US20020049760A1 - Technique for accessing information in a peer-to-peer network - Google Patents
Technique for accessing information in a peer-to-peer network Download PDFInfo
- Publication number
- US20020049760A1 US20020049760A1 US09/883,064 US88306401A US2002049760A1 US 20020049760 A1 US20020049760 A1 US 20020049760A1 US 88306401 A US88306401 A US 88306401A US 2002049760 A1 US2002049760 A1 US 2002049760A1
- Authority
- US
- United States
- Prior art keywords
- file
- peer
- network
- information
- hash
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Abandoned
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/10—Protocols in which an application is distributed across nodes in the network
- H04L67/104—Peer-to-peer [P2P] networks
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/10—File systems; File servers
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/90—Details of database functions independent of the retrieved data types
- G06F16/901—Indexing; Data structures therefor; Storage structures
- G06F16/9014—Indexing; Data structures therefor; Storage structures hash tables
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/06—Protocols specially adapted for file transfer, e.g. file transfer protocol [FTP]
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/10—Protocols in which an application is distributed across nodes in the network
- H04L67/104—Peer-to-peer [P2P] networks
- H04L67/1061—Peer-to-peer [P2P] networks using node-based peer discovery mechanisms
- H04L67/1063—Discovery through centralising entities
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/10—Protocols in which an application is distributed across nodes in the network
- H04L67/104—Peer-to-peer [P2P] networks
- H04L67/1074—Peer-to-peer [P2P] networks for supporting data block transmission mechanisms
- H04L67/1078—Resource delivery mechanisms
- H04L67/108—Resource delivery mechanisms characterised by resources being split in blocks or fragments
Definitions
- peer-to-peer networks may be used for implementing distributed file sharing systems wherein selected files stored on each peer network device may be made accessible to other peer network devices in the peer-to-peer network. Accordingly, peer-to-peer network architectures are highly scalable, since files may be retrieved from many locations rather than just one central location (e.g., a central server).
- peer-to-peer file sharing applications such as NAPSTERTM and GNUTELLATM now provide the ability for Internet users to configure their computer systems to function as peer network devices in a peer-to-peer network implemented across the Internet. In this way, an Internet user is able to access desired files which are stored at the computer systems of other Internet users.
- the peer-to-peer network includes a plurality of peer devices and a database accessible by at least a portion of the peer devices.
- Each of the peer devices is configured to store information files, and is further configured to share content from selected information files with at least a portion of the other peer devices in the network.
- Each shared file in the network has a respective fingerprint IID associated therewith relating to its file content.
- files in the peer-to-peer network may be identified and/or accessed based upon their associated hash ID values. In this way it is possible to identify identical files stored in the peer-to-peer network which have different file names and/or other metadata descriptors. Additionally, since the content of all files having the same hash ID will be identical, an automated process may be used to retrieve the desired content from one or more of the identified files. For example, a user may elect to retrieve a desired file (having an associated hash ID) which may be stored at one or more remote locations in the peer-to-peer network.
- an automated process may use the hash ID (associated with the desired file) to automatically select one or more remote locations for retrieving the desired file.
- the automated process may choose to retrieve the entire file contents of the desired file from a specific remote location, or may choose to receive selected portions of the file contents of the desired file from different remote locations in the peer-to-peer network. Further, if an error occurs during the file transfer process, resulting in a partial file transfer, the automated process may be configured to identify the portion(s) of the desired file which were not retrieve, and automatically select at least one different remote location for retrieving the remaining contents of the desired file.
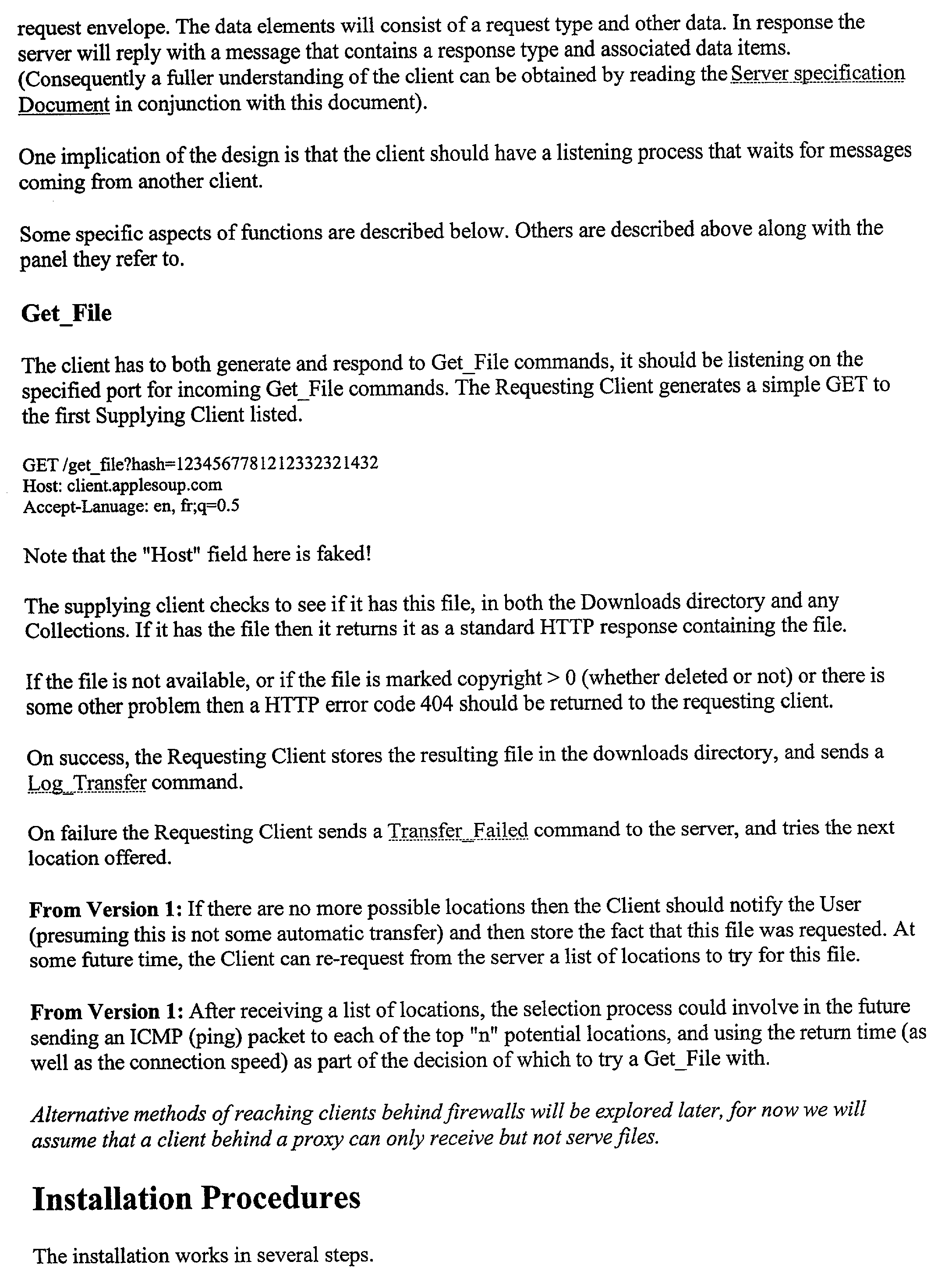
- FIG. 1 illustrates a block diagram of peer-to-peer network which may be used for implementing the technique of the present invention in accordance with a specific embodiment of the present invention.
- FIG. 2 shows a block diagram of HASH coding of a file in accordance with a specific embodiment of the present invention.
- FIG. 3A shows a block diagram of directory data structures in accordance with a specific embodiment of the present invention.
- FIG. 3B shows a block diagram of an example of specific data stored in the directory data structures in accordance with a specific embodiment of the present invention.
- FIG. 4A shows a block diagram of an example of specific data stored in the peer directory structures in accordance with a specific embodiment of the present invention.
- FIGS. 4B and 4C illustrates flow diagrams of the directory synchronization process between a local peer directory and a central directory in accordance with a specific embodiment of the present invention.
- FIG. 5 illustrates a trace diagram of the technique for searching files in accordance with a specific embodiment of the present invention.
- FIGS. 6 A- 6 C illustrates a trace diagram of a file retrieving technique in accordance with a specific embodiment of the present invention.
- FIG. 7 shows a trace diagram of another file retrieving technique from multiple peers in accordance with an alternative embodiment of the present invention.
- FIG. 8 shows a block diagram of a chunk map for the management of the retrieval of “chunks” of a file for the file retrieving technique in accordance with the alternative embodiment of the present invention.
- FIG. 9 illustrates a flow diagram of the chunk management technique across multiple worker threads for the file retrieving technique in accordance with the alternative embodiment of the present invention.
- FIG. 10 illustrates a flow diagram of the chunk management technique when an unresponsive peer for the file retrieving technique in accordance with the alternative embodiment of the present invention.
- FIG. 11 shows a specific embodiment of a peer network device 60 which may be used for implementing the technique of the present invention.
- FIG. 12 is a diagram of an example of a screen shot illustrating a user interface on a peer device in accordance with a specific embodiment of the present invention.
- FIG. 13 is a diagram of another example of a screen shot illustrating a user interface showing a search input field in accordance with a specific embodiment of the present invention.
- FIG. 14 is a diagram of the example of a screen shot of FIG. 13 illustrating a selection of the search input field in accordance with a specific embodiment of the present invention.
- the present invention provides an improved technique for accessing information in a peer-to-peer network.
- each file accessible in the peer-to-peer network is assigned a respective hash ID or fingerprint ID which is used to describe the contents of that file.
- a conventional hash or fingerprinting algorithm may be used to analyze the contents of a selected file, and generate a unique hash ID or fingerprint ID which may be used for identifying the specific contents of that file.
- the hashing algorithm is designed such that no two files having different file content will have the same hash ID. However, files having identical file content will have the same hash ID.
- the file name and metadata associated with a file are not included in the computation of the hash ID for that file.
- files in the peer-to-peer network may be identified and/or accessed based upon their associated hash ID values. In this way it is possible to identify identical files stored in the peer-to-peer network which have different file names and/or other metadata descriptors. Additionally, since the content of all files having the same hash ID will be identical, an automated process may be used to retrieve the desired content from one or more of the identified files. For example, a user may elect to retrieve a desired file (having an associated hash ID) which may be stored at one or more remote locations in the peer-to-peer network.
- an automated process may use the hash ID (associated with the desired file) to automatically select one or more remote locations for retrieving the desired file.
- the automated process may choose to retrieve the entire file contents of the desired file from a specific remote location, or may choose to receive selected portions of the file contents of the desired file from different remote locations in the peer-to-peer network. Further, if an error occurs during the file transfer process, resulting in a partial file transfer, the automated process may be configured to identify the portion(s) of the desired file which were not retrieve, and automatically select at least one different remote location for retrieving the remaining contents of the desired file.
- the network 100 includes a plurality of peer network devices 102 a - 102 n , and at least one central server system 110 .
- the peer devices 102 a - 102 n are communicably connected to each other and to the central server 110 via the Internet 104 .
- the peers may communicate with each other and the server via the http protocol or via a private protocol, the former being preferable to minimize the effects of various firewalls that may exist between any given peer device and the Internet 104 .
- the server 110 preferably includes software or firmware that handles communication between the peer devices 102 a - 102 n and the central server 110 , and that performs specific logical operations on the directory 112 on the server.
- the directory 112 may be stored in a single relational database, but permanent storage may also be accomplished by an object database, a directory server, or multiple databases.
- Files 202 that are to be shared are only stored on the peer devices 102 a - 102 n .
- the directory 112 stores information about the files (e.g., HASH ID, filename, metadata, size, type, etc.) but not their contents.
- the directory 112 stores information about the peer devices themselves (e.g., Peer ID) and most importantly, which peer devices the files 202 exist on at any given time.
- file 202 may contain any type of stored information. These include, for example, jpeg, mpeg and mp3.
- FIG. 2 the unique footprinting of a file 202 is illustrated in accordance with one specific embodiment of the present invention.
- the process by which a file 202 may be uniquely identified is through the application of HASH code 204 .
- Each peer device 102 a - 102 n that wishes to publish a file on the peer-to-peer network 100 first computes the HASH code 204 of that file.
- the HASH code 204 may be computed via conventional algorithms which generate a unique identifier based upon the content of a particular file.
- fingerprinting or hash code algorithm examples include, MD5 (described in RFC 1321, and attached hereto has Appendix A), and Keyed SHAL (described in RFC 2841, and attached hereto has Appendix B). Each of these references is incorporated herein by reference in its entirety for all purposes.
- MD5 See Appendix A
- Other algorithms may also be used such as, for example, Keyed SHAI (See Appendix B) which mathematically characterizes the audio or visual waveforms of the content of the file and creates a unique code representation of that file.
- the filename, time/date stamps, and any other meta-data about the file are not included in the computation of the HASH code.
- Different peers, or even the same peer can refer to or describe what is in fact the same file content by different names. The desired files are more likely to be found, as different users may search for files using different names, descriptions, or other characteristics, although the file content is identical.
- Such unique ID association allows each user to name and describe a given file in the manner most relevant to them.
- the central directory data 300 may be stored in a relational database.
- FIG. 3A illustrates three of the central tables in the directory data structures 300 : the file directory table 310 ; the elements table 320 ; and the users table 330 .
- the file directory table 310 contains information about the file contents only, including the HASH code or ID, the size, and the type (video, music, image, etc . . . ). Other information specific to the contents of the file may also be stored in this table.
- the elements table 320 contains descriptive information or meta data about each file as entered and maintained by each individual user.
- This elements table 320 also includes foreign keys Hash code ID and Peer device ID that points to the files 310 and users tables 330 , respectively.
- the users table 330 contains information about each user and his/her peer device 102 a - 102 n .
- the users table also maintains the systems current knowledge as to which user is currently connected to the peer-to-peer network 100 .
- the relationship between the three tables of FIG. 3A can be defined such that each user can have many files and each file can be owned by many users.
- each user can have their own individual description of each file and may possibly describe the same file in more than one way, although the file content, and thus, the HASH coding are identical.
- file directory table 350 for instance, the HASH ID 354 , the file size 356 and file type 358 are categorized and stored in the central server 110 for each particular file 351 a - 351 c .
- the HASH ID 364 , the file name 362 , the metadata 366 and the peer Id 368 are categorized and stored as well.
- the Peer ID 374 , the address location 372 and the “online” determination are categorized and stored on the server.
- File 351 a refers to a specific file whose HASH code is “A,” whose length in “n” bytes, and whose type is “MP 3 .”
- Peer 1 has named file 351 a as “Hotel California” in the file name 362 and described it as “Eagles” (in this case the name of the artist that recorded that song) in the metadata 366 .
- Peer 2 in contrast, has named file 351 a as “California, Hotel” in the file name 362 and described it simply as “Music File” in the metadata 366 .
- Peer 1 and Peer 2 are both currently online, so that any other peer wishing to obtain either “Hotel California” or “California, Hotel,” both of which ultimately have HASH code “A”, will have two choices as to which machine to obtain it from.
- Each peer 102 a - 102 n in the peer-to-peer network 100 maintains their own local directory of what files (e.g., 451 a - 451 c ) it has available.
- this directory may be stored as a local XML file for easy exchange with the server 110 over internet 104 .
- FIG. 4A illustrates the contents of a local directory on a specific peer.
- the local file table 450 contains a record for each file 451 a - 451 c .
- Each file may be described by its filename 452 (which may be subject to the constraints of the local operating system as to permitted characters, format, and length), a HASH ID 453 , a file size 454 , a file type 457 , file meta data 458 , and a location or folder path 459 .
- the latter facilitates the peer device to quickly locate the file on the local disk when another peer device requests it.
- Files may be added to the local peer directory whenever the user drags them into one or more specific folders on the local machine. Files may also be deleted from the local directory when they are deleted from those folders or moved out of the specific directories. Alternative implementations may use different business rules and user interface processes to specify when a file becomes available for sharing.
- FIG. 4B shows the directory synchronization process between the local peer directory 450 and the central directory 112 commencing at operation 400 .
- the selected local files to be made available for file sharing are identified.
- the HASH code of each file to be shared (if it has not already been done previously or if a file has changed for any reason) is computed in operation 403 .
- the entire local directory 450 or alternatively only changes and additions to the local directory, are transmitted to the central server 110 in operation 404 via the internet 104 .
- the central server 110 then proceeds to synchronize each individual file with the central directory 112 .
- the first central directory operation 405 checks to see if a file with that particular HASH ID already exists in the file directory 310 of data directory structure 300 (FIG. 3A). If it doesn't, operation 406 is performed to add the new file to the central directory 112 . In either case, the system now proceeds to operation 407 , which is to check to see if a record exists in the elements table 320 for this particular file and user combination. If it does not, operation 408 is performed to add the filename, meta data, and peer ID to the elements table. If an element already existed for that user ID and file ID in the elements table 320 , that record is checked for any required changes and updated as necessary. In any event, the new data coming from the peer 102 a - 102 n takes precedence over corresponding existing data in the central directory 112 .
- FIG. 4C further illustrates an alternative embodiment process of adding new files into the local directory 470 .
- This file addition process may be performed whenever a new location (a file, several files, or a folder containing several files) is added to the list of locations available for file sharing or whenever a new file is added to an existing shared folder.
- a new file is identified in operation 474
- its HASH code is immediately determined in operation 476 .
- the local directory 450 is updated in operation 478 with the particular information for that file, including its filename, HASH ID, size, and location on the peer device.
- FIG. 5 illustrates the process of searching for files according to one specific implementation.
- a requesting peer1 ( 504 ) searches for a fall or partial filename or a particular keyword
- the peer software sends the search request to the central server 502 in operation (1).
- the central server 502 processes this request and generates a list of matching files at operation ( 3 ), returning it to the requesting peer1 ( 504 ) in operation ( 5 ).
- the peer1 ( 504 ) displays only the relevant information to the user, who then selects one or more files to retrieve in operation ( 7 ).
- the requesting peer1 ( 504 ) then sends the HASH ID of one or more files to be retrieved to the server 502 at operation
- the server identifies zero, or one or more “on-line” locations (addresses) at which the requested file(s) may be found.
- the list of HASH Ids and matching locations is returned to the requesting peer1 ( 504 ) in operation ( 13 ).
- the requesting peer initiates the procedure to retrieve the selected file(s) from the locations provided by the server 502 , the operations of which are described below.
- the returned list in operation ( 13 ) may be limited to a maximum number of locations for each file, since in practice a file can usually be reliably retrieved from a relatively small number of locations.
- the server 502 may have returned the possible locations of each file with the results of operation ( 5 ). This would be beneficial by virtue of saving the second query to the server in operation ( 9 ) but would be expensive since locations would have to be found and transmitted, even for files that are not ultimately desired.
- the locations an available file may change in the intervening time between the original search and the selection of particular files to retrieve.
- the requesting peer1 ( 504 ) can choose a location from the list (assuming there is more than one location) using any number of different techniques.
- the requesting peer1 ( 504 ) can just pick the first location from the list, pick a location at random, or use some heuristic algorithm to find the “best” location to retrieve from. This may involve “pinging” each location to determine its relative distance on the network 100 from the requesting peer1 ( 504 ), or requesting a 1024 byte packet from each location to see which one can deliver bytes fastest. Such heuristics may also be useful to see which peers the requesting peer can complete a connection to. It may be impractical for the server 502 to know which peers can communicate efficiently with what other peers at any given time, since the server may not have sufficient knowledge of the topology of the network 100 or of the traffic loads that exist on it at any particular time.
- the requesting peer1 ( 504 ) has chosen a first location to start retrieving the file from (e.g., peer2 ( 506 ) in this case)
- the requesting peer1 makes a request at operation (17) to peer2 ( 506 ) for a file that has the desired HASH ID.
- Peer2 ( 506 ) identifies which file in its local directory corresponds to the desired HASH ID, for example, by performing a lookup or search in its local directory 450 at operation ( 19 ). If the requesting peer1 ( 504 ) and peer2 ( 506 ) can reliably communicate, peer2 transmits the contents of the requested file to the requesting peer1 at operation ( 21 ). Once the file has been successfully retrieved, the file is stored locally in operation ( 23 ).
- the name and meta data attached to the file at this point will be that which was originally selected in the search results in operation ( 5 ) of FIG. 5.
- This name and meta data may not necessarily be the same as the name and meta data attached to the file by peer2 ( 506 ).
- the requesting peer1 notifies the server 502 that it has a copy of the file, in this way potentially becoming a fulfilling peer for a subsequent request for this same file.
- this final message from the requesting peer can be used by the server to log successful file transfers, helping operators monitor the efficiency of the network 100 .
- the first fulfilling peer2 ( 506 ) may not answer a request for a file.
- FIG. 6B illustrates this situation, in one specific implementation. If the fulfilling peer2 ( 506 ) does not respond within a nominal timeout interval, the requesting peer1 ( 504 ) will select the next location Peer3 ( 508 ) from the list of available locations determined in operation ( 13 ) of FIG. 5, using any one of a number of heuristic algorithms to do so.
- Peer1 will send a request for the file with the specified HASH ID to Peer3 in operation ( 27 ).
- Peer3 will find that file on the local peer device in operation ( 29 ), and will transmit the contents of the requested file to Peer 1 in operation ( 31 ).
- the file is stored locally in operation ( 33 ).
- the requesting peer ( 504 ) will notify the server 502 that it now has a copy of the file.
- FIG. 6C illustrates the situation where a file may be partially retrieved from the first fulfilling peer2 ( 506 ) in the list of locations determined at operation ( 13 ) of FIG. 5.
- the first fulfilling Peer2 ( 506 ) is no longer providing the contents of the file to the requesting peer1 ( 504 ) at operation ( 21 a ).
- the requesting Peer1 ( 504 ) detects a timeout in operation ( 35 ) 1 and then decides to proceed with retrieving the remainder of the file from a second fulfilling Peer3 ( 508 ).
- the requesting peer1 ( 504 ) in this case makes a request in operation ( 37 ) for the file with HASH ID starting at a position one byte greater than the amount of the file retrieved so far from the next peer in the list of available locations; in this case Peer3 ( 508 ).
- the second fulfilling Peer3 ( 508 ) identifies which file in its local directory corresponds to the desired HASH ID at operation ( 39 )
- the new fulfilling Peer3 ( 508 ) returns the remainder of the file to the requesting peer1 ( 504 ) in operation ( 41 ).
- the application in the requesting peer1 ( 504 ) then joins the two chunks of the file together in operation ( 43 ) and stores the file locally.
- the requesting peer1 ( 504 ) will notify and update the central directory 112 of the server 502 that it now has a copy of the file.
- the requesting peer1 ( 504 ) requests different “chunks” of the desired file from two different fulfilling peers—( 506 ) and ( 508 ).
- the partial file requests in operation ( 2 a ) and operation ( 2 b ) takes the form of the HASH ID of the desired file, the starting position in the file, and the end position in the file.
- the requesting peer1 ( 504 ) may request for chunks of size “n” bytes.
- the chunk size “n” may be statically or dynamically determined based upon parameters such as, size of file to be retrieved and/or number of peers which currently have the file available.
- the first partial request in operation ( 2 a ) may be for the first “n” bytes goes to peer3 ( 508 ), starting a byte no. 1 and ending at byte no. n.
- the second partial request in operation ( 2 b ) may be for the second “n” bytes goes to peer2 ( 506 ), starting a byte no. n+1 and ending at byte no. 2 n .
- Each fulfilling peer returns the requested part of the file to the requesting peer1 ( 504 ) in operations ( 8 a ) and ( 8 b ).
- the requesting peer1 ( 504 ) reassembles the chunks of the file received from each peer in the right order into the actual file.
- the requesting peer1 ( 504 ) will then notify and update the central directory 112 of the server 502 that it now has a copy of the file which is not shown.
- a file may be retrieved from multiple fulfilling peers in parts or “chunks.” According to one specific embodiment, it may be the responsibility of the requesting peer to keep track of what chunks have already been retrieved, what chunks are currently being retrieved, and what chunks remain to be retrieved.
- FIG. 8 illustrates a “chunk map” 800 constructed by a “chunk manager” tool or application in which a file has been divided into “m” chunks. Each chunk will typically have the same size, for example “n” bytes, except for the last chunk which may have an odd size since there may be no guarantee that the requested file can be divided into a number of equal sized chunks.
- the chunk manager uses this state information to determine which chunks are to be retrieve next.
- the file is known to have been completely retrieved when every chunk is in the “AR” state.
- the chunk manager can assign the retrieval of any one chunk of a file to a worker thread (i.e. Peer1-PeerN). Multiple worker threads may be running in parallel, each retrieving a distinct chunk of the file.
- the chunk manager may employ a variety of techniques to assign chunks to retrieve and peers to retrieve from to different threads.
- the chunk manager assigns “p” chunks sequentially to “p” individual threads. Typically, p ⁇ m, the number of chunks available, although an alternative may be to use more threads than there are chunks and to simply terminate the surplus threads that are not finished when the entire file has been retrieved.
- the number of threads that can be run in parallel may be constrained by system resources available on the peer device, by operating system constraints, or for any other reason.
- FIG. 9 illustrates one specific embodiment where a chunk manager executive thread at operation ( 900 ) manages the efforts of multiple worker threads.
- the executive thread starts with initial parameters at operation ( 902 ) including a list of peers that have the file with HASH ID that is to be retrieved, as well as the chunk size “n” to be used in retrieving.
- the chunk manager may compute its own value of n based on the number of peers available and the size of the file.
- the executive thread's first task at operation ( 904 ) is to launch a number “p” of worker threads. Each worker thread starts up in operation ( 932 ) and waits for an assignment in operation ( 934 ).
- the executive thread assigns a chunk to each available worker thread in operation ( 906 ).
- Each unit of work may be characterized by the HASH ID of the file to be retrieved, the peer to retrieve it from, and the start and end positions in the file.
- Each worker thread accepts a work assignment in operation ( 936 ), and then makes a request to the assigned peer for the assigned chunk in operation ( 938 ). This request includes the HASH ID of the file and the start and end positions in the file. Meanwhile, the executive thread waits for chunks to be received in operation ( 908 ).
- a query is performed at operation ( 940 ) about whether or not the desired chunk has been completely received. If “YES”, when a worker thread has completely received a chunk, it sends that chunk or preferably, a reference to the location of the chunk in memory or on a storage device, to the chunk manager in operation ( 942 ). The chunk manager accepts the chunk at operation ( 910 ), and updates its chunk map 800 , marking a i the received chunk as having state “AR” in operation ( 912 ).
- the failure is reported to the executive manager at operation ( 944 ). This reported information will include the HASH ID of the file to be retrieved, the peer to retrieve it from, and the start and end positions in the file of the chunk not retrieved.
- the worker thread that has just finished returns to operation 934 and waits for another assignment.
- the executive thread examines its updated chunk map in operation 914 to see if there are any unassigned chunks (state “NAR”) remaining. If there are, it selects one unassigned chunks in operation ( 916 ) and assigns it to a free worker thread in operation ( 906 ).
- the executive thread may decide to select an existing assigned, but not yet fully received “ANR” chunk, for reassignment in operation ( 920 ). This decision may be made based upon a variety of factors, including the current rate of retrieving of unfinished chunks, the availability of additional worker threads or peers, or the relative retrieve speed of available peers. If an assigned, but unfinished chunk is selected for reassignment, the existing worker thread assigned to that chunk has its assignment terminated and becomes available for reassignment at operation ( 922 ). The chunk it was working on is now marked as “NAR” and is ready for reassignment in operation ( 906 ).
- a specific peer may be attached to a specific worker thread for the duration of the process. Worker threads that finish sooner may get new work assigned to them, with that new work being targeted to peers that are faster at delivering chunks of the file. Should a peer fail to deliver a chunk in a timely manner, it may be removed from the list of available peers and the thread may request a new peer to interact with.
- the delivery speed of various peers may vary over time, so that what was a fast peer at the beginning of the process becomes a slow peer towards the end or vice-versa. Since new work tends to go to threads that are finishing their work fastest, the system self-optimizes the retrieve to deliver the file as fast as possible.
- each peer may be assigned an average or nominal speed prior to the start of file retrieving. The speed of each peer would then be set to the actual speed as chunks are actually delivered. Since delivery speed may vary on a minute-by-minute basis, the most recent measurement of peer speed may be deemed to be authoritative.
- the status of identified peers as being non-responsive are updated.
- FIG. 12 illustrates one example of a user interface 1200 on the peer device according to a specific embodiment of the present invention.
- the user interface for instance, may be implemented as an application running on the Microsoft Windows operating system.
- the user interface 1200 includes a search input field 1300 where the user can search for files.
- the search term “clinton” is entered in field 1300 .
- Files that are found are displayed in a search results list 1301 .
- the user can then select one or more files from the list 1301 of search results, as shown in FIG. 14, to retrieve from other peers.
- the mpeg file “clintong.mpeg” 1400 is highlighted.
- the technique of the present invention provides improved peer-to-peer networking technology for enabling faster and more reliable downloads, using multiple peers in a round-robin or simultaneous retrieving mode, and/or being able to resume failed downloads from different peers.
- at least a portion of these features may be implemented by identifying files based on their contents rather than their file names. In this way it is possible to identify and retrieve file content from one or more identical files stored in the peer-to-peer network which have different file names and/or other metadata descriptors.
- the peer-to-peer network of the present invention includes a central directory, like Napster, but unlike Gnutella which uses a distributed directory.
- a central directory like Napster, but unlike Gnutella which uses a distributed directory.
- the technique of the present invention may be applied to both to central directory systems as well as peer-to-peer, distributed directory systems.
- the peer-to-peer file sharing techniques of the present invention may be implemented on software and/or hardware.
- they can be implemented in an operating system kernel, in a separate user process, in a library package bound into network applications, on a specially constructed machine, or on a network interface card.
- the technique of the present invention is implemented in software such as an operating system or in an application running on an operating system.
- a software or software/hardware hybrid implementation of the peer-to-peer file sharing technique of this invention may be implemented on a general-purpose programmable machine selectively activated or reconfigured by a computer program stored in memory.
- Such programmable machine may be a network device designed to handle network traffic, such as, for example, a router or a switch.
- Such network devices may have multiple network interfaces including frame relay and ISDN interfaces, for example.
- Specific examples of such network devices include routers and switches.
- the technique of the present invention may be implemented on specially configured routers or servers such as specially configured router models 1600 , 2500 , 2600 , 3600 , 4500 , 4700 , 7200 , 7500 , and 12000 available from Cisco Systems, Inc. of San Jose, Calif.
- the peer-to-peer file sharing technique of this invention may be implemented on a general-purpose network host machine such as a personal computer or workstation. Further, the invention may be at least partially implemented on a card (e.g., an interface card) for a network device or a general-purpose computing device.
- a card e.g., an interface card
- a network device 60 suitable for implementing the peer-to-peer file sharing techniques of the present invention includes a master central processing unit (CPU) 62 , interfaces 68 , and a bus 67 (e.g., a PCI bus).
- the CPU 62 may be responsible for implementing specific functions associated with the functions of a desired network device.
- the CPU 62 may be responsible for analyzing packets, encapsulating packets, forwarding packets to appropriate network devices, processing file search requests, maintaining shared file information across the peer-to-peer network, etc.
- the CPU 62 may be responsible for initiating file search requests, retrieving file content information from peer devices, performing hash coding operations on selected files, etc.
- the CPU 62 preferably accomplishes all these functions under the control of software including an operating system (e.g. Windows NT), and any appropriate applications software.
- an operating system e.g. Windows NT
- CPU 62 may include one or more processors 63 such as a processor from the Motorola family of microprocessors or the MIPS family of microprocessors. In an alternative embodiment, processor 63 is specially designed hardware for controlling the operations of network device 60 . In a specific embodiment, a memory 61 (such as nonvolatile RAM and/or ROM) also forms part of CPU 62 . However, there are many different ways in which memory could be coupled to the system. Memory block 61 may be used for a variety of purposes such as, for example, caching and/or storing data, programming instructions, etc.
- the interfaces 68 are typically provided as interface cards (sometimes referred to as “line cards”). Generally, they control the sending and receiving of data packets over the network and sometimes support other peripherals used with the network device 60 .
- the interfaces that may be provided are Ethernet interfaces, frame relay interfaces, cable interfaces, DSL interfaces, token ring interfaces, and the like.
- various very high-speed interfaces may be provided such as fast Ethernet interfaces, Gigabit Ethernet interfaces, ATM interfaces, HSSI interfaces, POS interfaces, FDDI interfaces and the like.
- these interfaces may include ports appropriate for communication with the appropriate media. In some cases, they may also include an independent processor and, in some instances, volatile RAM.
- the independent processors may control such communications intensive tasks as packet switching, media control and management. By providing separate processors for the communications intensive tasks, these interfaces allow the master microprocessor 62 to efficiently perform routing computations, network diagnostics, security functions, etc.
- FIG. 11 illustrates one specific network device of the present invention
- it is by no means the only network device architecture on which the present invention can be implemented.
- an architecture having a single processor that handles communications as well as routing computations, etc. is often used.
- other types of interfaces and media could also be used with the network device.
- network device may employ one or more memories or memory modules (such as, for example, memory block 65 ) configured to store data, program instructions for the general-purpose network operations and/or other information relating to the functionality of the peer-to-peer file sharing techniques described herein.
- the program instructions may control the operation of an operating system and/or one or more applications, for example.
- the memory or memories may also be configured to include.
- machine-readable media that include program instructions, state information, etc. for performing various operations described herein.
- machine-readable media include, but are not limited to, magnetic media such as hard disks, floppy disks, and magnetic tape; optical media such as CD-ROM disks; magneto-optical media such as floptical disks; and hardware devices that are specially configured to store and perform program instructions, such as read-only memory devices (ROM) and random access memory (RAM).
- ROM read-only memory devices
- RAM random access memory
- the invention may also be embodied in a carrier wave travelling over an appropriate medium such as airwaves, optical lines, electric lines, etc.
- program instructions include both machine code, such as produced by a compiler, and files containing higher level code that may be executed by the computer using an interpreter.
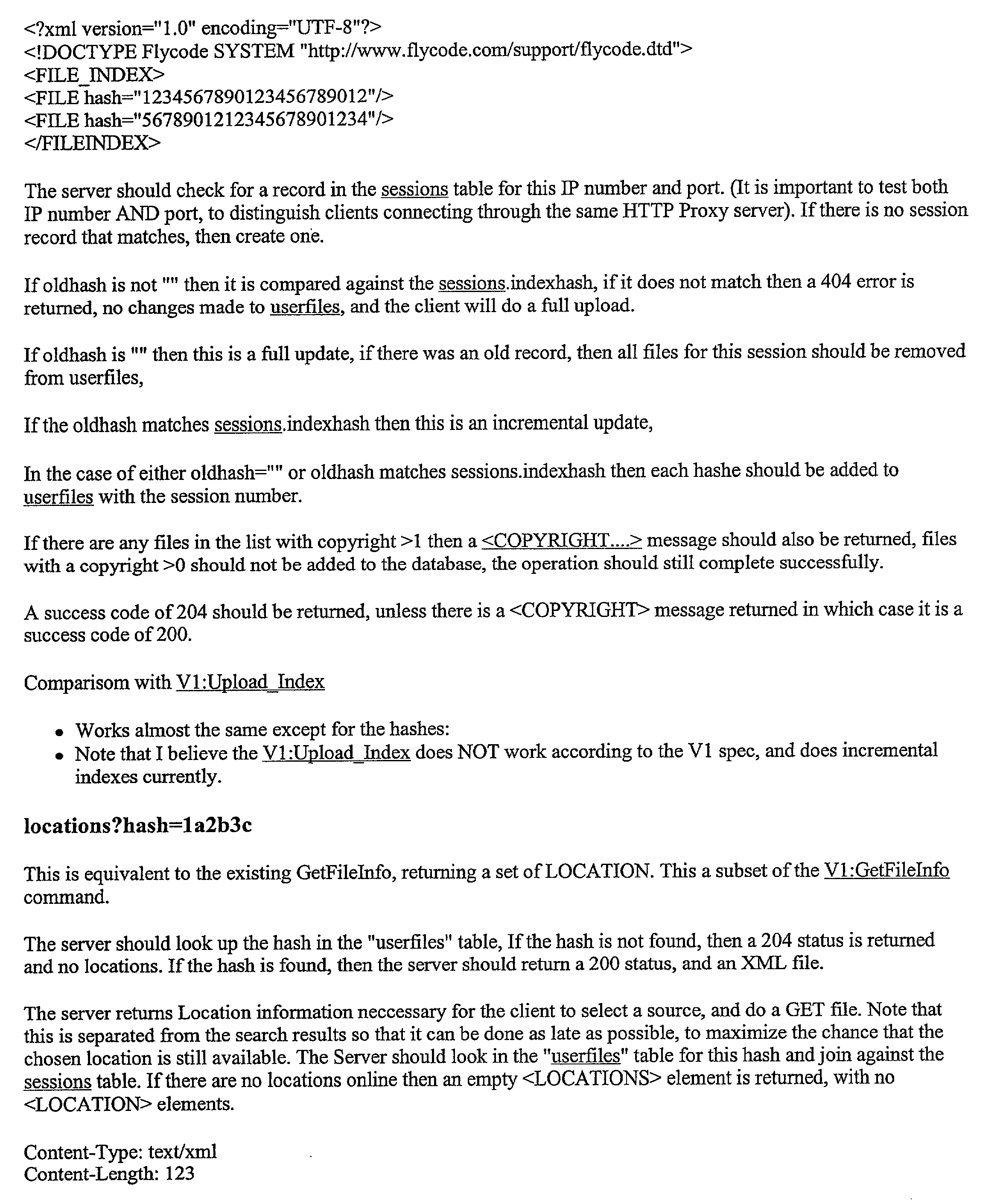
- Appendix C is entitled, “FLYCODE DATABASE SPECIFICATION”
- Appendix D is entitled, “FLYCODE VERSION 2 ARCHITECTURE—SPECIFICATION”.
Abstract
The present invention provides an improved technique for accessing information in a peer-to-peer network. According to specific embodiments of the present invention, each file accessible in the peer-to-peer network is assigned a respective hash ID or fingerprint ID which is used to describe the contents of that file. Files in the peer-to-peer network may be identified and/or accessed based upon their associated hash ID values. In this way it is possible to identify identical files stored in the peer-to-peer network which have different file names and/or other metadata descriptors. Since the content of all files having the same hash ID will be identical, an automated process may be used to retrieve the desired content from one or more of the identified files.
Description
- This application claims priority under 35 U.S.C. Section 119(e) from U.S. Provisional Patent Application No. 60/212,177, filed Jun. 16, 2000, attached hereto as Appendix E, which is incorporated herein by reference in its entirety for all purposes.
- Over the past decade, there has been an explosive growth in computer network technology, which has dramatically changed the degree and type of information available to users connected to computer networks, such as, for example, the Internet. As information becomes more accessible over local and wide area networks, new techniques for file storage and distribution are developed. Currently, most existing architectures for file distribution in a network environment utilize centralized file storage and transfer architecture, in which files are stored in central servers and accessed by individual distributed client programs. However, as the files increase in number and size, file storage and distribution from these central servers often becomes problematic.
- One type of file sharing technology which addresses some of the problems posed by centralized file storage systems relates to distributed file storage systems, such as those implemented in peer-to-peer networks. As commonly known to one having ordinary skill in the art peer-to-peer networks may be used for implementing distributed file sharing systems wherein selected files stored on each peer network device may be made accessible to other peer network devices in the peer-to-peer network. Accordingly, peer-to-peer network architectures are highly scalable, since files may be retrieved from many locations rather than just one central location (e.g., a central server).
- In recent years, there have been significant advances in peer-to-peer network technology, particularly with regard to the Internet. For example, peer-to-peer file sharing applications such as NAPSTER™ and GNUTELLA™ now provide the ability for Internet users to configure their computer systems to function as peer network devices in a peer-to-peer network implemented across the Internet. In this way, an Internet user is able to access desired files which are stored at the computer systems of other Internet users.
- While this first generation peer-to-peer architecture solved some of the problems associated with centralized file storage, it also introduced new problems such as, for example, file access, reliability, speed, security, etc. For example, using peer-to-peer file sharing applications such as NAPSTER™, shared files in the peer-to-peer network were identified and retrieved based upon their file names. Thus, for example, if a name of a file were misspelled, there was no other way of identifying the file during a search. Additionally, if a peer which was currently involved in one or more file retrieval operations went offline, the file retrieval operations would fail. The requesting user then had to discard the partial file contents and pick a new peer to download from. Consequently, very large files were virtually impossible to retrieve since few peers remained online long enough to complete such a large transfer.
- It will be appreciated that there are numerous issues relating to peer-to-peer network technology which remain to be resolved. Accordingly, continuous efforts are being undertaken to improve peer-to-peer networking technology in order to provide improved file storage, access, and distribution techniques implemented over a data network.
- According to different embodiments of the present invention, methods, systems, and computer program products are disclosed for accessing information in a peer-to-peer network. The peer-to-peer network includes a plurality of peer devices and a database accessible by at least a portion of the peer devices. Each of the peer devices is configured to store information files, and is further configured to share content from selected information files with at least a portion of the other peer devices in the network. Each shared file in the network has a respective fingerprint IID associated therewith relating to its file content.
- According to specific embodiments, files in the peer-to-peer network may be identified and/or accessed based upon their associated hash ID values. In this way it is possible to identify identical files stored in the peer-to-peer network which have different file names and/or other metadata descriptors. Additionally, since the content of all files having the same hash ID will be identical, an automated process may be used to retrieve the desired content from one or more of the identified files. For example, a user may elect to retrieve a desired file (having an associated hash ID) which may be stored at one or more remote locations in the peer-to-peer network. Rather than the user having to select a specific location for accessing and retrieving the desired file, an automated process may use the hash ID (associated with the desired file) to automatically select one or more remote locations for retrieving the desired file. According to different embodiments, the automated process may choose to retrieve the entire file contents of the desired file from a specific remote location, or may choose to receive selected portions of the file contents of the desired file from different remote locations in the peer-to-peer network. Further, if an error occurs during the file transfer process, resulting in a partial file transfer, the automated process may be configured to identify the portion(s) of the desired file which were not retrieve, and automatically select at least one different remote location for retrieving the remaining contents of the desired file.
- Additional objects, features and advantages of the various aspects of the present invention will become apparent from the following description of its preferred embodiments, which description should be taken in conjunction with the accompanying drawings.
- FIG. 1 illustrates a block diagram of peer-to-peer network which may be used for implementing the technique of the present invention in accordance with a specific embodiment of the present invention.
- FIG. 2 shows a block diagram of HASH coding of a file in accordance with a specific embodiment of the present invention.
- FIG. 3A shows a block diagram of directory data structures in accordance with a specific embodiment of the present invention.
- FIG. 3B shows a block diagram of an example of specific data stored in the directory data structures in accordance with a specific embodiment of the present invention.
- FIG. 4A shows a block diagram of an example of specific data stored in the peer directory structures in accordance with a specific embodiment of the present invention.
- FIGS. 4B and 4C illustrates flow diagrams of the directory synchronization process between a local peer directory and a central directory in accordance with a specific embodiment of the present invention.
- FIG. 5 illustrates a trace diagram of the technique for searching files in accordance with a specific embodiment of the present invention.
- FIGS. 6A-6C illustrates a trace diagram of a file retrieving technique in accordance with a specific embodiment of the present invention.
- FIG. 7 shows a trace diagram of another file retrieving technique from multiple peers in accordance with an alternative embodiment of the present invention.
- FIG. 8 shows a block diagram of a chunk map for the management of the retrieval of “chunks” of a file for the file retrieving technique in accordance with the alternative embodiment of the present invention.
- FIG. 9 illustrates a flow diagram of the chunk management technique across multiple worker threads for the file retrieving technique in accordance with the alternative embodiment of the present invention.
- FIG. 10 illustrates a flow diagram of the chunk management technique when an unresponsive peer for the file retrieving technique in accordance with the alternative embodiment of the present invention.
- FIG. 11 shows a specific embodiment of a
peer network device 60 which may be used for implementing the technique of the present invention. - FIG. 12 is a diagram of an example of a screen shot illustrating a user interface on a peer device in accordance with a specific embodiment of the present invention.
- FIG. 13 is a diagram of another example of a screen shot illustrating a user interface showing a search input field in accordance with a specific embodiment of the present invention.
- FIG. 14 is a diagram of the example of a screen shot of FIG. 13 illustrating a selection of the search input field in accordance with a specific embodiment of the present invention.
- The present invention provides an improved technique for accessing information in a peer-to-peer network. According to specific embodiments of the present invention, each file accessible in the peer-to-peer network is assigned a respective hash ID or fingerprint ID which is used to describe the contents of that file. According to one embodiment, a conventional hash or fingerprinting algorithm may be used to analyze the contents of a selected file, and generate a unique hash ID or fingerprint ID which may be used for identifying the specific contents of that file. The hashing algorithm is designed such that no two files having different file content will have the same hash ID. However, files having identical file content will have the same hash ID. In one implementation, the file name and metadata associated with a file are not included in the computation of the hash ID for that file.
- According to specific embodiments, files in the peer-to-peer network may be identified and/or accessed based upon their associated hash ID values. In this way it is possible to identify identical files stored in the peer-to-peer network which have different file names and/or other metadata descriptors. Additionally, since the content of all files having the same hash ID will be identical, an automated process may be used to retrieve the desired content from one or more of the identified files. For example, a user may elect to retrieve a desired file (having an associated hash ID) which may be stored at one or more remote locations in the peer-to-peer network. Rather than the user having to select a specific location for accessing and retrieving the desired file, an automated process may use the hash ID (associated with the desired file) to automatically select one or more remote locations for retrieving the desired file. According to different embodiments, the automated process may choose to retrieve the entire file contents of the desired file from a specific remote location, or may choose to receive selected portions of the file contents of the desired file from different remote locations in the peer-to-peer network. Further, if an error occurs during the file transfer process, resulting in a partial file transfer, the automated process may be configured to identify the portion(s) of the desired file which were not retrieve, and automatically select at least one different remote location for retrieving the remaining contents of the desired file.
- Referring now to FIG. 1, a high level view of a peer-to-
peer network 100 is illustrated in accordance with a specific embodiment of the present invention. Thenetwork 100 includes a plurality of peer network devices 102 a-102 n, and at least onecentral server system 110. According to one specific implementation, the peer devices 102 a-102 n are communicably connected to each other and to thecentral server 110 via theInternet 104. The peers may communicate with each other and the server via the http protocol or via a private protocol, the former being preferable to minimize the effects of various firewalls that may exist between any given peer device and theInternet 104. - The
server 110 preferably includes software or firmware that handles communication between the peer devices 102 a-102 n and thecentral server 110, and that performs specific logical operations on thedirectory 112 on the server. According to one specific implementation, thedirectory 112 may be stored in a single relational database, but permanent storage may also be accomplished by an object database, a directory server, or multiple databases. -
Files 202 that are to be shared are only stored on the peer devices 102 a-102 n. Thedirectory 112 stores information about the files (e.g., HASH ID, filename, metadata, size, type, etc.) but not their contents. In addition, thedirectory 112 stores information about the peer devices themselves (e.g., Peer ID) and most importantly, which peer devices thefiles 202 exist on at any given time. - Briefly, it will be appreciated that
file 202 may contain any type of stored information. These include, for example, jpeg, mpeg and mp3. - Turning now to FIG. 2, the unique footprinting of a
file 202 is illustrated in accordance with one specific embodiment of the present invention. In particular, the process by which afile 202 may be uniquely identified is through the application ofHASH code 204. Each peer device 102 a-102 n that wishes to publish a file on the peer-to-peer network 100 first computes theHASH code 204 of that file. TheHASH code 204 may be computed via conventional algorithms which generate a unique identifier based upon the content of a particular file. Examples of fingerprinting or hash code algorithm which may be used in conjunction with the technique of the present invention include, MD5 (described in RFC 1321, and attached hereto has Appendix A), and Keyed SHAL (described in RFC 2841, and attached hereto has Appendix B). Each of these references is incorporated herein by reference in its entirety for all purposes. - According to one specific implementation, MD5 (See Appendix A) may be used to guarantee that the HASH code is unique for each different file, even when two files differ by as little as one bit. Other algorithms may also be used such as, for example, Keyed SHAI (See Appendix B) which mathematically characterizes the audio or visual waveforms of the content of the file and creates a unique code representation of that file. According to a specific embodiment, the filename, time/date stamps, and any other meta-data about the file are not included in the computation of the HASH code. Different peers, or even the same peer, can refer to or describe what is in fact the same file content by different names. The desired files are more likely to be found, as different users may search for files using different names, descriptions, or other characteristics, although the file content is identical. Such unique ID association allows each user to name and describe a given file in the manner most relevant to them.
- According to one specific implementation, the
central directory data 300 may be stored in a relational database. FIG. 3A illustrates three of the central tables in the directory data structures 300: the file directory table 310; the elements table 320; and the users table 330. The file directory table 310, for example, contains information about the file contents only, including the HASH code or ID, the size, and the type (video, music, image, etc . . . ). Other information specific to the contents of the file may also be stored in this table. The elements table 320, on the other hand, contains descriptive information or meta data about each file as entered and maintained by each individual user. This elements table 320 also includes foreign keys Hash code ID and Peer device ID that points to thefiles 310 and users tables 330, respectively. The users table 330 contains information about each user and his/her peer device 102 a-102 n. The users table also maintains the systems current knowledge as to which user is currently connected to the peer-to-peer network 100. - According to one specific embodiment, the relationship between the three tables of FIG. 3A can be defined such that each user can have many files and each file can be owned by many users. In addition, each user can have their own individual description of each file and may possibly describe the same file in more than one way, although the file content, and thus, the HASH coding are identical.
- In one embodiment, should a file be deleted by every user that ever had them, there will be no record in the elements table 320 of that file but a record of that file's existence will remain in the file directory table 310.
- As best viewed in FIG. 3B, a specific example is diagrammed which illustrates how a number of files, their descriptions, and the users that own them might be represented in the
directory database 112. In file directory table 350, for instance, theHASH ID 354, thefile size 356 andfile type 358 are categorized and stored in thecentral server 110 for each particular file 351 a-351 c. Correspondingly, in the elements table 360, theHASH ID 364, thefile name 362, themetadata 366 and thepeer Id 368 are categorized and stored as well. Finally, in user table 370, thePeer ID 374, theaddress location 372 and the “online” determination, are categorized and stored on the server. -
File 351 a, for example, refers to a specific file whose HASH code is “A,” whose length in “n” bytes, and whose type is “MP3.” Two users, “Peer 1” and “Peer 2” each have a copy of thisfile 351 a.Peer 1 has namedfile 351 a as “Hotel California” in thefile name 362 and described it as “Eagles” (in this case the name of the artist that recorded that song) in themetadata 366.Peer 2, in contrast, has namedfile 351 a as “California, Hotel” in thefile name 362 and described it simply as “Music File” in themetadata 366.Peer 1 andPeer 2 are both currently online, so that any other peer wishing to obtain either “Hotel California” or “California, Hotel,” both of which ultimately have HASH code “A”, will have two choices as to which machine to obtain it from. - Each peer 102 a-102 n in the peer-to-
peer network 100 maintains their own local directory of what files (e.g., 451 a-451 c) it has available. In one particular embodiment, this directory may be stored as a local XML file for easy exchange with theserver 110 overinternet 104. FIG. 4A illustrates the contents of a local directory on a specific peer. The local file table 450 contains a record for each file 451 a-451 c. Each file may be described by its filename 452 (which may be subject to the constraints of the local operating system as to permitted characters, format, and length), a HASH ID 453, afile size 454, afile type 457, filemeta data 458, and a location orfolder path 459. The latter facilitates the peer device to quickly locate the file on the local disk when another peer device requests it. - Other files may be added to the local peer directory whenever the user drags them into one or more specific folders on the local machine. Files may also be deleted from the local directory when they are deleted from those folders or moved out of the specific directories. Alternative implementations may use different business rules and user interface processes to specify when a file becomes available for sharing.
- To determine what files are available and where they may be available in the
central directory 112 so that they can readily be searched by any peer 102 a-102 n, a directory synchronization process is necessary. Applying this technique, it may be the responsibility of each peer 102 a-102 n in thenetwork 100 to send their list of files they have available, at least periodically, along with any changes to that list as they occur, to thecentral directory 112. - Referring now to one specific implementation, FIG. 4B shows the directory synchronization process between the
local peer directory 450 and thecentral directory 112 commencing atoperation 400. Initially atoperation 402, the selected local files to be made available for file sharing are identified. The HASH code of each file to be shared (if it has not already been done previously or if a file has changed for any reason) is computed inoperation 403. Once the HASH code for each new or changed file has been computed, the entirelocal directory 450, or alternatively only changes and additions to the local directory, are transmitted to thecentral server 110 inoperation 404 via theinternet 104. Thecentral server 110 then proceeds to synchronize each individual file with thecentral directory 112. The firstcentral directory operation 405 checks to see if a file with that particular HASH ID already exists in thefile directory 310 of data directory structure 300 (FIG. 3A). If it doesn't,operation 406 is performed to add the new file to thecentral directory 112. In either case, the system now proceeds tooperation 407, which is to check to see if a record exists in the elements table 320 for this particular file and user combination. If it does not,operation 408 is performed to add the filename, meta data, and peer ID to the elements table. If an element already existed for that user ID and file ID in the elements table 320, that record is checked for any required changes and updated as necessary. In any event, the new data coming from the peer 102 a-102 n takes precedence over corresponding existing data in thecentral directory 112. - FIG. 4C further illustrates an alternative embodiment process of adding new files into the local directory 470. This file addition process may be performed whenever a new location (a file, several files, or a folder containing several files) is added to the list of locations available for file sharing or whenever a new file is added to an existing shared folder. Whenever a new file is identified in operation 474, its HASH code is immediately determined in operation 476. The
local directory 450 is updated in operation 478 with the particular information for that file, including its filename, HASH ID, size, and location on the peer device. - FIG. 5 illustrates the process of searching for files according to one specific implementation. When a requesting peer1 ( 504) searches for a fall or partial filename or a particular keyword, the peer software sends the search request to the
central server 502 in operation (1). Thecentral server 502 processes this request and generates a list of matching files at operation (3), returning it to the requesting peer1 (504) in operation (5). The peer1 (504) displays only the relevant information to the user, who then selects one or more files to retrieve in operation (7). The requesting peer1 (504) then sends the HASH ID of one or more files to be retrieved to theserver 502 at operation In operation (11), the server identifies zero, or one or more “on-line” locations (addresses) at which the requested file(s) may be found. The list of HASH Ids and matching locations is returned to the requesting peer1 (504) in operation (13). Finally, in operation (15), the requesting peer initiates the procedure to retrieve the selected file(s) from the locations provided by theserver 502, the operations of which are described below. - In one embodiment, the returned list in operation ( 13) may be limited to a maximum number of locations for each file, since in practice a file can usually be reliably retrieved from a relatively small number of locations. In an alternative embodiment, the
server 502 may have returned the possible locations of each file with the results of operation (5). This would be beneficial by virtue of saving the second query to the server in operation (9) but would be expensive since locations would have to be found and transmitted, even for files that are not ultimately desired. In addition, the locations an available file may change in the intervening time between the original search and the selection of particular files to retrieve. - Once a list of locations for a file has been identified, the requesting peer1 ( 504) can choose a location from the list (assuming there is more than one location) using any number of different techniques. The requesting peer1 (504) can just pick the first location from the list, pick a location at random, or use some heuristic algorithm to find the “best” location to retrieve from. This may involve “pinging” each location to determine its relative distance on the
network 100 from the requesting peer1 (504), or requesting a 1024 byte packet from each location to see which one can deliver bytes fastest. Such heuristics may also be useful to see which peers the requesting peer can complete a connection to. It may be impractical for theserver 502 to know which peers can communicate efficiently with what other peers at any given time, since the server may not have sufficient knowledge of the topology of thenetwork 100 or of the traffic loads that exist on it at any particular time. - In FIG. 6A, in accordance with one specific embodiment, once the requesting peer1 ( 504) has chosen a first location to start retrieving the file from (e.g., peer2 (506) in this case), the requesting peer1 makes a request at operation (17) to peer2 (506) for a file that has the desired HASH ID. Peer2 (506) then identifies which file in its local directory corresponds to the desired HASH ID, for example, by performing a lookup or search in its
local directory 450 at operation (19). If the requesting peer1 (504) and peer2 (506) can reliably communicate, peer2 transmits the contents of the requested file to the requesting peer1 at operation (21). Once the file has been successfully retrieved, the file is stored locally in operation (23). - The name and meta data attached to the file at this point will be that which was originally selected in the search results in operation ( 5) of FIG. 5. This name and meta data may not necessarily be the same as the name and meta data attached to the file by peer2 (506). Finally, in operation (24), the requesting peer1 notifies the
server 502 that it has a copy of the file, in this way potentially becoming a fulfilling peer for a subsequent request for this same file. Furthermore, this final message from the requesting peer can be used by the server to log successful file transfers, helping operators monitor the efficiency of thenetwork 100. - In some situations, such as the presence of firewalls, proxy servers, or other network devices, or the fact that the fulfilling peer is no longer online, the first fulfilling peer2 ( 506) may not answer a request for a file. FIG. 6B illustrates this situation, in one specific implementation. If the fulfilling peer2 (506) does not respond within a nominal timeout interval, the requesting peer1 (504) will select the next location Peer3 (508) from the list of available locations determined in operation (13) of FIG. 5, using any one of a number of heuristic algorithms to do so. Assuming in this case that Peer1 (504) and Peer3 (508) can communicate, Peer1 will send a request for the file with the specified HASH ID to Peer3 in operation (27). Next, Peer3 will find that file on the local peer device in operation (29), and will transmit the contents of the requested file to
Peer 1 in operation (31). Once the file has been successfully retrieved, the file is stored locally in operation (33). Finally, in operation (34), the requesting peer (504) will notify theserver 502 that it now has a copy of the file. - According to one specific implementation, the retrieving of a file from one fulfilling peer that is interrupted for any reason may be resumed from another peer that is online and that has that file. FIG. 6C illustrates the situation where a file may be partially retrieved from the first fulfilling peer2 ( 506) in the list of locations determined at operation (13) of FIG. 5. After a time, the first fulfilling Peer2 (506) is no longer providing the contents of the file to the requesting peer1 (504) at operation (21 a). The requesting Peer1 (504) detects a timeout in operation (35)1 and then decides to proceed with retrieving the remainder of the file from a second fulfilling Peer3 (508). The requesting peer1 (504) in this case makes a request in operation (37) for the file with HASH ID starting at a position one byte greater than the amount of the file retrieved so far from the next peer in the list of available locations; in this case Peer3 (508).
- It is crucial that the file contents on the first fulfilling Peer2 ( 506) and the second fulfilling Peer3 (508) corresponding to HASH ID be identical in every respect, since otherwise these parts of files may not fit together correctly and result in a damaged or corrupted final file. This is why it is essential to pick a HASH function that will uniquely create a unique HASH code from a file's contents.
- Once the second fulfilling Peer3 ( 508) identifies which file in its local directory corresponds to the desired HASH ID at operation (39), the new fulfilling Peer3 (508) returns the remainder of the file to the requesting peer1 (504) in operation (41). The application in the requesting peer1 (504) then joins the two chunks of the file together in operation (43) and stores the file locally. In operation (44), the requesting peer1 (504) will notify and update the
central directory 112 of theserver 502 that it now has a copy of the file. - In an alternative embodiment, when the relative ability of multiple peers to deliver files is not known, it can be advantageous to retrieve different parts of a single file from multiple peers 102 a-102 n simultaneously. This may be particularly true if the requesting peer has a faster connection than most of the fulfilling peers since the file can be retrieved faster than any single fulfilling peer can deliver it.
- According to one specific implementation shown in FIG. 7, the requesting peer1 ( 504) requests different “chunks” of the desired file from two different fulfilling peers—(506) and (508). The partial file requests in operation (2 a) and operation (2 b) takes the form of the HASH ID of the desired file, the starting position in the file, and the end position in the file. In this example, the requesting peer1 (504) may request for chunks of size “n” bytes. The chunk size “n” may be statically or dynamically determined based upon parameters such as, size of file to be retrieved and/or number of peers which currently have the file available. The first partial request in operation (2 a) may be for the first “n” bytes goes to peer3 (508), starting a byte no. 1 and ending at byte no. n. The second partial request in operation (2 b) may be for the second “n” bytes goes to peer2 (506), starting a byte no. n+1 and ending at byte no. 2 n. Each fulfilling peer returns the requested part of the file to the requesting peer1 (504) in operations (8 a) and (8 b). In
operation 43, the requesting peer1 (504) reassembles the chunks of the file received from each peer in the right order into the actual file. The requesting peer1 (504) will then notify and update thecentral directory 112 of theserver 502 that it now has a copy of the file which is not shown. - A file may be retrieved from multiple fulfilling peers in parts or “chunks.” According to one specific embodiment, it may be the responsibility of the requesting peer to keep track of what chunks have already been retrieved, what chunks are currently being retrieved, and what chunks remain to be retrieved. FIG. 8 illustrates a “chunk map” 800 constructed by a “chunk manager” tool or application in which a file has been divided into “m” chunks. Each chunk will typically have the same size, for example “n” bytes, except for the last chunk which may have an odd size since there may be no guarantee that the requested file can be divided into a number of equal sized chunks. According to this specific embodiment, each chunk exists in one of three possible states: AR=Assigned and Retrieved; ANR=Assigned and Not Retrieved; and NAR=Not Assigned and Not Retrieved. The chunk manager uses this state information to determine which chunks are to be retrieve next. The file is known to have been completely retrieved when every chunk is in the “AR” state.
- In one specific example, a file whose size is 1.45 MB, for instance, is being requested. If the system has been configured to use a value of n=100 kb, there will be m=15 chunks, each of
size 100 kb, except for the 15th chunk, whose size will be 50 kb. - According to one specific implementation, the chunk manager can assign the retrieval of any one chunk of a file to a worker thread (i.e. Peer1-PeerN). Multiple worker threads may be running in parallel, each retrieving a distinct chunk of the file. The chunk manager may employ a variety of techniques to assign chunks to retrieve and peers to retrieve from to different threads. In one embodiment, the chunk manager assigns “p” chunks sequentially to “p” individual threads. Typically, p≦m, the number of chunks available, although an alternative may be to use more threads than there are chunks and to simply terminate the surplus threads that are not finished when the entire file has been retrieved. The number of threads that can be run in parallel may be constrained by system resources available on the peer device, by operating system constraints, or for any other reason.
- FIG. 9 illustrates one specific embodiment where a chunk manager executive thread at operation ( 900) manages the efforts of multiple worker threads. The executive thread starts with initial parameters at operation (902) including a list of peers that have the file with HASH ID that is to be retrieved, as well as the chunk size “n” to be used in retrieving. Alternatively, the chunk manager may compute its own value of n based on the number of peers available and the size of the file.
- The executive thread's first task at operation ( 904) is to launch a number “p” of worker threads. Each worker thread starts up in operation (932) and waits for an assignment in operation (934).
- The executive thread assigns a chunk to each available worker thread in operation ( 906). Each unit of work may be characterized by the HASH ID of the file to be retrieved, the peer to retrieve it from, and the start and end positions in the file. Each worker thread accepts a work assignment in operation (936), and then makes a request to the assigned peer for the assigned chunk in operation (938). This request includes the HASH ID of the file and the start and end positions in the file. Meanwhile, the executive thread waits for chunks to be received in operation (908).
- A query is performed at operation ( 940) about whether or not the desired chunk has been completely received. If “YES”, when a worker thread has completely received a chunk, it sends that chunk or preferably, a reference to the location of the chunk in memory or on a storage device, to the chunk manager in operation (942). The chunk manager accepts the chunk at operation (910), and updates its chunk map 800, marking a i the received chunk as having state “AR” in operation (912).
- If the query performed at operation ( 940) is answered with a “NO”, the failure is reported to the executive manager at operation (944). This reported information will include the HASH ID of the file to be retrieved, the peer to retrieve it from, and the start and end positions in the file of the chunk not retrieved.
- At this point, regardless of the query at operation ( 940), the worker thread that has just finished returns to
operation 934 and waits for another assignment. The executive thread examines its updated chunk map inoperation 914 to see if there are any unassigned chunks (state “NAR”) remaining. If there are, it selects one unassigned chunks in operation (916) and assigns it to a free worker thread in operation (906). - If there are no unassigned chunks, the executive thread may decide to select an existing assigned, but not yet fully received “ANR” chunk, for reassignment in operation ( 920). This decision may be made based upon a variety of factors, including the current rate of retrieving of unfinished chunks, the availability of additional worker threads or peers, or the relative retrieve speed of available peers. If an assigned, but unfinished chunk is selected for reassignment, the existing worker thread assigned to that chunk has its assignment terminated and becomes available for reassignment at operation (922). The chunk it was working on is now marked as “NAR” and is ready for reassignment in operation (906).
- In one specific embodiment, a specific peer may be attached to a specific worker thread for the duration of the process. Worker threads that finish sooner may get new work assigned to them, with that new work being targeted to peers that are faster at delivering chunks of the file. Should a peer fail to deliver a chunk in a timely manner, it may be removed from the list of available peers and the thread may request a new peer to interact with. The delivery speed of various peers may vary over time, so that what was a fast peer at the beginning of the process becomes a slow peer towards the end or vice-versa. Since new work tends to go to threads that are finishing their work fastest, the system self-optimizes the retrieve to deliver the file as fast as possible.
- By way of example, in the previously discussed file of FIG. 8 where the 1.45 MB file is divided into m=fifteen (15) chunks of n=100 kb (the 15th chunk being 50 kb), ten (10) peers are online and have the file with HASH ID available. The executive manager decides to use p=eight (8) worker threads to retrieve the file. If every chunk retrieved is successful and is performed in the same amount of time, each thread will retrieve two 100 kb chunks, except for the 8th thread, which will only retrieve one 100 kb chunk, and for the 7th thread, which will retrieve a 100 kb chunk followed by a 50 kb chunk.
- In practice, some threads will be assigned to unresponsive peers and will fail to retrieve their chunks the first time. The executive thread may mark these peers as unresponsive and assign new peers to the available threads. Furthermore, some peers may be much faster than others at retrieving chunks. In that case, they will become available for retrieving new chunks earlier, the result being that one thread may retrieve five (5) or six (6) chunks while the remainder only retrieve one or two.
- Referring now to FIG. 10, one specific embodiment of a possible process for dealing with peers that fail to respond for chunks of a file is illustrated. The executive thread receives a failure notice from a worker thread in operation ( 1002). It then sets the measured speed of the corresponding peer to zero (0) in operation (1004). Subsequent peer assignments may use a ranking of measured speeds to pick the fastest available peers rather than the slower, or non-responsive ones. According to a specific embodiment, each peer may be assigned an average or nominal speed prior to the start of file retrieving. The speed of each peer would then be set to the actual speed as chunks are actually delivered. Since delivery speed may vary on a minute-by-minute basis, the most recent measurement of peer speed may be deemed to be authoritative. At operation (1006) the status of identified peers as being non-responsive are updated.
- FIG. 12 illustrates one example of a
user interface 1200 on the peer device according to a specific embodiment of the present invention. The user interface, for instance, may be implemented as an application running on the Microsoft Windows operating system. - In one example, as viewed in FIG. 13, the
user interface 1200 includes asearch input field 1300 where the user can search for files. In this example the search term “clinton” is entered infield 1300. Files that are found are displayed in a search resultslist 1301. - The user can then select one or more files from the
list 1301 of search results, as shown in FIG. 14, to retrieve from other peers. In this instance, the mpeg file “clintong.mpeg” 1400 is highlighted. - It will be appreciated that the technique of the present invention provides improved peer-to-peer networking technology for enabling faster and more reliable downloads, using multiple peers in a round-robin or simultaneous retrieving mode, and/or being able to resume failed downloads from different peers. According to a specific embodiment, at least a portion of these features may be implemented by identifying files based on their contents rather than their file names. In this way it is possible to identify and retrieve file content from one or more identical files stored in the peer-to-peer network which have different file names and/or other metadata descriptors.
- According to a specific embodiment, the peer-to-peer network of the present invention includes a central directory, like Napster, but unlike Gnutella which uses a distributed directory. However, it will be appreciated that the technique of the present invention may be applied to both to central directory systems as well as peer-to-peer, distributed directory systems.
- Other Embodiments
- Generally, the peer-to-peer file sharing techniques of the present invention may be implemented on software and/or hardware. For example, they can be implemented in an operating system kernel, in a separate user process, in a library package bound into network applications, on a specially constructed machine, or on a network interface card. In a specific embodiment of this invention, the technique of the present invention is implemented in software such as an operating system or in an application running on an operating system.
- A software or software/hardware hybrid implementation of the peer-to-peer file sharing technique of this invention may be implemented on a general-purpose programmable machine selectively activated or reconfigured by a computer program stored in memory. Such programmable machine may be a network device designed to handle network traffic, such as, for example, a router or a switch. Such network devices may have multiple network interfaces including frame relay and ISDN interfaces, for example. Specific examples of such network devices include routers and switches. For example, the technique of the present invention may be implemented on specially configured routers or servers such as specially configured router models 1600, 2500, 2600, 3600, 4500, 4700, 7200, 7500, and 12000 available from Cisco Systems, Inc. of San Jose, Calif. A general architecture for some of these machines will appear from the description given below. In an alternative embodiment, the peer-to-peer file sharing technique of this invention may be implemented on a general-purpose network host machine such as a personal computer or workstation. Further, the invention may be at least partially implemented on a card (e.g., an interface card) for a network device or a general-purpose computing device.
- Referring now to FIG. 11, a
network device 60 suitable for implementing the peer-to-peer file sharing techniques of the present invention includes a master central processing unit (CPU) 62, interfaces 68, and a bus 67 (e.g., a PCI bus). When acting under the control of appropriate software or firmware, theCPU 62 may be responsible for implementing specific functions associated with the functions of a desired network device. For example, when configured as a server device, theCPU 62 may be responsible for analyzing packets, encapsulating packets, forwarding packets to appropriate network devices, processing file search requests, maintaining shared file information across the peer-to-peer network, etc. Alternatively, when configured as a peer network device, theCPU 62 may be responsible for initiating file search requests, retrieving file content information from peer devices, performing hash coding operations on selected files, etc. TheCPU 62 preferably accomplishes all these functions under the control of software including an operating system (e.g. Windows NT), and any appropriate applications software. -
CPU 62 may include one ormore processors 63 such as a processor from the Motorola family of microprocessors or the MIPS family of microprocessors. In an alternative embodiment,processor 63 is specially designed hardware for controlling the operations ofnetwork device 60. In a specific embodiment, a memory 61 (such as nonvolatile RAM and/or ROM) also forms part ofCPU 62. However, there are many different ways in which memory could be coupled to the system.Memory block 61 may be used for a variety of purposes such as, for example, caching and/or storing data, programming instructions, etc. - The
interfaces 68 are typically provided as interface cards (sometimes referred to as “line cards”). Generally, they control the sending and receiving of data packets over the network and sometimes support other peripherals used with thenetwork device 60. Among the interfaces that may be provided are Ethernet interfaces, frame relay interfaces, cable interfaces, DSL interfaces, token ring interfaces, and the like. In addition, various very high-speed interfaces may be provided such as fast Ethernet interfaces, Gigabit Ethernet interfaces, ATM interfaces, HSSI interfaces, POS interfaces, FDDI interfaces and the like. Generally, these interfaces may include ports appropriate for communication with the appropriate media. In some cases, they may also include an independent processor and, in some instances, volatile RAM. The independent processors may control such communications intensive tasks as packet switching, media control and management. By providing separate processors for the communications intensive tasks, these interfaces allow themaster microprocessor 62 to efficiently perform routing computations, network diagnostics, security functions, etc. - Although the system shown in FIG. 11 illustrates one specific network device of the present invention, it is by no means the only network device architecture on which the present invention can be implemented. For example, an architecture having a single processor that handles communications as well as routing computations, etc. is often used. Further, other types of interfaces and media could also be used with the network device.
- Regardless of network device's configuration, it may employ one or more memories or memory modules (such as, for example, memory block 65) configured to store data, program instructions for the general-purpose network operations and/or other information relating to the functionality of the peer-to-peer file sharing techniques described herein. The program instructions may control the operation of an operating system and/or one or more applications, for example. The memory or memories may also be configured to include.
- Because such information and program instructions may be employed to implement the systems/methods described herein, the present invention relates to machine readable media that include program instructions, state information, etc. for performing various operations described herein. Examples of machine-readable media include, but are not limited to, magnetic media such as hard disks, floppy disks, and magnetic tape; optical media such as CD-ROM disks; magneto-optical media such as floptical disks; and hardware devices that are specially configured to store and perform program instructions, such as read-only memory devices (ROM) and random access memory (RAM). The invention may also be embodied in a carrier wave travelling over an appropriate medium such as airwaves, optical lines, electric lines, etc. Examples of program instructions include both machine code, such as produced by a compiler, and files containing higher level code that may be executed by the computer using an interpreter.
- Additional embodiments of the present invention are described in Appendix C and Appendix D to the present application, each of which is incorporated herein by reference in its entirety for all purposes. Appendix C is entitled, “FLYCODE DATABASE SPECIFICATION”, and Appendix D is entitled, “
FLYCODE VERSION 2 ARCHITECTURE—SPECIFICATION”. - Although several preferred embodiments of this invention have been described in detail herein with reference to the accompanying drawings, it is to be understood that the invention is not limited to these precise embodiments, and that various changes and modifications may be effected therein by one skilled in the art without departing from the scope of spirit of the invention as defined in the appended claims.
Claims (87)
1. A method for accessing information in a peer-to-peer network, the peerto-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, the method comprising:
selecting a first information file;
generating, using fingerprinting algorithm, a first fingerprint ID relating to the content of the first information file; and
identifying the first information file using the first fingerprint ID.
2. The method of claim 1 wherein the fingerprinting algorithm corresponds to an MD5 Message-Digest algorithm.
3. The method of claim 1 wherein the fingerprinting algorithm corresponds to a Secure Hash Algorithm (SHA1).
4. The method of claim 1 wherein the first information file is stored at a first peer device, and wherein the first information file has an associated first filename, the method comprising:
storing the first filename and first fingerprint ID at the first peer device.
5. The method of claim 4 further comprising: transmitting the first filename and the first fingerprint ID to the database system for storage therein.
6. The method of claim 5 wherein the database system corresponds to a remote database system.
7. The method of claim 1 further comprising:
selecting a second information file having content identical to the first information file;
applying the fingerprinting algorithm to the content of the second information file to thereby generate an identical first fingerprint ID to that of the first information file; and
identifying both the first and the second information file using the first unique fingerprint ID.
8. The method of claim 7 wherein the first information file is stored at a first peer device, and has a first associated filename, and wherein the second information file is stored at a second peer device, and has a has second associated filename, the method further comprising:
storing the first associated filename and first fingerprint ID associated with the first information file in the database system; and
storing the second associated filename and first fingerprint ID associated with the second information file in the database system.
9. A method for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective fingerprint ID associated therewith relating to its file content, the method comprising:
transmitting a first message to the database system, the first message including a search request for locating files in the network which match a first search string; and
receiving a first response from the database system, the first response including first information relating to identified files stored in the network which match the first search string;
the first information further including an associated fingerprint ID for each identified file.
10. The method of claim 9 further comprising:
transmitting a second message to the database system, the second message including a first fingerprint ID selected from the first information; and
receiving a second response from the database system in response to the second message;
the second response including second information, the second information including at least one network address corresponding to at least one peer device that has been identified as having access to at least one file corresponding to the first fingerprint ID.
11. The method of claim 10 further comprising:
transmitting a third message to a first peer device of the at least one peer devices, the third message corresponding to a request to retrieve a first file identified by the first fingerprint ID.
12. The method of claim 11 wherein the third message includes the first fingerprint ID.
13. The method of claim 11 further comprising:
receiving at least a portion of the file content of the first file from the first peer device in response to the third message.
14. A method for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective fingerprint ID associated therewith relating to its file content, the method comprising:
transmitting a first message to a first peer device, the first message corresponding to a request to retrieve a first file identified by a first fingerprint ID, wherein the first message includes the first fingerprint ID, and wherein the first fingerprint ID is different than a filename associated with the first file; and
receiving a first portion of the file content of the first file from the first peer device in response to the first message.
15. The method of claim 14 further comprising:
detecting a failure in a file transfer process associated with the first peer device;
identifying a second portion of the first file content which has not been received; and
transmitting a second message to a second peer device, the second message corresponding to a request to retrieve the second portion of the first file content identified by the first fingerprint ID, wherein the second message includes the first fingerprint ID.
16. A method for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the method comprising:
receiving file information from selected peer devices, the file information relating to shared files stored at each of the selected peer devices;
the file information including a filename for each shared file, and including a HASH ID for each shared file;
storing the file information in at least one data structure at the database system; and
identifying a desired shared file in the network using its associated HASH ID.
17. The method of claim 16 further comprising identifying an identity of a peer device using a selected HASH ID;
wherein the identified peer device has been identified as storing a file having an associated HASH ID which matches the selected HASH ID.
18. The method of claim 16 further comprising identifying a network address of a first peer device using a selected HASH ID;
wherein the first peer device has been identified as storing a file having an associated HASH ID which matches the selected HASH ID.
19. A method for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the method comprising:
receiving a first message from a first peer device, the first message including a search request for locating files in the network which match a first search string;
generating a first response to the first message, the response including a first list of file records relating to files stored in the network which match the first search string, wherein each file record includes an associated HASH ID and an associated filename; and
providing the first list of file records to the first peer device.
20. The method of claim 19 further comprising:
excluding from the first list of file records duplicate records in which multiple file records have the same associated HASH ID and filename.
21. The method of claim 19 further comprising:
receiving a second message from the first peer device in response to the first response, the second message including at least one HASH ID;
identifying, using said at least one HASH ID, at least one network address corresponding to at least one peer device which has been identified as storing at least one file corresponding to the at least one HASH ID; and
providing, to the first peer device, a second response, the second response including address information which includes at least a portion of the at least one identified network addresses.
22. A method for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the method comprising:
identifying a first network addresses corresponding to a first peer device which has been identified as storing a first information file associated with a first HASH ID;
identifying a second network addresses corresponding to a second peer device which has been identified as storing a second information file associated with the first HASH ID;
transmitting a first message to the first peer device requesting a first portion of file content of the first information file from the first peer device; and
transmitting a second message to the second peer device requesting a second portion of file content of the second information file from the second peer device.
23. The method of claim 22 wherein the first and second messages each include the first HASH ID.
24. The method of claim 22 wherein the first and second messages are initiated at substantially a same time
25. The method of claim 22 wherein the requesting of the first portion of file content from the first peer device occurs concurrently with the requesting of the second portion of file content from the second peer device.
26. The method of claim 22 further comprising:
receiving the first portion of file content from the first peer device;
receiving the second portion of file content from the second peer device;
generating a third information file which includes the first and second portion of file content, wherein the file content of the third information file is identical to the file content of the first information file.
27. The method of claim 22 further comprising:
detecting a failure in a file transfer process associated with the first peer device;
identifying a third network addresses corresponding to a third peer device which has been identified as storing a third information file associated with the first HASH ID;
transmitting a third message to the third peer device, the third message corresponding to a request to retrieve the first portion of file content from the third information file.
28. The method of claim 22 wherein the first portion of file content corresponds to a first chunk of bytes 1 to N of the first information file; and
wherein the second portion of file content corresponds to a second chunk of bytes N+1 to 2N of the second information file.
29. A method for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the method comprising:
requesting from a first plurality of peer devices a respective portion of file content from a respective information file, each respective information file being identified as having identical file content and having an identical first HASH ID being associated therewith.
30. The method of claim 29 further comprising:
receiving from at least a portion of the first plurality of peer devices respective portions of file content from the respective information file; and
reconstructing the respective portions of file content to assemble a requested information file having file content identical to that corresponding to the first HASH ID being associated therewith.
31. The method of claim 29 further comprising:
before requesting a respective portion, creating a content map of the file content associated with the first HASH ID, said content map parceling the file content into respective portions from 1 to M.
32. The method of claim 31 further comprising:
assigning at least one respective portion, from 1 to M, to a first peer device of the first plurality of peer devices to request retrieval thereof.
33. The method of claim 32 further comprising:
receiving from the first peer device the one respective portion, from 1 to M, of file content from the respective information file; and
upon retrieval of the entire one respective portion from the first peer device, updating the content map corresponding to the retrieval thereof.
34. The method of claim 33 further comprising:
upon retrieval of all respective portions, from 1 to M, of file content, reconstructing the respective portions to assemble a requested information file having file content identical to that corresponding to the first HASH ID being associated therewith.
35. The method of claim 29 further comprising:
identifying the network addresses corresponding a first plurality of peer devices, from 1 to X, each of the first plurality of peer devices being identified as storing a respective information file, each having identical file content and having an identical first HASH ID being associated therewith;
36. The method of claim 35 further comprising:
before requesting a respective portion, creating a content map of the file content associated with the first HASH ID, said content map parceling the file content into respective portions from 1 to M, where M>X.
37. A system for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, the system comprising:
at least one CPU
memory
at least one interface for communicating with other devices in the peer-to-peer network;
the system being configured or designed to select a first information file;
the system being further configured or designed to applying a fingerprinting algorithm to the content of the selected file to thereby generate a first fingerprint ID relating to the content of the first information file; and
the system being further configured or designed to identify the first information file using the first fingerprint ID.
38. The system of claim 37 wherein the fingerprinting algorithm corresponds to an MD5 Message-Digest algorithm.
39. The system of claim 37 wherein the fingerprinting algorithm corresponds to a Secure Hash Algorithm (SHA1).
40. The system of claim 37 wherein the first information file is stored at a first peer device, and wherein the first information file has an associated first filename; and
wherein the system is further configured or designed to store the first filename and first fingerprint ID at the first peer device.
41. The system of claim 40 being further configured or designed to transmit the first filename and the first fingerprint ID to the database system for storage therein.
42. The system of claim 41 wherein the database system corresponds to a remote database system.
43. The system of claim 37 being further configured or designed to select a second information file having content identical to the first information file;
the system being further configured or designed to apply the fingerprinting algorithm to the content of the second information file to thereby generate an identical first fingerprint ID to that of the first information file; and
the system being further configured or designed to identify both the first and the second information file using the first unique fingerprint ID.
44. The system of claim 43 wherein the first information file is stored at a first peer device, and has a first associated filename, and wherein the second information file is stored at a second peer device, and has a has second associated filename;
the system being further configured or designed to store the first associated filename and first fingerprint ID associated with the first information file in the database system; and
the system being further configured or designed to store the second associated filename and first fingerprint ID associated with the second information file in the database system.
45. A system for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective fingerprint ID associated therewith relating to its file content, the system comprising:
at least one CPU
memory
at least one interface for communicating with other devices in the peer-to-peer network;
the system being configured or designed to transmit a first message to the database system, the first message including a search request for locating files in the network which match a first search string; and
the system being further configured or designed to receive a first response from the database system, the first response including first information relating to identified files stored in the network which match the first search string;
the first information further including an associated fingerprint ID for each identified file.
46. The system of claim 45 being further configured or designed to transmit a second message to the database system, the second message including a first fingerprint ID selected from the first information; and
the system being further configured or designed to receive a second response from the database system in response to the second message;
the second response including second information, the second information including at least one network address corresponding to at least one peer device that has been identified as having access to at least one file corresponding to the first fingerprint ID.
47. The system of claim 46 being further configured or designed to transmit a third message to a first peer device of the at least one peer devices, the third message corresponding to a request to retrieve a first file identified by the first fingerprint ID.
48. The system of claim 47 wherein the third message includes the first fingerprint ID.
49. The system of claim 47 being further configured or designed to tsb receive at least a portion of the file content of the first file from the first peer device in response to the third message.
50. A system for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective fingerprint ID associated therewith relating to its file content, the system comprising:
at least one CPU
memory
at least one interface for communicating with other devices in the peer-to-peer network;
the system being configured or designed to transmit a first message to a first peer device, the first message corresponding to a request to retrieve a first file identified by a first fingerprint ID, wherein the first message includes the first fingerprint ID, and wherein the first fingerprint ID is different than a filename associated with the first file; and
the system being further configured or designed to receive a first portion of the file content of the first file from the first peer device in response to the first message.
51. The system of claim 50 being further configured or designed to detect a failure in a file transfer process associated with the first peer device;
the system being further configured or designed to identify a second portion of the first file content which has not been received; and
the system being further configured or designed to transmit a second message to a second peer device, the second message corresponding to a request to retrieve the second portion of the first file content identified by the first fingerprint ID, wherein the second message includes the first fingerprint ID.
52. A system for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the system comprising:
at least one CPU
memory
at least one interface for communicating with other devices in the peer-to-peer network;
the system being configured or designed to receive file information from selected peer devices, the file information relating to shared files stored at each of the selected peer devices;
the file information including a filename for each shared file, and including a HASH ID for each shared file;
the system being further configured or designed to storing the file information in at least one data structure at the database system; and
the system being further configured or designed to identify a desired shared file in the network using its associated HASH ID.
53. The system of claim 52 being further configured or designed to identify an identity of a peer device using a selected HASH ID;
wherein the identified peer device has been identified as storing a file having an associated HASH ID which matches the selected HASH ID.
54. The system of claim 52 being further configured or designed to identify a network address of a first peer device using a selected HASH ID;
wherein the first peer device has been identified as storing a file having an associated HASH ID which matches the selected HASH ID.
55. A system for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the system comprising:
at least one CPU
memory
at least one interface for communicating with other devices in the peer-to-peer network;
the system being configured or designed to receive a first message from a first peer device, the first message including a search request for locating files in the network which match a first search string;
the system being further configured or designed to generate a first response to the first message, the response including a first list of file records relating to files stored in the network which match the first search string, wherein each file record includes an associated HASH ID and an associated filename; and
the system being further configured or designed to provide the first list of file records to the first peer device.
56. The system of claim 55 further being further configured or designed to exclude from the first list of file records duplicate records in which multiple file records have the same associated HASH ID and filename.
57. The system of claim 55 being further configured or designed to receive a second message from the first peer device in response to the first response, the second message including at least one HASH ID;
the system being further configured or designed to identify, using said at least one HASH ID, at least one network address corresponding to at least one peer device which has been identified as storing at least one file corresponding to the at least one HASH ID; and
the system being further configured or designed to provide, to the first peer device, a second response, the second response including address information which includes at least a portion of the at least one identified network addresses.
58. A system for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the system comprising:
at least one CPU
memory
at least one interface for communicating with other devices in the peer-to-peer network;
the system being configured or designed to identify a first network addresses corresponding to a first peer device which has been identified as storing a first information file associated with a first HASH ID;
the system being further configured or designed to identify a second network addresses corresponding to a second peer device which has been identified as storing a second information file associated with the first HASH ID;
the system being further configured or designed to transmit a first message to the first peer device request a first portion of file content of the first information file from the first peer device; and
the system being further configured or designed to transmit a second message to the second peer device request a second portion of file content of the second information file from the second peer device.
59. The system of claim 58 wherein the first and second messages each include the first HASH ID.
60. The system of claim 58 wherein the first and second messages are initiated at substantially a same time
61. The system of claim 58 wherein the request of the first portion of file content from the first peer device occurs concurrently with the request of the second portion of file content from the second peer device.
62. The system of claim 58 being further configured or designed to receive the first portion of file content from the first peer device;
the system being further configured or designed to receive the second portion of file content from the second peer device; and
the system being further configured or designed to generate a third information file which includes the first and second portion of file content, wherein the file content of the third information file is identical to the file content of the first information file.
63. The system of claim 58 being further configured or designed to detect a failure in a file transfer process associated with the first peer device;
the system being further configured or designed to identify a third network addresses corresponding to a third peer device which has been identified as storing a third information file associated with the first HASH ID;
the system being further configured or designed to transmit a third message to the third peer device, the third message corresponding to a request to retrieve the first portion of file content from the third information file.
64. The system of claim 58 wherein the first portion of file content corresponds to a first chunk of bytes 1 to N of the first information file; and
wherein the second portion of file content corresponds to a second chunk of bytes N+1 to 2N of the second information file.
65. A system for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the system comprising:
at least one CPU
memory
at least one interface for communicating with other devices in the peer-to-peer network;
the system being configured or designed to request from a first plurality of peer devices a respective portion of file content from a respective information file, each respective information file being identified as having identical file content and having an identical first HASH ID being associated therewith.
66. The system of claim 65 being further configured or designed to receive from at least a portion of the first plurality of peer devices respective portions of file content from the respective information file; and
the system being further configured or designed to reconstruct the respective portions of file content to assemble a requested information file having file content identical to that corresponding to the first HASH ID being associated therewith.
67. The system of claim 65 being further configured or designed to create, before request a respective portion, a content map of the file content associated with the first HASH ID, said content map parceling the file content into respective portions from 1 to M.
68. The system of claim 67 being further configured or designed to assign at least one respective portion, from 1 to M, to a first peer device of the first plurality of peer devices to request retrieval thereof.
69. The system of claim 68 being further configured or designed to receive from the first peer device the one respective portion, from 1 to M, of file content from the respective information file; and
the system being further configured or designed to update, upon retrieval of the entire one respective portion from the first peer device, the content map corresponding to the retrieval thereof.
70. The system of claim 69 being further configured or designed to reconstruct, upon retrieval of all respective portions, from 1 to M, of file content, the respective portions to assemble a requested information file having file content identical to that corresponding to the first HASH ID being associated therewith.
71. The system of claim 65 being further configured or designed to identify the network addresses corresponding a first plurality of peer devices, from 1 to X, each of the first plurality of peer devices being identified as storing a respective information file, each having identical file content and having an identical first HASH ID being associated therewith;
72. The system of claim 71 being further configured or designed to create, before request a respective portion, a content map of the file content associated with the first HASH ID, said content map parceling the file content into respective portions from 1 to M, where M>X.
73. A computer program product for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, the computer program product comprising:
a computer usable medium having computer readable code embodied therein, the computer readable code comprising:
computer code for selecting a first information file;
computer code for generating, using fingerprinting algorithm, a first fingerprint ID relating to the content of the first information file; and
computer code for identifying the first information file using the first fingerprint ID.
74. The computer program product of claim 73 wherein the fingerprinting algorithm corresponds to an MD5 Message-Digest algorithm.
75. The computer program product of claim 73 wherein the fingerprinting algorithm corresponds to a Secure Hash Algorithm (SHA1).
76. The computer program product of claim 73 wherein the first information file is stored at a first peer device, and wherein the first information file has an associated first filename, the computer program product comprising:
computer code for storing the first filename and first fingerprint ID at the first peer device.
77. The computer program product of claim 76 further comprising:
computer code for transmitting the first filename and the first fingerprint ID to the database system for storage therein.
78. The computer program product of claim 77 wherein the database system corresponds to a remote database system.
79. The computer program product of claim 73 further comprising:
computer code for selecting a second information file having content identical to the first information file;
computer code for applying the fingerprinting algorithm to the content of the second information file to thereby generate an identical first fingerprint ID to that of the first information file; and
computer code for identifying both the first and the second information file using the first unique fingerprint ID.
80. The computer program product of claim 79 wherein the first information file is stored at a first peer device, and has a first associated filename, and wherein the second information file is stored at a second peer device, and has a has second associated filename, the computer program product further comprising:
computer code for storing the first associated filename and first fingerprint ID associated with the first information file in the database system; and
computer code for storing the second associated filename and first fingerprint ID associated with the second information file in the database system.
81. A computer program product for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective fingerprint ID associated therewith relating to its file content, the computer program product comprising:
a computer usable medium having computer readable code embodied therein, the computer readable code comprising:
computer code for transmitting a first message to the database system, the first message including a search request for locating files in the network which match a first search string; and
computer code for receiving a first response from the database system, the first response including first information relating to identified files stored in the network which match the first search string;
the first information further including an associated fingerprint ID for each identified file.
82. A computer program product for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective fingerprint ID associated therewith relating to its file content, the computer program product comprising:
a computer usable medium having computer readable code embodied therein, the computer readable code comprising:
computer code for transmitting a first message to a first peer device, the first message corresponding to a request to retrieve a first file identified by a first fingerprint ID, wherein the first message includes the first fingerprint ID, and wherein the first fingerprint ID is different than a filename associated with the first file; and
computer code for receiving a first portion of the file content of the first file from the first peer device in response to the first message.
83. A computer program product for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the computer program product comprising:
a computer usable medium having computer readable code embodied therein, the computer readable code comprising:
computer code for receiving file information from selected peer devices, the file information relating to shared files stored at each of the selected peer devices;
the file information including a filename for each shared file, and including a HASH ID for each shared file;
computer code for storing the file information in at least one data structure at the database system; and
computer code for identifying a desired shared file in the network using its associated HASH ID.
84. A computer program product for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the computer program product comprising:
a computer usable medium having computer readable code embodied therein, the computer readable code comprising:
computer code for receiving a first message from a first peer device, the first message including a search request for locating files in the network which match a first search string;
computer code for generating a first response to the first message, the response including a first list of file records relating to files stored in the network which match the first search string, wherein each file record includes an associated HASH ID and an associated filename; and
computer code for providing the first list of file records to the first peer device.
85. A computer program product for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the computer program product comprising:
a computer usable medium having computer readable code embodied therein, the computer readable code comprising:
computer code for identifying a first network addresses corresponding to a first peer device which has been identified as storing a first information file associated with a first HASH ID;
computer code for identifying a second network addresses corresponding to a second peer device which has been identified as storing a second information file associated with the first HASH ID;
computer code for transmitting a first message to the first peer device requesting a first portion of file content of the first information file from the first peer device; and
computer code for transmitting a second message to the second peer device requesting a second portion of file content of the second information file from the second peer device.
86. A system for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the system comprising:
means for identifying a first network addresses corresponding to a first peer device which has been identified as storing a first information file associated with a first HASH ID;
means for identifying a second network addresses corresponding to a second peer device which has been identified as storing a second information file associated with the first HASH ID;
means for transmitting a first message to the first peer device requesting a first portion of file content of the first information file from the first peer device; and
means for transmitting a second message to the second peer device requesting a second portion of file content of the second information file from the second peer device.
87. A system for accessing information in a peer-to-peer network, the peer-to-peer network including a plurality of peer devices and a database system accessible by at least a portion of the peer devices, each of the peer devices being configured to store information files, and further being configured to share content from selected information files with at least a portion of the other peer devices in the network, wherein each shared file in the network has a respective HASH ID associated therewith relating to its file content, the HASH ID being different from a respective filename associated with each file, the system comprising:
means for receiving a first message from a first peer device, the first message including a search request for locating files in the network which match a first search string;
means for generating a first response to the first message, the response including a first list of file records relating to files stored in the network which match the first search string, wherein each file record includes an associated HASH ID and an associated filename; and
means for providing the first list of file records to the first peer device.
Priority Applications (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US09/883,064 US20020049760A1 (en) | 2000-06-16 | 2001-06-15 | Technique for accessing information in a peer-to-peer network |
| US11/364,465 US7660853B2 (en) | 2000-06-16 | 2006-02-28 | Hashing algorithm used for multiple files having identical content and fingerprint in a peer-to-peer network |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US21217700P | 2000-06-16 | 2000-06-16 | |
| US09/883,064 US20020049760A1 (en) | 2000-06-16 | 2001-06-15 | Technique for accessing information in a peer-to-peer network |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US11/364,465 Division US7660853B2 (en) | 2000-06-16 | 2006-02-28 | Hashing algorithm used for multiple files having identical content and fingerprint in a peer-to-peer network |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| US20020049760A1 true US20020049760A1 (en) | 2002-04-25 |
Family
ID=26906851
Family Applications (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US09/883,064 Abandoned US20020049760A1 (en) | 2000-06-16 | 2001-06-15 | Technique for accessing information in a peer-to-peer network |
| US11/364,465 Expired - Fee Related US7660853B2 (en) | 2000-06-16 | 2006-02-28 | Hashing algorithm used for multiple files having identical content and fingerprint in a peer-to-peer network |
Family Applications After (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US11/364,465 Expired - Fee Related US7660853B2 (en) | 2000-06-16 | 2006-02-28 | Hashing algorithm used for multiple files having identical content and fingerprint in a peer-to-peer network |
Country Status (1)
| Country | Link |
|---|---|
| US (2) | US20020049760A1 (en) |
Cited By (146)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20020103848A1 (en) * | 2000-11-29 | 2002-08-01 | Giacomini Peter Joseph | Distributed caching architecture for computer networks |
| US20020138552A1 (en) * | 2001-03-21 | 2002-09-26 | Debruine Timothy S. | Method and system for optimizing private network file transfers in a public peer-to-peer network |
| US20020138291A1 (en) * | 2001-03-21 | 2002-09-26 | Vijay Vaidyanathan | Digital file marketplace |
| US20020138576A1 (en) * | 2001-03-21 | 2002-09-26 | Schleicher Jorg Gregor | Method and system for generating revenue in a peer-to-peer file delivery network |
| US20020138744A1 (en) * | 2001-03-21 | 2002-09-26 | Schleicher Jorg Gregor | Method and system for providing a secure peer-to peer file delivery network |
| US20020156893A1 (en) * | 2001-01-22 | 2002-10-24 | Eric Pouyoul | System and method for dynamic, transparent migration of services |
| US20020178261A1 (en) * | 2001-05-25 | 2002-11-28 | Chang Frederic Robert | Method of improving the reliability of peer-to-peer network downloads |
| US20020198929A1 (en) * | 2001-06-25 | 2002-12-26 | International Business Machines Corporation | Method and apparatus to encourage client into a distributed peer to peer sharing technology |
| US20020198930A1 (en) * | 2001-06-25 | 2002-12-26 | International Business Machines Corporation | Method and apparatus for wide-spread distribution of electronic content in a peer to peer fashion |
| US20030009518A1 (en) * | 2001-07-06 | 2003-01-09 | Intel Corporation | Method and apparatus for peer-to-peer services |
| US20030009587A1 (en) * | 2001-07-06 | 2003-01-09 | Intel Corporation | Method and apparatus for peer-to-peer services |
| US20030009568A1 (en) * | 2001-06-26 | 2003-01-09 | Eastman Kodak Company | Method and system for managing images over a communication network |
| US20030009569A1 (en) * | 2001-06-26 | 2003-01-09 | Eastman Kodak Company | System and method for managing images over a communication network |
| US20030018709A1 (en) * | 2001-07-20 | 2003-01-23 | Audible Magic | Playlist generation method and apparatus |
| US20030018712A1 (en) * | 2001-07-06 | 2003-01-23 | Intel Corporation | Method and apparatus for peer-to-peer services |
| US20030037010A1 (en) * | 2001-04-05 | 2003-02-20 | Audible Magic, Inc. | Copyright detection and protection system and method |
| US20030037140A1 (en) * | 2001-08-17 | 2003-02-20 | Nokia Corp | Communication networks and methods of distributing information around the network |
| US20030061287A1 (en) * | 2001-09-26 | 2003-03-27 | Chee Yu | Method and system for delivering files in digital file marketplace |
| US20030110126A1 (en) * | 2001-12-10 | 2003-06-12 | Dunkeld Bryan C. | System & method for unique digital asset identification and transaction management |
| US20030131129A1 (en) * | 2002-01-10 | 2003-07-10 | International Business Machines Corporation | Method and system for peer to peer communication in a network environment |
| US20030135623A1 (en) * | 2001-10-23 | 2003-07-17 | Audible Magic, Inc. | Method and apparatus for cache promotion |
| US20030144995A1 (en) * | 2002-01-25 | 2003-07-31 | International Business Machines | Compressing index files in information retrieval |
| US20030158911A1 (en) * | 2002-02-19 | 2003-08-21 | Sun Microsystems, Inc. | Method and apparatus for an XML reporter |
| US20030177246A1 (en) * | 2002-03-15 | 2003-09-18 | International Business Machines Corporation | Centrally enhanced peer-to-peer resource sharing method and apparatus |
| US20030187852A1 (en) * | 2000-08-31 | 2003-10-02 | Tsuyoshi Abe | File transfer system, apparatus, method and computer readable medium storing file transfer program |
| US20030225796A1 (en) * | 2002-05-31 | 2003-12-04 | Hitachi, Ltd. | Method and apparatus for peer-to-peer file sharing |
| US20030233455A1 (en) * | 2002-06-14 | 2003-12-18 | Mike Leber | Distributed file sharing system |
| US20030236767A1 (en) * | 2002-06-19 | 2003-12-25 | Jun Akiyama | Information processing system and information processing method |
| US20040024877A1 (en) * | 2002-03-07 | 2004-02-05 | Benoit Celle | Network environments and location of resources therein |
| US20040172476A1 (en) * | 2003-02-28 | 2004-09-02 | Chapweske Justin F. | Parallel data transfer over multiple channels with data order prioritization |
| WO2004081794A1 (en) | 2003-03-10 | 2004-09-23 | Sharp Kabushiki Kaisha | Data processing device, data processing program, and recording medium |
| US20050004941A1 (en) * | 2001-11-16 | 2005-01-06 | Maria Kalker Antonius Adrianus Cornelis | Fingerprint database updating method, client and server |
| US20050021617A1 (en) * | 2001-09-06 | 2005-01-27 | Seffen Rusitschka | Scalable peer-to-peer network with a directory service |
| US20050044189A1 (en) * | 2000-02-17 | 2005-02-24 | Audible Magic Corporation. | Method and apparatus for identifying media content presented on a media playing device |
| US20050091595A1 (en) * | 2003-10-24 | 2005-04-28 | Microsoft Corporation | Group shared spaces |
| EP1533981A2 (en) * | 2003-11-19 | 2005-05-25 | Serenade Systems | Content distribution architecture |
| WO2005062152A1 (en) * | 2003-12-23 | 2005-07-07 | Arvato Storage Media Gmbh | Method for protecting a proprietary file |
| US20050216473A1 (en) * | 2004-03-25 | 2005-09-29 | Yoshio Aoyagi | P2P network system |
| US20050237949A1 (en) * | 2000-12-21 | 2005-10-27 | Addessi Vincent M | Dynamic connection structure for file transfer |
| US20050251807A1 (en) * | 2004-05-05 | 2005-11-10 | Martin Weel | System and method for sharing playlists |
| US20050251566A1 (en) * | 2004-05-05 | 2005-11-10 | Martin Weel | Playlist downloading for digital entertainment network |
| WO2005109251A2 (en) * | 2004-05-06 | 2005-11-17 | Oracle International Corporation | Web server for multi-version web documents |
| US20060010204A1 (en) * | 2004-07-06 | 2006-01-12 | Nokia Corporation | Peer-to-peer engine for object sharing in communication devices |
| JP2006018772A (en) * | 2004-07-05 | 2006-01-19 | Nippon Telegraph & Telephone West Corp | Agent control system and method |
| US20060041552A1 (en) * | 2004-08-18 | 2006-02-23 | Fujitsu Limited | Electronic information searching apparatus, method of searching electronic information and program for the same |
| EP1633111A1 (en) * | 2004-09-03 | 2006-03-08 | Microsoft Corporation | A system and method for distributed streaming of scalable media |
| US20060059061A1 (en) * | 2004-09-15 | 2006-03-16 | Oey Timothy S | Methods and systems for identifying and tracking potential property rights in software products |
| US20060064386A1 (en) * | 2004-09-20 | 2006-03-23 | Aaron Marking | Media on demand via peering |
| EP1643716A1 (en) * | 2004-09-03 | 2006-04-05 | Microsoft Corporation | A system and method for receiver driven streaming in a peer-to-peer network |
| US20060085385A1 (en) * | 2004-10-18 | 2006-04-20 | Richard Foster | Storage of content data in a peer-to-peer network |
| US20060107286A1 (en) * | 2004-11-12 | 2006-05-18 | Patrick Connor | System and method for the controlled on-demand distribution of content via a centralized server and a peer-to-peer network |
| US20060130037A1 (en) * | 2004-12-14 | 2006-06-15 | Microsoft Corporation | Method and system for downloading updates |
| US20060136526A1 (en) * | 2004-12-16 | 2006-06-22 | Childress Rhonda L | Rapid provisioning of a computer into a homogenized resource pool |
| US20060168318A1 (en) * | 2003-02-12 | 2006-07-27 | Adam Twiss | Methods and apparatus for traffic management in peer-to-peer networks |
| US20060179129A1 (en) * | 2005-02-10 | 2006-08-10 | Clayton Richard M | Hotcontent update for a target device |
| US20060184983A1 (en) * | 2005-02-16 | 2006-08-17 | Qwest Communications International Inc. | Wireless digital video recorder manager |
| US20060184968A1 (en) * | 2005-02-11 | 2006-08-17 | Clayton Richard M | Automatic content update for a target device |
| US20060184975A1 (en) * | 2005-02-16 | 2006-08-17 | Qwest Communications International Inc. | Wireless digital video recorder |
| US20060218275A1 (en) * | 2000-08-11 | 2006-09-28 | Napster, Inc. | System and method for searching peer-to-peer computer networks |
| US20060218598A1 (en) * | 2005-02-16 | 2006-09-28 | Qwest Communications International Inc. | Wireless digital video recorders - content sharing systems and methods |
| US20060259781A1 (en) * | 2005-04-29 | 2006-11-16 | Sony Corporation/Sony Electronics Inc. | Method and apparatus for detecting the falsification of metadata |
| US20060273152A1 (en) * | 2005-06-07 | 2006-12-07 | First Data Corporation | Dynamic aggregation of payment transactions |
| US20070016655A1 (en) * | 2002-03-15 | 2007-01-18 | International Business Machines Corporation | Secured and access controlled peer-to-peer resource sharing method and apparatus |
| EP1752925A1 (en) * | 2005-07-20 | 2007-02-14 | Siemens Aktiengesellschaft | Method and system for distribution of digital protected content data via a peer-to-peer data network |
| US20070136370A1 (en) * | 2005-12-09 | 2007-06-14 | Ophir Frieder | Peer-to-peer file sharing |
| US20070136297A1 (en) * | 2005-12-08 | 2007-06-14 | Microsoft Corporation | Peer-to-peer remediation |
| US20070177739A1 (en) * | 2006-01-27 | 2007-08-02 | Nec Laboratories America, Inc. | Method and Apparatus for Distributed Data Replication |
| US20070198726A1 (en) * | 2000-10-12 | 2007-08-23 | Peerapp Ltd. | Method and system for accelerating receipt of data in a client to client network |
| US20070237139A1 (en) * | 2006-04-11 | 2007-10-11 | Nokia Corporation | Node |
| US20070244894A1 (en) * | 2006-04-04 | 2007-10-18 | Xerox Corporation | Peer-to-peer file sharing system and method using downloadable data segments |
| US20070277202A1 (en) * | 2006-05-26 | 2007-11-29 | Frank Li-De Lin | System and method for content delivery |
| WO2008010802A1 (en) * | 2006-07-20 | 2008-01-24 | Thomson Licensing | Multi-party cooperative peer-to-peer video streaming |
| US20080034108A1 (en) * | 2000-12-29 | 2008-02-07 | Swarmcast, Inc. | Rate sensitive packet transfer mechanism over a peer-to-peer network |
| US20080062870A1 (en) * | 2006-09-12 | 2008-03-13 | Foleeo, Inc. | Hive-based peer-to-peer network |
| JP2008059398A (en) * | 2006-08-31 | 2008-03-13 | Brother Ind Ltd | Identification information allocation device, information processing method therefor, and program therefor |
| US20080086422A1 (en) * | 2005-02-04 | 2008-04-10 | Ricoh Company, Ltd. | Techniques for accessing controlled media objects |
| US20080168074A1 (en) * | 2005-01-21 | 2008-07-10 | Yuichi Inagaki | Data Transfer Device, Data Transfer Method, and Data Transfer Program |
| WO2008084348A1 (en) * | 2007-01-09 | 2008-07-17 | Nokia Corporation | Method for supporting file versioning in mbms file repair |
| US20080177910A1 (en) * | 2006-10-20 | 2008-07-24 | Canon Kabushiki Kaisha | Data reproducing apparatus, content management method, program, and storage medium |
| US20080228811A1 (en) * | 2006-11-21 | 2008-09-18 | International Business Machines Corporation | System and Method for Identifying Computer Users Having Files with Common Attributes |
| US20080256175A1 (en) * | 2007-04-16 | 2008-10-16 | Samsung Electronics Co., Ltd. | Method and apparatus for transmitting data in a peer-to-peer network |
| US20090012957A1 (en) * | 2004-05-07 | 2009-01-08 | Yves Villaret | System and method for searching strings of records |
| US20090030651A1 (en) * | 2007-07-27 | 2009-01-29 | Audible Magic Corporation | System for identifying content of digital data |
| US20090077160A1 (en) * | 2006-10-06 | 2009-03-19 | Concert Technology Corporation | System and method for providing media content selections |
| US20090116406A1 (en) * | 2005-07-20 | 2009-05-07 | Brother Kogyo Kabushiki Kaisha | Node device, memory medium saving computer program, information delivery system, and network participation method |
| US20090164535A1 (en) * | 2007-12-20 | 2009-06-25 | Microsoft Corporation | Disk seek optimized file system |
| US7562012B1 (en) | 2000-11-03 | 2009-07-14 | Audible Magic Corporation | Method and apparatus for creating a unique audio signature |
| US20090187978A1 (en) * | 2008-01-18 | 2009-07-23 | Yahoo! Inc. | Security and authentications in peer-to-peer networks |
| US20090220744A1 (en) * | 2008-02-28 | 2009-09-03 | Martinez Jr Arturo M | Method of making a vertical phase change memory (pcm) and a pcm device |
| US20090287841A1 (en) * | 2008-05-12 | 2009-11-19 | Swarmcast, Inc. | Live media delivery over a packet-based computer network |
| US20100010871A1 (en) * | 2004-12-31 | 2010-01-14 | Matthew Mengerink | Method and system to provide feedback data within a distributed e-commerce system |
| US20100023579A1 (en) * | 2008-06-18 | 2010-01-28 | Onion Networks, KK | Dynamic media bit rates based on enterprise data transfer policies |
| US20100023563A1 (en) * | 2008-07-23 | 2010-01-28 | Nvidia Corporation | Copying Files From One Directory To Another |
| US20100095009A1 (en) * | 2006-10-02 | 2010-04-15 | Nokia Corporation | Method, System, and Devices for Network Sharing or Searching Of Resources |
| US20100146145A1 (en) * | 2008-12-04 | 2010-06-10 | Swarmcast, Inc. | Adaptive playback rate with look-ahead |
| US7770168B1 (en) * | 2005-05-25 | 2010-08-03 | Landesk Software Limited | Systems and methods for distributing software using nodes within a network group |
| US20100205161A1 (en) * | 2009-02-10 | 2010-08-12 | Autodesk, Inc. | Transitive file copying |
| US20100306373A1 (en) * | 2009-06-01 | 2010-12-02 | Swarmcast, Inc. | Data retrieval based on bandwidth cost and delay |
| US7877438B2 (en) | 2001-07-20 | 2011-01-25 | Audible Magic Corporation | Method and apparatus for identifying new media content |
| US20110072075A1 (en) * | 2008-05-20 | 2011-03-24 | Eric Gautier | System and method for distributing a map of content available at multiple receivers |
| US20110099200A1 (en) * | 2009-10-28 | 2011-04-28 | Sun Microsystems, Inc. | Data sharing and recovery within a network of untrusted storage devices using data object fingerprinting |
| US20110099154A1 (en) * | 2009-10-22 | 2011-04-28 | Sun Microsystems, Inc. | Data Deduplication Method Using File System Constructs |
| US20110200224A1 (en) * | 2008-10-14 | 2011-08-18 | Koninklijke Philips Electronics N.V. | Content item identifier |
| US8082150B2 (en) | 2001-07-10 | 2011-12-20 | Audible Magic Corporation | Method and apparatus for identifying an unknown work |
| US8108485B1 (en) * | 2008-12-17 | 2012-01-31 | Sprint Communications Company L.P. | Method and system for operating a communication system |
| US20120054260A1 (en) * | 2010-08-26 | 2012-03-01 | Giraffic Technologies Ltd. | Asynchronous data streaming in a peer to peer network |
| US8130746B2 (en) | 2004-07-28 | 2012-03-06 | Audible Magic Corporation | System for distributing decoy content in a peer to peer network |
| US20120089648A1 (en) * | 2010-10-08 | 2012-04-12 | Kevin Michael Kozan | Crowd sourcing for file recognition |
| US8185612B1 (en) | 2010-12-30 | 2012-05-22 | Peerapp Ltd. | Methods and systems for caching data communications over computer networks |
| US8199651B1 (en) | 2009-03-16 | 2012-06-12 | Audible Magic Corporation | Method and system for modifying communication flows at a port level |
| US20120198051A1 (en) * | 2011-01-31 | 2012-08-02 | Telefonaktiebolaget L M Ericsson (Publ) | Adaptive Service Discovery in Structured Peer-to-Peer Overlay Networks and Method |
| US8332326B2 (en) * | 2003-02-01 | 2012-12-11 | Audible Magic Corporation | Method and apparatus to identify a work received by a processing system |
| US20120323966A1 (en) * | 2010-02-25 | 2012-12-20 | Rakuten, Inc. | Storage device, server device, storage system, database device, provision method of data, and program |
| US20130073671A1 (en) * | 2011-09-15 | 2013-03-21 | Vinayak Nagpal | Offloading traffic to device-to-device communications |
| US20130132527A1 (en) * | 2001-10-11 | 2013-05-23 | Oren Asher | Method and System for Peer-to-peer Image Streaming |
| US8543543B2 (en) * | 2011-09-13 | 2013-09-24 | Microsoft Corporation | Hash-based file comparison |
| US8543720B2 (en) | 2007-12-05 | 2013-09-24 | Google Inc. | Dynamic bit rate scaling |
| CN103336786A (en) * | 2013-06-05 | 2013-10-02 | 腾讯科技(深圳)有限公司 | Data processing method and device |
| US8635360B2 (en) | 2007-10-19 | 2014-01-21 | Google Inc. | Media playback point seeking using data range requests |
| US8634947B1 (en) * | 2009-10-21 | 2014-01-21 | Michael Merhej | System and method for identifying digital files |
| US8725740B2 (en) | 2008-03-24 | 2014-05-13 | Napo Enterprises, Llc | Active playlist having dynamic media item groups |
| US20150106437A1 (en) * | 2002-04-26 | 2015-04-16 | Sony Corporation | Centralized selection of peers as media data sources in a dispersed peer network |
| US9069635B2 (en) | 2012-04-09 | 2015-06-30 | Autodesk, Inc. | Process for compressing application deployments |
| US9081778B2 (en) | 2012-09-25 | 2015-07-14 | Audible Magic Corporation | Using digital fingerprints to associate data with a work |
| US9178946B2 (en) | 2004-05-05 | 2015-11-03 | Black Hills Media, Llc | Device discovery for digital entertainment network |
| US20150326667A1 (en) * | 2012-12-18 | 2015-11-12 | Microsoft Technology Licensing Llc | Peer-to-peer sharing of cloud-based content |
| US20150331865A1 (en) * | 2014-05-16 | 2015-11-19 | International Business Machines Corporation | Management of online community merge events |
| US9312827B2 (en) | 1998-01-22 | 2016-04-12 | Black Hills Media, Llc | Network enabled audio device and radio site |
| US20160173381A1 (en) * | 2014-12-12 | 2016-06-16 | Western Digital Technologies, Inc. | Nas off-loading of network traffic for shared files |
| US20160197977A1 (en) * | 2005-11-15 | 2016-07-07 | Ebay Inc. | Method and system to process navigation information |
| US20180013610A1 (en) * | 2015-08-12 | 2018-01-11 | Tencent Technology (Shenzhen) Company Limited | File delivery method, apparatus and system |
| US10142411B2 (en) | 2015-05-29 | 2018-11-27 | Microsoft Technology Licensing, Llc | Dynamic swarm segmentation |
| US10225340B2 (en) | 2010-12-30 | 2019-03-05 | Zephyrtel, Inc. | Optimizing data transmission between a first endpoint and a second endpoint in a computer network |
| US10313850B2 (en) * | 2017-07-24 | 2019-06-04 | Honeywell International Inc. | Systems and methods for upgrading firmware in multiple devices of a wireless fire detection system |
| US10331618B2 (en) * | 2012-10-16 | 2019-06-25 | International Business Machines Corporation | Software discovery with variable scan frequency |
| US10416979B2 (en) * | 2017-05-16 | 2019-09-17 | Red Hat, Inc. | Package installation on a host file system using a container |
| US20200366636A1 (en) * | 2017-05-16 | 2020-11-19 | Apple Inc. | Initiating a business messaging session |
| US20200374178A1 (en) * | 2008-03-27 | 2020-11-26 | Dropbox, Inc. | System and method for multi-tier synchronization |
| US20210019285A1 (en) * | 2019-07-16 | 2021-01-21 | Citrix Systems, Inc. | File download using deduplication techniques |
| US10931733B2 (en) * | 2017-08-24 | 2021-02-23 | Re Mago Ltd | Method, apparatus, and computer-readable medium for transmission of files over a web socket connection in a networked collaboration workspace |
| US11144952B2 (en) | 2013-11-13 | 2021-10-12 | Bi Science (2009) Ltd. | Behavioral content discovery |
| US20210342308A1 (en) * | 2020-04-30 | 2021-11-04 | Unity IPR ApS | System and method for performing context aware operating file system virtualization |
| US11418588B2 (en) * | 2020-09-29 | 2022-08-16 | EMC IP Holding Company LLC | Intelligent peer-to-peer container filesystem |
| US11734393B2 (en) | 2004-09-20 | 2023-08-22 | Warner Bros. Entertainment Inc. | Content distribution with renewable content protection |
| US11768954B2 (en) | 2020-06-16 | 2023-09-26 | Capital One Services, Llc | System, method and computer-accessible medium for capturing data changes |
| US11822522B2 (en) | 2020-01-31 | 2023-11-21 | EMC IP Holding Company LLC | Intelligent filesystem for container images |
Families Citing this family (61)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US7072982B2 (en) * | 2000-11-22 | 2006-07-04 | Microsoft Corporation | Universal naming scheme for peer to peer resources |
| US7594030B2 (en) * | 2000-11-22 | 2009-09-22 | Microsoft Corporation | Locator and tracking service for peer to peer resources |
| US7584261B1 (en) * | 2001-02-09 | 2009-09-01 | Microsoft Corporation | Distribution of binary executables and content from peer locations/machines |
| US8156223B2 (en) * | 2001-03-20 | 2012-04-10 | Microsoft Corporation | Distribution of binary executables and content from peer locations/machines |
| US8086738B2 (en) * | 2007-05-24 | 2011-12-27 | Russell Fish | Distributed means of organizing an arbitrarily large number of computers |
| EP1413119B1 (en) * | 2001-08-04 | 2006-05-17 | Kontiki, Inc. | Method and apparatus for facilitating distributed delivery of content across a computer network |
| EP1298506A1 (en) * | 2001-09-27 | 2003-04-02 | Siemens Aktiengesellschaft | Dynamic access to automation resources |
| CN1628462A (en) * | 2002-05-24 | 2005-06-15 | 奥伊科思研究所 | Method and system for managing audio-visual contents for distribution thereof in on-demand mode |
| US20040243536A1 (en) * | 2003-05-28 | 2004-12-02 | Integrated Data Control, Inc. | Information capturing, indexing, and authentication system |
| US7450524B2 (en) * | 2003-06-30 | 2008-11-11 | Kontiki, Inc. | Method and apparatus for determining network topology in a peer-to-peer network |
| US8370454B2 (en) * | 2003-06-30 | 2013-02-05 | International Business Machines Corporation | Retrieving a replica of an electronic document in a computer network |
| US7370089B2 (en) * | 2003-07-11 | 2008-05-06 | International Business Machines Corporation | Autonomic learning method to load balance output transfers of two peer nodes |
| US7715934B2 (en) | 2003-09-19 | 2010-05-11 | Macrovision Corporation | Identification of input files using reference files associated with nodes of a sparse binary tree |
| US20050203851A1 (en) * | 2003-10-25 | 2005-09-15 | Macrovision Corporation | Corruption and its deterrence in swarm downloads of protected files in a file sharing network |
| US7877810B2 (en) * | 2004-03-02 | 2011-01-25 | Rovi Solutions Corporation | System, method and client user interface for a copy protection service |
| WO2006090606A1 (en) * | 2005-02-24 | 2006-08-31 | Konica Minolta Holdings, Inc. | File or directory name generation method and device thereof |
| WO2006131909A2 (en) * | 2005-06-06 | 2006-12-14 | Netbarrage Ltd. | Method and system for monitoring and analyzing peer-to-peer users' activities over a data network |
| US7809943B2 (en) * | 2005-09-27 | 2010-10-05 | Rovi Solutions Corporation | Method and system for establishing trust in a peer-to-peer network |
| US8086722B2 (en) * | 2005-12-21 | 2011-12-27 | Rovi Solutions Corporation | Techniques for measuring peer-to-peer (P2P) networks |
| US7739239B1 (en) | 2005-12-29 | 2010-06-15 | Amazon Technologies, Inc. | Distributed storage system with support for distinct storage classes |
| US7702640B1 (en) * | 2005-12-29 | 2010-04-20 | Amazon Technologies, Inc. | Stratified unbalanced trees for indexing of data items within a computer system |
| US7716180B2 (en) | 2005-12-29 | 2010-05-11 | Amazon Technologies, Inc. | Distributed storage system with web services client interface |
| US20090132508A1 (en) * | 2006-05-02 | 2009-05-21 | Koninklijke Philips Electronics N.V. | System and method for associating a category label of one user with a category label defined by another user |
| US8041942B2 (en) * | 2006-09-05 | 2011-10-18 | Panasonic Corporation | Robust peer-to-peer networks and methods of use thereof |
| US7965655B2 (en) * | 2007-01-31 | 2011-06-21 | Hewlett-Packard Development Company, L.P. | Distributed network distance determination using a distributed hash table overlay network |
| US8131972B2 (en) * | 2007-09-19 | 2012-03-06 | International Business Machines Corporation | Method and apparatus for improving memory coalescing in a virtualized hardware environment |
| US8683458B2 (en) * | 2007-11-30 | 2014-03-25 | Red Hat, Inc. | Automatic full install upgrade of a network appliance |
| US20090150520A1 (en) * | 2007-12-07 | 2009-06-11 | David Garcia | Transmitting Assets In UPnP Networks To Remote Servers |
| US20090150570A1 (en) * | 2007-12-07 | 2009-06-11 | Bo Tao | Sharing Assets Between UPnP Networks |
| US20090150433A1 (en) * | 2007-12-07 | 2009-06-11 | Nokia Corporation | Method, Apparatus and Computer Program Product for Using Media Content as Awareness Cues |
| US20090150481A1 (en) * | 2007-12-08 | 2009-06-11 | David Garcia | Organizing And Publishing Assets In UPnP Networks |
| US20090150480A1 (en) * | 2007-12-08 | 2009-06-11 | Xiyuan Xia | Publishing Assets Of Dynamic Nature In UPnP Networks |
| US8589592B2 (en) * | 2007-12-11 | 2013-11-19 | Red Hat, Inc. | Efficient object distribution |
| US8209334B1 (en) * | 2007-12-28 | 2012-06-26 | Don Doerner | Method to direct data to a specific one of several repositories |
| US8296312B1 (en) * | 2008-01-14 | 2012-10-23 | Netapp, Inc. | Search and update of attributes in file systems |
| CN101547161B (en) | 2008-03-28 | 2012-09-26 | 阿里巴巴集团控股有限公司 | Folder transmission system, folder transmission device and folder transmission method |
| US8418164B2 (en) | 2008-05-29 | 2013-04-09 | Red Hat, Inc. | Image install of a network appliance |
| US9106668B2 (en) * | 2008-06-24 | 2015-08-11 | Azureus Software, Inc. | Distributed peer location in peer-to-peer file transfers |
| US8019882B2 (en) * | 2008-06-27 | 2011-09-13 | Microsoft Corporation | Content identification for peer-to-peer content retrieval |
| EP2338256A4 (en) * | 2008-09-17 | 2012-03-28 | Vuze Inc | Associative construction of multimedia subscriptions |
| US8935292B2 (en) * | 2008-10-15 | 2015-01-13 | Nokia Corporation | Method and apparatus for providing a media object |
| US8117343B2 (en) * | 2008-10-28 | 2012-02-14 | Hewlett-Packard Development Company, L.P. | Landmark chunking of landmarkless regions |
| US9792384B2 (en) * | 2009-02-26 | 2017-10-17 | Red Hat, Inc. | Remote retreival of data files |
| US8001273B2 (en) * | 2009-03-16 | 2011-08-16 | Hewlett-Packard Development Company, L.P. | Parallel processing of input data to locate landmarks for chunks |
| US8103769B1 (en) * | 2009-09-03 | 2012-01-24 | Amazon Technologies, Inc. | Dynamic isolation of shared resources |
| US8701193B1 (en) | 2009-09-30 | 2014-04-15 | Emc Corporation | Malware detection via signature indices |
| US8474038B1 (en) | 2009-09-30 | 2013-06-25 | Emc Corporation | Software inventory derivation |
| US8655844B1 (en) | 2009-09-30 | 2014-02-18 | Emc Corporation | File version tracking via signature indices |
| US8285842B1 (en) * | 2010-10-08 | 2012-10-09 | Google Inc. | Method and apparatus for dynamically specifying location collection and computation logic |
| US8538920B2 (en) * | 2011-08-08 | 2013-09-17 | Hewlett-Packard Development Company, L.P. | System and method for storage service |
| US9934229B2 (en) * | 2011-10-23 | 2018-04-03 | Microsoft Technology Licensing, Llc | Telemetry file hash and conflict detection |
| US9591337B1 (en) * | 2012-03-27 | 2017-03-07 | Cox Communications, Inc. | Point to point media on demand |
| US20130275618A1 (en) * | 2012-04-17 | 2013-10-17 | Alcatel-Lucent Bell Labs France | Method and apparatus for reducing content redundancy in content-centric networking |
| US9489193B2 (en) * | 2012-05-01 | 2016-11-08 | Sophos Limited | Method and system for providing software updates to local machines |
| US20150142742A1 (en) * | 2013-11-17 | 2015-05-21 | Zhen-Chao HONG | System and method for syncing local directories that enable file access across multiple devices |
| US9607002B2 (en) * | 2013-12-18 | 2017-03-28 | Intel Corporation | File retrieval from multiple storage locations |
| US9521128B2 (en) | 2014-11-07 | 2016-12-13 | Qualcomm Incorporated | Using a hash of a filename to control encoding/decoding of a digital file |
| US9811333B2 (en) | 2015-06-23 | 2017-11-07 | Microsoft Technology Licensing, Llc | Using a version-specific resource catalog for resource management |
| US20170206220A1 (en) * | 2016-01-20 | 2017-07-20 | 1 Digital Inc. | Method and apparatus for unified data access across networked computers |
| CN108153741B (en) * | 2018-01-12 | 2021-10-15 | 中译语通科技股份有限公司 | Multi-language-based efficient data acquisition method and computer program |
| CN109347968B (en) * | 2018-11-07 | 2021-09-24 | 网宿科技股份有限公司 | Method, equipment and system for downloading data blocks of resource file |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5978791A (en) * | 1995-04-11 | 1999-11-02 | Kinetech, Inc. | Data processing system using substantially unique identifiers to identify data items, whereby identical data items have the same identifiers |
| US6225888B1 (en) * | 1997-12-08 | 2001-05-01 | Nokia Telecommunications Oy | Authentication between communicating parties in a telecommunications network |
| US20020101989A1 (en) * | 1997-06-02 | 2002-08-01 | Vishal Markandey | Data protection system |
Family Cites Families (10)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5862335A (en) * | 1993-04-01 | 1999-01-19 | Intel Corp. | Method and apparatus for monitoring file transfers and logical connections in a computer network |
| US6185619B1 (en) * | 1996-12-09 | 2001-02-06 | Genuity Inc. | Method and apparatus for balancing the process load on network servers according to network and serve based policies |
| US6055568A (en) * | 1996-12-17 | 2000-04-25 | Intel Corporation | Method and apparatus for dynamically configuring a decentralized network of computers |
| US6098108A (en) * | 1997-07-02 | 2000-08-01 | Sitara Networks, Inc. | Distributed directory for enhanced network communication |
| US6374266B1 (en) * | 1998-07-28 | 2002-04-16 | Ralph Shnelvar | Method and apparatus for storing information in a data processing system |
| US6542964B1 (en) * | 1999-06-02 | 2003-04-01 | Blue Coat Systems | Cost-based optimization for content distribution using dynamic protocol selection and query resolution for cache server |
| US6339785B1 (en) * | 1999-11-24 | 2002-01-15 | Idan Feigenbaum | Multi-server file download |
| DE60139157D1 (en) * | 2000-01-14 | 2009-08-13 | Thinkstream Inc | DISTRIBUTED INFORMATION NETWORK WITH GLOBAL ACCESS |
| US20010037311A1 (en) * | 2000-02-18 | 2001-11-01 | Mccoy James | Efficient internet service cost recovery system and method |
| WO2002057917A2 (en) * | 2001-01-22 | 2002-07-25 | Sun Microsystems, Inc. | Peer-to-peer network computing platform |
-
2001
- 2001-06-15 US US09/883,064 patent/US20020049760A1/en not_active Abandoned
-
2006
- 2006-02-28 US US11/364,465 patent/US7660853B2/en not_active Expired - Fee Related
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5978791A (en) * | 1995-04-11 | 1999-11-02 | Kinetech, Inc. | Data processing system using substantially unique identifiers to identify data items, whereby identical data items have the same identifiers |
| US6415280B1 (en) * | 1995-04-11 | 2002-07-02 | Kinetech, Inc. | Identifying and requesting data in network using identifiers which are based on contents of data |
| US20020101989A1 (en) * | 1997-06-02 | 2002-08-01 | Vishal Markandey | Data protection system |
| US6225888B1 (en) * | 1997-12-08 | 2001-05-01 | Nokia Telecommunications Oy | Authentication between communicating parties in a telecommunications network |
Cited By (336)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US9549001B1 (en) | 1998-01-22 | 2017-01-17 | Black Hills Media, Llc | Method and device for sourcing and constructing a playlist |
| US9312827B2 (en) | 1998-01-22 | 2016-04-12 | Black Hills Media, Llc | Network enabled audio device and radio site |
| US9397627B2 (en) | 1998-01-22 | 2016-07-19 | Black Hills Media, Llc | Network-enabled audio device |
| US7500007B2 (en) | 2000-02-17 | 2009-03-03 | Audible Magic Corporation | Method and apparatus for identifying media content presented on a media playing device |
| US7917645B2 (en) | 2000-02-17 | 2011-03-29 | Audible Magic Corporation | Method and apparatus for identifying media content presented on a media playing device |
| US9049468B2 (en) | 2000-02-17 | 2015-06-02 | Audible Magic Corporation | Method and apparatus for identifying media content presented on a media playing device |
| US20050044189A1 (en) * | 2000-02-17 | 2005-02-24 | Audible Magic Corporation. | Method and apparatus for identifying media content presented on a media playing device |
| US10194187B2 (en) | 2000-02-17 | 2019-01-29 | Audible Magic Corporation | Method and apparatus for identifying media content presented on a media playing device |
| US20060218275A1 (en) * | 2000-08-11 | 2006-09-28 | Napster, Inc. | System and method for searching peer-to-peer computer networks |
| US7730178B2 (en) * | 2000-08-11 | 2010-06-01 | Napster, Inc. | System and method for searching peer-to-peer computer networks |
| US20060218274A1 (en) * | 2000-08-11 | 2006-09-28 | Napster, Inc. | System and method for optimizing access to information in peer-to-peer computer networks |
| US7454480B2 (en) * | 2000-08-11 | 2008-11-18 | Napster, Inc. | System and method for optimizing access to information in peer-to-peer computer networks |
| US7386574B2 (en) * | 2000-08-31 | 2008-06-10 | Nippon Telegraph And Telephone Corporation | File transfer system, apparatus, method and computer readable medium storing file transfer program |
| US20030187852A1 (en) * | 2000-08-31 | 2003-10-02 | Tsuyoshi Abe | File transfer system, apparatus, method and computer readable medium storing file transfer program |
| US8250149B2 (en) | 2000-10-12 | 2012-08-21 | Peerapp Ltd. | Method and system for accelerating receipt of data in a client to client network |
| US20070198726A1 (en) * | 2000-10-12 | 2007-08-23 | Peerapp Ltd. | Method and system for accelerating receipt of data in a client to client network |
| US8037162B2 (en) * | 2000-10-12 | 2011-10-11 | PeeApp Ltd. | Method and system for accelerating receipt of data in a client to client network |
| US7562012B1 (en) | 2000-11-03 | 2009-07-14 | Audible Magic Corporation | Method and apparatus for creating a unique audio signature |
| US8086445B2 (en) | 2000-11-03 | 2011-12-27 | Audible Magic Corporation | Method and apparatus for creating a unique audio signature |
| US20090240361A1 (en) * | 2000-11-03 | 2009-09-24 | Wold Erling H | Method and apparatus for creating a unique audio signature |
| US20020103848A1 (en) * | 2000-11-29 | 2002-08-01 | Giacomini Peter Joseph | Distributed caching architecture for computer networks |
| US7225219B2 (en) * | 2000-11-29 | 2007-05-29 | Broadspider Networks, Inc. | Distributed caching architecture for computer networks |
| US20050237949A1 (en) * | 2000-12-21 | 2005-10-27 | Addessi Vincent M | Dynamic connection structure for file transfer |
| US8694606B2 (en) | 2000-12-29 | 2014-04-08 | Google Inc. | Rate sensitive packet transfer mechanism over a peer-to-peer network |
| US8312107B2 (en) | 2000-12-29 | 2012-11-13 | Google Inc. | Rate sensitive packet transfer mechanism over a peer-to-peer network |
| US7831718B2 (en) | 2000-12-29 | 2010-11-09 | Swarmcast, Inc. | Rate sensitive packet transfer mechanism over a peer-to-peer network |
| US20080034108A1 (en) * | 2000-12-29 | 2008-02-07 | Swarmcast, Inc. | Rate sensitive packet transfer mechanism over a peer-to-peer network |
| US7165107B2 (en) * | 2001-01-22 | 2007-01-16 | Sun Microsystems, Inc. | System and method for dynamic, transparent migration of services |
| US20020156893A1 (en) * | 2001-01-22 | 2002-10-24 | Eric Pouyoul | System and method for dynamic, transparent migration of services |
| US20020138552A1 (en) * | 2001-03-21 | 2002-09-26 | Debruine Timothy S. | Method and system for optimizing private network file transfers in a public peer-to-peer network |
| US7047406B2 (en) * | 2001-03-21 | 2006-05-16 | Qurlo Holdings, Inc. | Method and system for providing a secure peer-to-peer file delivery network |
| US20020138291A1 (en) * | 2001-03-21 | 2002-09-26 | Vijay Vaidyanathan | Digital file marketplace |
| US20020138576A1 (en) * | 2001-03-21 | 2002-09-26 | Schleicher Jorg Gregor | Method and system for generating revenue in a peer-to-peer file delivery network |
| US20020138744A1 (en) * | 2001-03-21 | 2002-09-26 | Schleicher Jorg Gregor | Method and system for providing a secure peer-to peer file delivery network |
| US7653552B2 (en) | 2001-03-21 | 2010-01-26 | Qurio Holdings, Inc. | Digital file marketplace |
| US20090077673A1 (en) * | 2001-04-05 | 2009-03-19 | Schmelzer Richard A | Copyright detection and protection system and method |
| US9589141B2 (en) | 2001-04-05 | 2017-03-07 | Audible Magic Corporation | Copyright detection and protection system and method |
| US7707088B2 (en) | 2001-04-05 | 2010-04-27 | Audible Magic Corporation | Copyright detection and protection system and method |
| US20050154680A1 (en) * | 2001-04-05 | 2005-07-14 | Audible Magic Corporation | Copyright detection and protection system and method |
| US20050154678A1 (en) * | 2001-04-05 | 2005-07-14 | Audible Magic Corporation | Copyright detection and protection system and method |
| US8645279B2 (en) | 2001-04-05 | 2014-02-04 | Audible Magic Corporation | Copyright detection and protection system and method |
| US20090328236A1 (en) * | 2001-04-05 | 2009-12-31 | Schmelzer Richard A | Copyright detection and protection system and method |
| US7797249B2 (en) | 2001-04-05 | 2010-09-14 | Audible Magic Corporation | Copyright detection and protection system and method |
| US8484691B2 (en) | 2001-04-05 | 2013-07-09 | Audible Magic Corporation | Copyright detection and protection system and method |
| US7711652B2 (en) | 2001-04-05 | 2010-05-04 | Audible Magic Corporation | Copyright detection and protection system and method |
| US7363278B2 (en) | 2001-04-05 | 2008-04-22 | Audible Magic Corporation | Copyright detection and protection system and method |
| US7565327B2 (en) | 2001-04-05 | 2009-07-21 | Audible Magic Corporation | Copyright detection and protection system and method |
| US8775317B2 (en) | 2001-04-05 | 2014-07-08 | Audible Magic Corporation | Copyright detection and protection system and method |
| US20030037010A1 (en) * | 2001-04-05 | 2003-02-20 | Audible Magic, Inc. | Copyright detection and protection system and method |
| US20080141379A1 (en) * | 2001-04-05 | 2008-06-12 | Audible Magic Corporation | Copyright detection and protection system and method |
| US20080155116A1 (en) * | 2001-04-05 | 2008-06-26 | Audible Magic Corporation | Copyright detection and protection system and method |
| US20020178261A1 (en) * | 2001-05-25 | 2002-11-28 | Chang Frederic Robert | Method of improving the reliability of peer-to-peer network downloads |
| US7475132B2 (en) | 2001-05-25 | 2009-01-06 | At&T Knowledge Ventures, Lp | Method of improving the reliability of peer-to-peer network downloads |
| US7272645B2 (en) * | 2001-05-25 | 2007-09-18 | Sbc Technology Resources, Inc. | Method of improving the reliability of peer-to-peer network downloads |
| US20020198929A1 (en) * | 2001-06-25 | 2002-12-26 | International Business Machines Corporation | Method and apparatus to encourage client into a distributed peer to peer sharing technology |
| US20020198930A1 (en) * | 2001-06-25 | 2002-12-26 | International Business Machines Corporation | Method and apparatus for wide-spread distribution of electronic content in a peer to peer fashion |
| US20030009569A1 (en) * | 2001-06-26 | 2003-01-09 | Eastman Kodak Company | System and method for managing images over a communication network |
| US7124191B2 (en) * | 2001-06-26 | 2006-10-17 | Eastman Kodak Company | Method and system for managing images over a communication network |
| US7243153B2 (en) * | 2001-06-26 | 2007-07-10 | Eastman Kodak Company | System and method for managing images over a communication network |
| US20030009568A1 (en) * | 2001-06-26 | 2003-01-09 | Eastman Kodak Company | Method and system for managing images over a communication network |
| US7440994B2 (en) | 2001-07-06 | 2008-10-21 | Intel Corporation | Method and apparatus for peer-to-peer services to shift network traffic to allow for an efficient transfer of information between devices via prioritized list |
| US20030018712A1 (en) * | 2001-07-06 | 2003-01-23 | Intel Corporation | Method and apparatus for peer-to-peer services |
| US20030009518A1 (en) * | 2001-07-06 | 2003-01-09 | Intel Corporation | Method and apparatus for peer-to-peer services |
| US20090106355A1 (en) * | 2001-07-06 | 2009-04-23 | Harrow Ivan P | Method and Apparatus for Peer-to-Peer Services |
| US7546363B2 (en) | 2001-07-06 | 2009-06-09 | Intel Corporation | Adaptive route determination for peer-to-peer services |
| US20030009587A1 (en) * | 2001-07-06 | 2003-01-09 | Intel Corporation | Method and apparatus for peer-to-peer services |
| US7562112B2 (en) * | 2001-07-06 | 2009-07-14 | Intel Corporation | Method and apparatus for peer-to-peer services for efficient transfer of information between networks |
| US7921155B2 (en) | 2001-07-06 | 2011-04-05 | Intel Corporation | Method and apparatus for peer-to-peer services |
| US8082150B2 (en) | 2001-07-10 | 2011-12-20 | Audible Magic Corporation | Method and apparatus for identifying an unknown work |
| US10025841B2 (en) | 2001-07-20 | 2018-07-17 | Audible Magic, Inc. | Play list generation method and apparatus |
| US7877438B2 (en) | 2001-07-20 | 2011-01-25 | Audible Magic Corporation | Method and apparatus for identifying new media content |
| US20030018709A1 (en) * | 2001-07-20 | 2003-01-23 | Audible Magic | Playlist generation method and apparatus |
| US8972481B2 (en) | 2001-07-20 | 2015-03-03 | Audible Magic, Inc. | Playlist generation method and apparatus |
| US20030037140A1 (en) * | 2001-08-17 | 2003-02-20 | Nokia Corp | Communication networks and methods of distributing information around the network |
| US20050021617A1 (en) * | 2001-09-06 | 2005-01-27 | Seffen Rusitschka | Scalable peer-to-peer network with a directory service |
| US8266216B2 (en) * | 2001-09-06 | 2012-09-11 | Siemens Aktiengesellschaft | Scalable peer-to-peer network with a directory service |
| US8041803B2 (en) * | 2001-09-26 | 2011-10-18 | Qurio Holdings, Inc. | Method and system for delivering files in digital file marketplace |
| US20030061287A1 (en) * | 2001-09-26 | 2003-03-27 | Chee Yu | Method and system for delivering files in digital file marketplace |
| US8825812B2 (en) * | 2001-10-11 | 2014-09-02 | Oren Asher | Method and system for peer-to-peer image streaming |
| US20130132527A1 (en) * | 2001-10-11 | 2013-05-23 | Oren Asher | Method and System for Peer-to-peer Image Streaming |
| US20030135623A1 (en) * | 2001-10-23 | 2003-07-17 | Audible Magic, Inc. | Method and apparatus for cache promotion |
| US7523312B2 (en) * | 2001-11-16 | 2009-04-21 | Koninklijke Philips Electronics N.V. | Fingerprint database updating method, client and server |
| US20050004941A1 (en) * | 2001-11-16 | 2005-01-06 | Maria Kalker Antonius Adrianus Cornelis | Fingerprint database updating method, client and server |
| US20080215633A1 (en) * | 2001-12-10 | 2008-09-04 | Dunkeld Bryan C | Digital Media Asset Conversion System and Method |
| US20110302064A1 (en) * | 2001-12-10 | 2011-12-08 | Dunkeld Bryan C | System & Method for Introducing Digital Assets Into An Electronic Distribution System |
| US8606856B2 (en) * | 2001-12-10 | 2013-12-10 | Content Technologies, Llc | Digital media asset identification system and method |
| US8706636B2 (en) * | 2001-12-10 | 2014-04-22 | Content Technologies Llc | System and method for unique digital asset identification and transaction management |
| US8583556B2 (en) | 2001-12-10 | 2013-11-12 | Content Technologies, Llc | Method of providing a digital asset for distribution |
| US20110302661A1 (en) * | 2001-12-10 | 2011-12-08 | Dunkeld Bryan C | System & Method for Distributing Digital Assets Across a Network |
| US20030110126A1 (en) * | 2001-12-10 | 2003-06-12 | Dunkeld Bryan C. | System & method for unique digital asset identification and transaction management |
| US8626838B2 (en) * | 2001-12-10 | 2014-01-07 | Content Technologies, Llc | Digital media asset identification system and method |
| US20110302086A1 (en) * | 2001-12-10 | 2011-12-08 | Dunkeld Bryan C | System & Method for Unique Digital Asset Identification and Transaction Management |
| US20110302303A1 (en) * | 2001-12-10 | 2011-12-08 | Dunkeld Bryan C | System & Method for Managing Transfers of Digital Assets Over a Network |
| US20080215632A1 (en) * | 2001-12-10 | 2008-09-04 | Dunkeld Bryan C | Digital Media Asset Identification System and Method |
| US8001052B2 (en) * | 2001-12-10 | 2011-08-16 | Dunkeld Bryan C | System and method for unique digital asset identification and transaction management |
| US8200581B2 (en) * | 2001-12-10 | 2012-06-12 | Content Technologies, Llc | Digital media asset conversion system and method |
| US7117264B2 (en) * | 2002-01-10 | 2006-10-03 | International Business Machines Corporation | Method and system for peer to peer communication in a network environment |
| US20030131129A1 (en) * | 2002-01-10 | 2003-07-10 | International Business Machines Corporation | Method and system for peer to peer communication in a network environment |
| US20030144995A1 (en) * | 2002-01-25 | 2003-07-31 | International Business Machines | Compressing index files in information retrieval |
| US7028045B2 (en) * | 2002-01-25 | 2006-04-11 | International Business Machines Corporation | Compressing index files in information retrieval |
| US20030158911A1 (en) * | 2002-02-19 | 2003-08-21 | Sun Microsystems, Inc. | Method and apparatus for an XML reporter |
| US7249133B2 (en) * | 2002-02-19 | 2007-07-24 | Sun Microsystems, Inc. | Method and apparatus for a real time XML reporter |
| US8694957B2 (en) * | 2002-02-19 | 2014-04-08 | Oracle America, Inc. | Method and apparatus for an XML reporter |
| US20070271294A1 (en) * | 2002-02-19 | 2007-11-22 | Lou Edmund G | Method and apparatus for an xml reporter |
| US20040024877A1 (en) * | 2002-03-07 | 2004-02-05 | Benoit Celle | Network environments and location of resources therein |
| US8521876B2 (en) | 2002-03-15 | 2013-08-27 | International Business Machines Corporation | Centrally enhanced peer-to-peer resource sharing method and apparatus |
| US7130921B2 (en) * | 2002-03-15 | 2006-10-31 | International Business Machines Corporation | Centrally enhanced peer-to-peer resource sharing method and apparatus |
| US20070016655A1 (en) * | 2002-03-15 | 2007-01-18 | International Business Machines Corporation | Secured and access controlled peer-to-peer resource sharing method and apparatus |
| US20030177246A1 (en) * | 2002-03-15 | 2003-09-18 | International Business Machines Corporation | Centrally enhanced peer-to-peer resource sharing method and apparatus |
| US7475139B2 (en) * | 2002-03-15 | 2009-01-06 | International Business Machines Corporation | Secured and access controlled peer-to-peer resource sharing |
| US10506064B2 (en) | 2002-04-26 | 2019-12-10 | Sony Corporation | Centralized selection of peers as media data sources in a dispersed peer network |
| US9894176B2 (en) * | 2002-04-26 | 2018-02-13 | Sony Corporation | Centralized selection of peers as media data sources in a dispersed peer network |
| US20150106437A1 (en) * | 2002-04-26 | 2015-04-16 | Sony Corporation | Centralized selection of peers as media data sources in a dispersed peer network |
| US20030225796A1 (en) * | 2002-05-31 | 2003-12-04 | Hitachi, Ltd. | Method and apparatus for peer-to-peer file sharing |
| US7574488B2 (en) * | 2002-05-31 | 2009-08-11 | Hitachi, Ltd. | Method and apparatus for peer-to-peer file sharing |
| US20030233455A1 (en) * | 2002-06-14 | 2003-12-18 | Mike Leber | Distributed file sharing system |
| US20030236767A1 (en) * | 2002-06-19 | 2003-12-25 | Jun Akiyama | Information processing system and information processing method |
| US8332326B2 (en) * | 2003-02-01 | 2012-12-11 | Audible Magic Corporation | Method and apparatus to identify a work received by a processing system |
| US9787766B2 (en) * | 2003-02-12 | 2017-10-10 | Alcatel Lucent | Methods and apparatus for traffic management in peer-to-peer networks |
| US20060168318A1 (en) * | 2003-02-12 | 2006-07-27 | Adam Twiss | Methods and apparatus for traffic management in peer-to-peer networks |
| US8103786B2 (en) | 2003-02-28 | 2012-01-24 | Swarmcast Inc. (Bvi) | Parallel data transfer over multiple channels with data order prioritization |
| US7555559B2 (en) * | 2003-02-28 | 2009-06-30 | Onion Networks, KK | Parallel data transfer over multiple channels with data order prioritization |
| US20090327512A1 (en) * | 2003-02-28 | 2009-12-31 | Onion Networks, KK | Parallel data transfer over multiple channels with data order prioritization |
| US20040172476A1 (en) * | 2003-02-28 | 2004-09-02 | Chapweske Justin F. | Parallel data transfer over multiple channels with data order prioritization |
| EP1607868A4 (en) * | 2003-03-10 | 2009-04-22 | Sharp Kk | Data processing device, data processing program, and recording medium |
| EP1607868A1 (en) * | 2003-03-10 | 2005-12-21 | Sharp Kabushiki Kaisha | Data processing device, data processing program, and recording medium |
| WO2004081794A1 (en) | 2003-03-10 | 2004-09-23 | Sharp Kabushiki Kaisha | Data processing device, data processing program, and recording medium |
| US20050091595A1 (en) * | 2003-10-24 | 2005-04-28 | Microsoft Corporation | Group shared spaces |
| EP1533981A3 (en) * | 2003-11-19 | 2005-06-15 | Serenade Systems | Content distribution architecture |
| EP1533981A2 (en) * | 2003-11-19 | 2005-05-25 | Serenade Systems | Content distribution architecture |
| US7529770B2 (en) | 2003-12-23 | 2009-05-05 | Arvato Digital Services Gmbh | Method for protecting a proprietary file |
| US20070168330A1 (en) * | 2003-12-23 | 2007-07-19 | Arvato Storage Media Gmbh | Method for protecting a proprietary file |
| WO2005062152A1 (en) * | 2003-12-23 | 2005-07-07 | Arvato Storage Media Gmbh | Method for protecting a proprietary file |
| JP2005275937A (en) * | 2004-03-25 | 2005-10-06 | Fujitsu Ltd | P2p network system |
| US20050216473A1 (en) * | 2004-03-25 | 2005-09-29 | Yoshio Aoyagi | P2P network system |
| US9178946B2 (en) | 2004-05-05 | 2015-11-03 | Black Hills Media, Llc | Device discovery for digital entertainment network |
| US8458356B2 (en) | 2004-05-05 | 2013-06-04 | Black Hills Media | System and method for sharing playlists |
| US20050251807A1 (en) * | 2004-05-05 | 2005-11-10 | Martin Weel | System and method for sharing playlists |
| US8028038B2 (en) | 2004-05-05 | 2011-09-27 | Dryden Enterprises, Llc | Obtaining a playlist based on user profile matching |
| US9516370B1 (en) | 2004-05-05 | 2016-12-06 | Black Hills Media, Llc | Method, device, and system for directing a wireless speaker from a mobile phone to receive and render a playlist from a content server on the internet |
| US9554405B2 (en) | 2004-05-05 | 2017-01-24 | Black Hills Media, Llc | Wireless speaker for receiving from a mobile phone directions to receive and render a playlist from a content server on the internet |
| US20080209013A1 (en) * | 2004-05-05 | 2008-08-28 | Conpact, Inc. | System and method for sharing playlists |
| US8230099B2 (en) | 2004-05-05 | 2012-07-24 | Dryden Enterprises, Llc | System and method for sharing playlists |
| US20050251566A1 (en) * | 2004-05-05 | 2005-11-10 | Martin Weel | Playlist downloading for digital entertainment network |
| US9826046B2 (en) | 2004-05-05 | 2017-11-21 | Black Hills Media, Llc | Device discovery for digital entertainment network |
| US20080208379A1 (en) * | 2004-05-05 | 2008-08-28 | Conpact, Inc. | System and method for sharing playlists |
| US8028323B2 (en) | 2004-05-05 | 2011-09-27 | Dryden Enterprises, Llc | Method and system for employing a first device to direct a networked audio device to obtain a media item |
| US9584591B1 (en) | 2004-05-05 | 2017-02-28 | Black Hills Media, Llc | Method and device for sharing a playlist at a dedicated media player device |
| US20100223260A1 (en) * | 2004-05-06 | 2010-09-02 | Oracle International Corporation | Web Server for Multi-Version Web Documents |
| US7689601B2 (en) | 2004-05-06 | 2010-03-30 | Oracle International Corporation | Achieving web documents using unique document locators |
| WO2005109251A3 (en) * | 2004-05-06 | 2006-08-03 | Oracle Int Corp | Web server for multi-version web documents |
| US9672296B2 (en) | 2004-05-06 | 2017-06-06 | Oracle International Corporation | Web server for multi-version web documents |
| WO2005109251A2 (en) * | 2004-05-06 | 2005-11-17 | Oracle International Corporation | Web server for multi-version web documents |
| US20090012957A1 (en) * | 2004-05-07 | 2009-01-08 | Yves Villaret | System and method for searching strings of records |
| US7904429B2 (en) * | 2004-05-07 | 2011-03-08 | Robogroup T.E.K. Ltd | System and method for searching strings of records |
| JP4624734B2 (en) * | 2004-07-05 | 2011-02-02 | 西日本電信電話株式会社 | Agent control system and method |
| JP2006018772A (en) * | 2004-07-05 | 2006-01-19 | Nippon Telegraph & Telephone West Corp | Agent control system and method |
| US8316088B2 (en) | 2004-07-06 | 2012-11-20 | Nokia Corporation | Peer-to-peer engine for object sharing in communication devices |
| US20060010204A1 (en) * | 2004-07-06 | 2006-01-12 | Nokia Corporation | Peer-to-peer engine for object sharing in communication devices |
| US8130746B2 (en) | 2004-07-28 | 2012-03-06 | Audible Magic Corporation | System for distributing decoy content in a peer to peer network |
| US20060041552A1 (en) * | 2004-08-18 | 2006-02-23 | Fujitsu Limited | Electronic information searching apparatus, method of searching electronic information and program for the same |
| EP1643716A1 (en) * | 2004-09-03 | 2006-04-05 | Microsoft Corporation | A system and method for receiver driven streaming in a peer-to-peer network |
| KR101183430B1 (en) | 2004-09-03 | 2012-09-17 | 마이크로소프트 코포레이션 | A system and method for receiver driven streaming in a peer-to-peer network |
| US20060053209A1 (en) * | 2004-09-03 | 2006-03-09 | Microsoft Corporation | System and method for distributed streaming of scalable media |
| US7664109B2 (en) | 2004-09-03 | 2010-02-16 | Microsoft Corporation | System and method for distributed streaming of scalable media |
| EP1633111A1 (en) * | 2004-09-03 | 2006-03-08 | Microsoft Corporation | A system and method for distributed streaming of scalable media |
| US20060059061A1 (en) * | 2004-09-15 | 2006-03-16 | Oey Timothy S | Methods and systems for identifying and tracking potential property rights in software products |
| US8160947B2 (en) * | 2004-09-15 | 2012-04-17 | Adobe Systems Incorporated | Methods and systems for identifying and tracking potential property rights in software products |
| US20060064386A1 (en) * | 2004-09-20 | 2006-03-23 | Aaron Marking | Media on demand via peering |
| US11734393B2 (en) | 2004-09-20 | 2023-08-22 | Warner Bros. Entertainment Inc. | Content distribution with renewable content protection |
| US8880698B2 (en) | 2004-10-18 | 2014-11-04 | Sony United Kingdom Limited | Storage of content data in a peer-to-peer network |
| US20060085385A1 (en) * | 2004-10-18 | 2006-04-20 | Richard Foster | Storage of content data in a peer-to-peer network |
| US20060107286A1 (en) * | 2004-11-12 | 2006-05-18 | Patrick Connor | System and method for the controlled on-demand distribution of content via a centralized server and a peer-to-peer network |
| US8413198B2 (en) * | 2004-11-12 | 2013-04-02 | Intel Corporation | System and method for the controlled on-demand distribution of content via a centralized server and a peer-to-peer network |
| AU2005239708B2 (en) * | 2004-12-14 | 2010-07-01 | Microsoft Technology Licensing, Llc | Method and system for downloading updates |
| EP1672490A2 (en) | 2004-12-14 | 2006-06-21 | Microsoft Corporation | Method and system for downloading updates |
| US7716660B2 (en) | 2004-12-14 | 2010-05-11 | Microsoft Corporation | Method and system for downloading updates |
| EP1672490A3 (en) * | 2004-12-14 | 2008-01-23 | Microsoft Corporation | Method and system for downloading updates |
| US20060130037A1 (en) * | 2004-12-14 | 2006-06-15 | Microsoft Corporation | Method and system for downloading updates |
| US20060136526A1 (en) * | 2004-12-16 | 2006-06-22 | Childress Rhonda L | Rapid provisioning of a computer into a homogenized resource pool |
| US20100010871A1 (en) * | 2004-12-31 | 2010-01-14 | Matthew Mengerink | Method and system to provide feedback data within a distributed e-commerce system |
| US20080168074A1 (en) * | 2005-01-21 | 2008-07-10 | Yuichi Inagaki | Data Transfer Device, Data Transfer Method, and Data Transfer Program |
| US20080086422A1 (en) * | 2005-02-04 | 2008-04-10 | Ricoh Company, Ltd. | Techniques for accessing controlled media objects |
| US8843414B2 (en) * | 2005-02-04 | 2014-09-23 | Ricoh Company, Ltd. | Techniques for accessing controlled media objects |
| US20060179129A1 (en) * | 2005-02-10 | 2006-08-10 | Clayton Richard M | Hotcontent update for a target device |
| US20060184968A1 (en) * | 2005-02-11 | 2006-08-17 | Clayton Richard M | Automatic content update for a target device |
| US8613037B2 (en) | 2005-02-16 | 2013-12-17 | Qwest Communications International Inc. | Wireless digital video recorder manager |
| US20060184983A1 (en) * | 2005-02-16 | 2006-08-17 | Qwest Communications International Inc. | Wireless digital video recorder manager |
| US8407746B2 (en) * | 2005-02-16 | 2013-03-26 | Qwest Communications International Inc. | Wireless digital video recorders—content sharing systems and methods |
| US20060184975A1 (en) * | 2005-02-16 | 2006-08-17 | Qwest Communications International Inc. | Wireless digital video recorder |
| US20060218598A1 (en) * | 2005-02-16 | 2006-09-28 | Qwest Communications International Inc. | Wireless digital video recorders - content sharing systems and methods |
| US8590000B2 (en) | 2005-02-16 | 2013-11-19 | Qwest Communications International Inc. | Wireless digital video recorder |
| US20060259781A1 (en) * | 2005-04-29 | 2006-11-16 | Sony Corporation/Sony Electronics Inc. | Method and apparatus for detecting the falsification of metadata |
| US7770168B1 (en) * | 2005-05-25 | 2010-08-03 | Landesk Software Limited | Systems and methods for distributing software using nodes within a network group |
| US20060273152A1 (en) * | 2005-06-07 | 2006-12-07 | First Data Corporation | Dynamic aggregation of payment transactions |
| US7665658B2 (en) | 2005-06-07 | 2010-02-23 | First Data Corporation | Dynamic aggregation of payment transactions |
| US7782867B2 (en) * | 2005-07-20 | 2010-08-24 | Brother Kogyo Kabushiki Kaisha | Node device, memory medium saving computer program, information delivery system, and network participation method |
| EP1752925A1 (en) * | 2005-07-20 | 2007-02-14 | Siemens Aktiengesellschaft | Method and system for distribution of digital protected content data via a peer-to-peer data network |
| US20090116406A1 (en) * | 2005-07-20 | 2009-05-07 | Brother Kogyo Kabushiki Kaisha | Node device, memory medium saving computer program, information delivery system, and network participation method |
| US10419515B2 (en) * | 2005-11-15 | 2019-09-17 | Ebay Inc. | Method and system to process navigation information |
| US11303694B2 (en) * | 2005-11-15 | 2022-04-12 | Ebay Inc. | Method and system to process navigation information |
| US20200112601A1 (en) * | 2005-11-15 | 2020-04-09 | Ebay Inc. | Method and system to process navigation information |
| US20160197977A1 (en) * | 2005-11-15 | 2016-07-07 | Ebay Inc. | Method and system to process navigation information |
| US20070136297A1 (en) * | 2005-12-08 | 2007-06-14 | Microsoft Corporation | Peer-to-peer remediation |
| US20130007295A1 (en) * | 2005-12-08 | 2013-01-03 | Microsoft Corporation | Peer-to-peer remediation |
| US20130019238A1 (en) * | 2005-12-08 | 2013-01-17 | Microsoft Corporation | Peer-to-peer remediation |
| US8924577B2 (en) * | 2005-12-08 | 2014-12-30 | Microsoft Corporation | Peer-to-peer remediation |
| US8291093B2 (en) * | 2005-12-08 | 2012-10-16 | Microsoft Corporation | Peer-to-peer remediation |
| US20070136370A1 (en) * | 2005-12-09 | 2007-06-14 | Ophir Frieder | Peer-to-peer file sharing |
| US7779006B2 (en) * | 2005-12-09 | 2010-08-17 | Illinois Institute Of Technology | Peer-to-peer file sharing |
| US20070177739A1 (en) * | 2006-01-27 | 2007-08-02 | Nec Laboratories America, Inc. | Method and Apparatus for Distributed Data Replication |
| US20070244894A1 (en) * | 2006-04-04 | 2007-10-18 | Xerox Corporation | Peer-to-peer file sharing system and method using downloadable data segments |
| US7970835B2 (en) * | 2006-04-04 | 2011-06-28 | Xerox Corporation | Peer-to-peer file sharing system and method using downloadable data segments |
| US8693391B2 (en) | 2006-04-11 | 2014-04-08 | Nokia Corporation | Peer to peer services in a wireless communication network |
| US20070237139A1 (en) * | 2006-04-11 | 2007-10-11 | Nokia Corporation | Node |
| US7797722B2 (en) * | 2006-05-26 | 2010-09-14 | Sony Corporation | System and method for content delivery |
| US20130031163A1 (en) * | 2006-05-26 | 2013-01-31 | Sony Electronics Inc. | System and Method For Content Delivery |
| US8316406B2 (en) * | 2006-05-26 | 2012-11-20 | Sony Corporation | System and method for content delivery |
| US20070277202A1 (en) * | 2006-05-26 | 2007-11-29 | Frank Li-De Lin | System and method for content delivery |
| US8607290B2 (en) * | 2006-05-26 | 2013-12-10 | Sony Corporation | System and method for content delivery |
| US20100205644A1 (en) * | 2006-05-26 | 2010-08-12 | Frank Li-De Lin | System and method for content delivery |
| WO2008010802A1 (en) * | 2006-07-20 | 2008-01-24 | Thomson Licensing | Multi-party cooperative peer-to-peer video streaming |
| US8150966B2 (en) | 2006-07-20 | 2012-04-03 | Thomson Licensing | Multi-party cooperative peer-to-peer video streaming |
| JP2008059398A (en) * | 2006-08-31 | 2008-03-13 | Brother Ind Ltd | Identification information allocation device, information processing method therefor, and program therefor |
| US20080062870A1 (en) * | 2006-09-12 | 2008-03-13 | Foleeo, Inc. | Hive-based peer-to-peer network |
| US8103870B2 (en) * | 2006-09-12 | 2012-01-24 | Foleeo, Inc. | Hive-based peer-to-peer network |
| US20100095009A1 (en) * | 2006-10-02 | 2010-04-15 | Nokia Corporation | Method, System, and Devices for Network Sharing or Searching Of Resources |
| US9008634B2 (en) | 2006-10-06 | 2015-04-14 | Napo Enterprises, Llc | System and method for providing media content selections |
| US20090077160A1 (en) * | 2006-10-06 | 2009-03-19 | Concert Technology Corporation | System and method for providing media content selections |
| US8352654B2 (en) * | 2006-10-20 | 2013-01-08 | Canon Kabushiki Kaisha | Data reproducing apparatus, content management method, program, and storage medium |
| US20120206623A1 (en) * | 2006-10-20 | 2012-08-16 | Canon Kabushiki Kaisha | Data reproducing apparatus, content management method, program, and storage medium |
| US8185677B2 (en) * | 2006-10-20 | 2012-05-22 | Canon Kabushiki Kaisha | Data reproducing apparatus, content management method, program, and storage medium |
| US20110128391A1 (en) * | 2006-10-20 | 2011-06-02 | Canon Kabushiki Kaisha | Data reproducing apparatus, content management method, program, and storage medium |
| US8806097B2 (en) * | 2006-10-20 | 2014-08-12 | Canon Kabushiki Kaisha | Data reproducing apparatus, content management method, program, and storage medium |
| US20130107079A1 (en) * | 2006-10-20 | 2013-05-02 | Canon Kabushiki Kaisha | Data reproducing apparatus, content management method, program, and storage medium |
| US20080177910A1 (en) * | 2006-10-20 | 2008-07-24 | Canon Kabushiki Kaisha | Data reproducing apparatus, content management method, program, and storage medium |
| US8499109B2 (en) * | 2006-10-20 | 2013-07-30 | Canon Kabushiki Kaisha | Data reproducing apparatus, content management method, program, and storage medium |
| US7904621B2 (en) * | 2006-10-20 | 2011-03-08 | Canon Kabushiki Kaisha | Data reproducing apparatus, content management method, program, and storage medium |
| US20080228811A1 (en) * | 2006-11-21 | 2008-09-18 | International Business Machines Corporation | System and Method for Identifying Computer Users Having Files with Common Attributes |
| US8768893B2 (en) | 2006-11-21 | 2014-07-01 | International Business Machines Corporation | Identifying computer users having files with common attributes |
| US8086573B2 (en) * | 2006-11-21 | 2011-12-27 | International Business Machines Corporation | System and method for identifying computer users having files with common attributes |
| WO2008084348A1 (en) * | 2007-01-09 | 2008-07-17 | Nokia Corporation | Method for supporting file versioning in mbms file repair |
| US20080313191A1 (en) * | 2007-01-09 | 2008-12-18 | Nokia Corporation | Method for the support of file versioning in file repair |
| US8984096B2 (en) | 2007-04-16 | 2015-03-17 | Samsung Electronics Co., Ltd. | Method and apparatus for transmitting data in a peer-to-peer network |
| US8180853B2 (en) * | 2007-04-16 | 2012-05-15 | Samsung Electronics Co., Ltd. | Method and apparatus for transmitting data in a peer-to-peer network |
| US20080256175A1 (en) * | 2007-04-16 | 2008-10-16 | Samsung Electronics Co., Ltd. | Method and apparatus for transmitting data in a peer-to-peer network |
| US10181015B2 (en) | 2007-07-27 | 2019-01-15 | Audible Magic Corporation | System for identifying content of digital data |
| US8732858B2 (en) | 2007-07-27 | 2014-05-20 | Audible Magic Corporation | System for identifying content of digital data |
| US9785757B2 (en) | 2007-07-27 | 2017-10-10 | Audible Magic Corporation | System for identifying content of digital data |
| US20090030651A1 (en) * | 2007-07-27 | 2009-01-29 | Audible Magic Corporation | System for identifying content of digital data |
| US20090031326A1 (en) * | 2007-07-27 | 2009-01-29 | Audible Magic Corporation | System for identifying content of digital data |
| US8006314B2 (en) | 2007-07-27 | 2011-08-23 | Audible Magic Corporation | System for identifying content of digital data |
| US8112818B2 (en) | 2007-07-27 | 2012-02-07 | Audible Magic Corporation | System for identifying content of digital data |
| US9268921B2 (en) | 2007-07-27 | 2016-02-23 | Audible Magic Corporation | System for identifying content of digital data |
| US8635360B2 (en) | 2007-10-19 | 2014-01-21 | Google Inc. | Media playback point seeking using data range requests |
| US9608921B2 (en) | 2007-12-05 | 2017-03-28 | Google Inc. | Dynamic bit rate scaling |
| US8543720B2 (en) | 2007-12-05 | 2013-09-24 | Google Inc. | Dynamic bit rate scaling |
| US20090164535A1 (en) * | 2007-12-20 | 2009-06-25 | Microsoft Corporation | Disk seek optimized file system |
| US7836107B2 (en) * | 2007-12-20 | 2010-11-16 | Microsoft Corporation | Disk seek optimized file system |
| US20090187978A1 (en) * | 2008-01-18 | 2009-07-23 | Yahoo! Inc. | Security and authentications in peer-to-peer networks |
| US20090220744A1 (en) * | 2008-02-28 | 2009-09-03 | Martinez Jr Arturo M | Method of making a vertical phase change memory (pcm) and a pcm device |
| US8725740B2 (en) | 2008-03-24 | 2014-05-13 | Napo Enterprises, Llc | Active playlist having dynamic media item groups |
| US11921595B2 (en) | 2008-03-27 | 2024-03-05 | Dropbox, Inc. | System and method for multi-tier synchronization |
| US11461196B2 (en) * | 2008-03-27 | 2022-10-04 | Dropbox, Inc. | System and method for multi-tier synchronization |
| US20200374178A1 (en) * | 2008-03-27 | 2020-11-26 | Dropbox, Inc. | System and method for multi-tier synchronization |
| US20090287841A1 (en) * | 2008-05-12 | 2009-11-19 | Swarmcast, Inc. | Live media delivery over a packet-based computer network |
| US8661098B2 (en) | 2008-05-12 | 2014-02-25 | Google Inc. | Live media delivery over a packet-based computer network |
| US8301732B2 (en) | 2008-05-12 | 2012-10-30 | Google Inc. | Live media delivery over a packet-based computer network |
| US7979570B2 (en) | 2008-05-12 | 2011-07-12 | Swarmcast, Inc. | Live media delivery over a packet-based computer network |
| US8214427B2 (en) * | 2008-05-20 | 2012-07-03 | Thompson Licensing | System and method for distributing a map of content available at multiple receivers |
| US20110072075A1 (en) * | 2008-05-20 | 2011-03-24 | Eric Gautier | System and method for distributing a map of content available at multiple receivers |
| US8150992B2 (en) | 2008-06-18 | 2012-04-03 | Google Inc. | Dynamic media bit rates based on enterprise data transfer policies |
| US8880722B2 (en) | 2008-06-18 | 2014-11-04 | Google Inc. | Dynamic media bit rates based on enterprise data transfer policies |
| US20100023579A1 (en) * | 2008-06-18 | 2010-01-28 | Onion Networks, KK | Dynamic media bit rates based on enterprise data transfer policies |
| US8458355B1 (en) | 2008-06-18 | 2013-06-04 | Google Inc. | Dynamic media bit rates based on enterprise data transfer policies |
| US20100023563A1 (en) * | 2008-07-23 | 2010-01-28 | Nvidia Corporation | Copying Files From One Directory To Another |
| US8738580B2 (en) * | 2008-07-23 | 2014-05-27 | Nvidia Corporation | Copying files from one directory to another |
| US8831272B2 (en) * | 2008-10-14 | 2014-09-09 | Koninklijke Philips N.V. | Content item identifier |
| US20110200224A1 (en) * | 2008-10-14 | 2011-08-18 | Koninklijke Philips Electronics N.V. | Content item identifier |
| US8375140B2 (en) | 2008-12-04 | 2013-02-12 | Google Inc. | Adaptive playback rate with look-ahead |
| US9112938B2 (en) | 2008-12-04 | 2015-08-18 | Google Inc. | Adaptive playback with look-ahead |
| US20100146145A1 (en) * | 2008-12-04 | 2010-06-10 | Swarmcast, Inc. | Adaptive playback rate with look-ahead |
| US8108485B1 (en) * | 2008-12-17 | 2012-01-31 | Sprint Communications Company L.P. | Method and system for operating a communication system |
| US20100205161A1 (en) * | 2009-02-10 | 2010-08-12 | Autodesk, Inc. | Transitive file copying |
| US9727569B2 (en) * | 2009-02-10 | 2017-08-08 | Autodesk, Inc. | Transitive file copying |
| US8199651B1 (en) | 2009-03-16 | 2012-06-12 | Audible Magic Corporation | Method and system for modifying communication flows at a port level |
| US9948708B2 (en) * | 2009-06-01 | 2018-04-17 | Google Llc | Data retrieval based on bandwidth cost and delay |
| US20100306373A1 (en) * | 2009-06-01 | 2010-12-02 | Swarmcast, Inc. | Data retrieval based on bandwidth cost and delay |
| US8634947B1 (en) * | 2009-10-21 | 2014-01-21 | Michael Merhej | System and method for identifying digital files |
| US8458144B2 (en) * | 2009-10-22 | 2013-06-04 | Oracle America, Inc. | Data deduplication method using file system constructs |
| US20110099154A1 (en) * | 2009-10-22 | 2011-04-28 | Sun Microsystems, Inc. | Data Deduplication Method Using File System Constructs |
| US8121993B2 (en) * | 2009-10-28 | 2012-02-21 | Oracle America, Inc. | Data sharing and recovery within a network of untrusted storage devices using data object fingerprinting |
| US20110099200A1 (en) * | 2009-10-28 | 2011-04-28 | Sun Microsystems, Inc. | Data sharing and recovery within a network of untrusted storage devices using data object fingerprinting |
| US20120323966A1 (en) * | 2010-02-25 | 2012-12-20 | Rakuten, Inc. | Storage device, server device, storage system, database device, provision method of data, and program |
| US8407280B2 (en) * | 2010-08-26 | 2013-03-26 | Giraffic Technologies Ltd. | Asynchronous multi-source streaming |
| US20120054260A1 (en) * | 2010-08-26 | 2012-03-01 | Giraffic Technologies Ltd. | Asynchronous data streaming in a peer to peer network |
| US9626456B2 (en) * | 2010-10-08 | 2017-04-18 | Warner Bros. Entertainment Inc. | Crowd sourcing for file recognition |
| US11200299B2 (en) * | 2010-10-08 | 2021-12-14 | Warner Bros. Entertainment Inc. | Crowd sourcing for file recognition |
| US20170220776A1 (en) * | 2010-10-08 | 2017-08-03 | Warner Bros. Entertainment Inc. | Crowd sourcing for file recognition |
| US20120089648A1 (en) * | 2010-10-08 | 2012-04-12 | Kevin Michael Kozan | Crowd sourcing for file recognition |
| US10484497B2 (en) | 2010-12-30 | 2019-11-19 | Zephyrtel, Inc. | Methods and systems for caching data communications over computer networks |
| US8990354B2 (en) | 2010-12-30 | 2015-03-24 | Peerapp Ltd. | Methods and systems for caching data communications over computer networks |
| US10225340B2 (en) | 2010-12-30 | 2019-03-05 | Zephyrtel, Inc. | Optimizing data transmission between a first endpoint and a second endpoint in a computer network |
| US8185612B1 (en) | 2010-12-30 | 2012-05-22 | Peerapp Ltd. | Methods and systems for caching data communications over computer networks |
| US20120198051A1 (en) * | 2011-01-31 | 2012-08-02 | Telefonaktiebolaget L M Ericsson (Publ) | Adaptive Service Discovery in Structured Peer-to-Peer Overlay Networks and Method |
| US8499075B2 (en) * | 2011-01-31 | 2013-07-30 | Telefonaktiebolaget Lm Ericsson (Publ) | Adaptive service discovery in structured peer-to-peer overlay networks and method |
| US8543543B2 (en) * | 2011-09-13 | 2013-09-24 | Microsoft Corporation | Hash-based file comparison |
| US20130073671A1 (en) * | 2011-09-15 | 2013-03-21 | Vinayak Nagpal | Offloading traffic to device-to-device communications |
| US9069635B2 (en) | 2012-04-09 | 2015-06-30 | Autodesk, Inc. | Process for compressing application deployments |
| US9608824B2 (en) | 2012-09-25 | 2017-03-28 | Audible Magic Corporation | Using digital fingerprints to associate data with a work |
| US9081778B2 (en) | 2012-09-25 | 2015-07-14 | Audible Magic Corporation | Using digital fingerprints to associate data with a work |
| US10698952B2 (en) | 2012-09-25 | 2020-06-30 | Audible Magic Corporation | Using digital fingerprints to associate data with a work |
| US10331618B2 (en) * | 2012-10-16 | 2019-06-25 | International Business Machines Corporation | Software discovery with variable scan frequency |
| US11321274B2 (en) | 2012-10-16 | 2022-05-03 | International Business Machines Corporation | Software discovery with variable scan frequency |
| US10305986B2 (en) * | 2012-12-18 | 2019-05-28 | Microsoft Technology Licensing, Llc. | Peer-to-peer sharing of cloud-based content |
| US20150326667A1 (en) * | 2012-12-18 | 2015-11-12 | Microsoft Technology Licensing Llc | Peer-to-peer sharing of cloud-based content |
| CN103336786A (en) * | 2013-06-05 | 2013-10-02 | 腾讯科技(深圳)有限公司 | Data processing method and device |
| US11720915B2 (en) | 2013-11-13 | 2023-08-08 | Bi Science (2009) Ltd. | Behavioral content discovery |
| US11144952B2 (en) | 2013-11-13 | 2021-10-12 | Bi Science (2009) Ltd. | Behavioral content discovery |
| US20150331865A1 (en) * | 2014-05-16 | 2015-11-19 | International Business Machines Corporation | Management of online community merge events |
| US10332217B2 (en) * | 2014-05-16 | 2019-06-25 | International Business Machines Corporation | Management of online community merge events |
| US20160173381A1 (en) * | 2014-12-12 | 2016-06-16 | Western Digital Technologies, Inc. | Nas off-loading of network traffic for shared files |
| US9596183B2 (en) * | 2014-12-12 | 2017-03-14 | Western Digital Technologies, Inc. | NAS off-loading of network traffic for shared files |
| US10142411B2 (en) | 2015-05-29 | 2018-11-27 | Microsoft Technology Licensing, Llc | Dynamic swarm segmentation |
| US20180013610A1 (en) * | 2015-08-12 | 2018-01-11 | Tencent Technology (Shenzhen) Company Limited | File delivery method, apparatus and system |
| US10416979B2 (en) * | 2017-05-16 | 2019-09-17 | Red Hat, Inc. | Package installation on a host file system using a container |
| US20200366636A1 (en) * | 2017-05-16 | 2020-11-19 | Apple Inc. | Initiating a business messaging session |
| US10768919B2 (en) | 2017-05-16 | 2020-09-08 | Red Hat, Inc. | Package installation on a host file system using a container |
| US10313850B2 (en) * | 2017-07-24 | 2019-06-04 | Honeywell International Inc. | Systems and methods for upgrading firmware in multiple devices of a wireless fire detection system |
| US11089454B2 (en) * | 2017-07-24 | 2021-08-10 | Honeywell International Inc. | Systems and methods for upgrading firmware in multiple devices of a wireless fire detection system |
| US10931733B2 (en) * | 2017-08-24 | 2021-02-23 | Re Mago Ltd | Method, apparatus, and computer-readable medium for transmission of files over a web socket connection in a networked collaboration workspace |
| US20210019285A1 (en) * | 2019-07-16 | 2021-01-21 | Citrix Systems, Inc. | File download using deduplication techniques |
| US11822522B2 (en) | 2020-01-31 | 2023-11-21 | EMC IP Holding Company LLC | Intelligent filesystem for container images |
| US20210342308A1 (en) * | 2020-04-30 | 2021-11-04 | Unity IPR ApS | System and method for performing context aware operating file system virtualization |
| US11768954B2 (en) | 2020-06-16 | 2023-09-26 | Capital One Services, Llc | System, method and computer-accessible medium for capturing data changes |
| US11418588B2 (en) * | 2020-09-29 | 2022-08-16 | EMC IP Holding Company LLC | Intelligent peer-to-peer container filesystem |
Also Published As
| Publication number | Publication date |
|---|---|
| US20060149806A1 (en) | 2006-07-06 |
| US7660853B2 (en) | 2010-02-09 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US7660853B2 (en) | Hashing algorithm used for multiple files having identical content and fingerprint in a peer-to-peer network | |
| US11194719B2 (en) | Cache optimization | |
| EP3311544B1 (en) | Managing dynamic ip address assignments | |
| US7363347B2 (en) | Method and system for reestablishing connection information on a switch connected to plural servers in a computer network | |
| AU757667C (en) | Access to content addressable data over a network | |
| US7793112B2 (en) | Access to content addressable data over a network | |
| JP4154893B2 (en) | Network storage virtualization method | |
| US7720996B2 (en) | Internet protocol (IP) address proximity and application to peer provider location | |
| US7139747B1 (en) | System and method for distributed web crawling | |
| EP2091202B1 (en) | Data distributing method, data distributing system and correlative devices in edge network | |
| Dabek et al. | Wide-area cooperative storage with CFS | |
| US8606874B2 (en) | System and method of binding a client to a server | |
| US20030145093A1 (en) | System and method for peer-to-peer file exchange mechanism from multiple sources | |
| KR101063556B1 (en) | Methods, devices, and computer program products for uploading data in computing systems | |
| US20090182842A1 (en) | Method And System For Redirecting Data Requests In Peer-To-Peer Data Networks | |
| US20110099226A1 (en) | Method of requesting for location information of resources on network, user node and server for the same | |
| US8028019B2 (en) | Methods and apparatus for data transfer in networks using distributed file location indices | |
| US20090299937A1 (en) | Method and system for detecting and managing peer-to-peer traffic over a data network | |
| US7251670B1 (en) | Methods and apparatus for replicating a catalog in a content distribution network | |
| US20020078461A1 (en) | Incasting for downloading files on distributed networks | |
| WO2001093064A1 (en) | Dynamic peer-to-peer network content-serving | |
| Lee | Peer-To-Peer Bandwidth Efficient Keyword Search File Storage System | |
| Zhu et al. | Ndynamo: An ndnDHT-based distributed storage system over named data networking | |
| Kilchenmann | Design and implementation of a distributed object storage system on peer nodes | |
| Zijlmans et al. | Decrepol: A Decentralized Replication Policy for Web Documents |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment |
Owner name: YAGA, INC., CALIFORNIA Free format text: ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:SCOTT, ADRIAN C. H.;ARDRON, S. MITRA;REEL/FRAME:012458/0346;SIGNING DATES FROM 20011119 TO 20011130 |
|
| AS | Assignment |
Owner name: QURIO HOLDINGS, INC., NORTH CAROLINA Free format text: ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:YAGA, INC.;REEL/FRAME:016361/0555 Effective date: 20050311 |
|
| STCB | Information on status: application discontinuation |
Free format text: ABANDONED -- FAILURE TO RESPOND TO AN OFFICE ACTION |