cryptography
Let me start off by saying that the situation isn’t as bleak as some would make it out to be. Yes, absolutely, quantum computing poses a future threat to modern asymmetric cryptography. But the sky isn’t falling — yet. There are some bits of good news to consider.
For one, quantum computing is a concern we’ve known about for decades. Quantum cryptography was proposed back in the 1980s, and both Shor’s and Grover’s algorithms were developed in the mid-1990s. So, it isn’t something new. Experts are working to come up with solutions and standards that will prepare us to deal with these issues once quantum cryptography officially arrives.
For example, the National Institute of Standards and Technology (NIST) has been working on narrowing down the list to several post-quantum cryptography (PQC) algorithms as part of its standardization plan. For example, as of July 2020, they’ve managed to narrow the list down to just 15 algorithms for:
- Public key encryption and key-establishment algorithms
- Digital signature algorithms
- Alternate algorithms
Why so many algorithms and why worry about it now? According to NIST’s Post-Quantum Cryptography Call for Proposals page:
“it appears that a transition to post-quantum cryptography will not be simple as there is unlikely to be a simple ‘drop-in’ replacement for our current public-key cryptographic algorithms. A significant effort will be required in order to develop, standardize, and deploy new post-quantum cryptosystems. In addition, this transition needs to take place well before any large-scale quantum computers are built, so that any information that is later compromised by quantum cryptanalysis is no longer sensitive when that compromise occurs. Therefore, it is desirable to plan for this transition early.”
But there is good news here. Certificate authorities like Sectigo and DigiCert are trying to head such problems off at the pass. They’re preparing for the inevitable by creating what they’re calling “hybrid” certificates. The thought here is that these certificates will help prepare organizations for the impending PQC world while also still making it so that their systems and infrastructure are still compatible with non-PQC setups. So, instead of using certificates that support only current asymmetric encryption algorithms or PQC encryption algorithms, they’ll enable your systems to still be interoperable with systems that support either or both types of algorithms.
The truth is that we’re still years away from having quantum computers commercially available. It’s on the horizon, but we’re just not there yet. So, all of this is to say that while quantum computers are a concern that the industry as a whole is preparing for, it’s just a waiting game at this point.
Final Thoughts on Asymmetric vs Symmetric Encryption
There are so many benefits and applications for symmetric and asymmetric encryption. The more that you learn about these two methods of encryption and how they work to secure our data in digital spaces, the more fascinating it becomes. Hopefully, this article has helped you better understand the strengths and weaknesses of each process, as well as how they complement each other.
Asymmetric and symmetric encryption alike both hold important places within the realm of public key infrastructure and digital communications. One without the other would be either incredibly insecure or so bulky and unmanageable that it wouldn’t be practical. This is why both types of encryption are crucial to internet security as we know it.
Have thoughts about symmetric and asymmetric encryption that haven’t been covered here? Be sure to share them in the comments section below!







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)











5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown